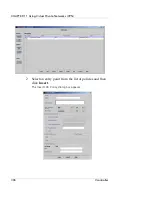
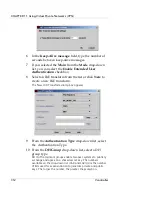
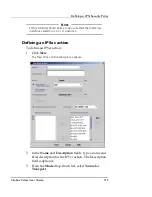
Authentication
Firebox Vclass User Guide
301
generally the Internet. Tunneling involves encrypting and
encapsulating data and protocol information within units
called IP packets. The “tunnel” is the path that the IP pack-
ets travel over the Internet. A tunnel is also defined by its
start and end points, the type of authentication and
encryption used, and the users allowed to use it. Tunneling
protocols provide the infrastructure of virtual private net-
working. These protocols govern how data transmission
occurs. The tunneling protocol used with the Firebox
Vclass appliances is the Internet Protocol Security (IPSec).
IPSec
The Internet Engineering Task Force (IETF) developed the
IPSec protocol suite as a security mechanism to ensure the
confidentiality and authenticity of IP packets. IPSec func-
tionality is based on modern cryptographic technologies,
providing extremely strong data authentication and pri-
vacy. IPSec makes secure communication possible over the
Internet, and IPSec standards allow interoperability
between VPN solutions.
A major benefit of IPSec is its interoperability. Instead of
specifying a proprietary method for performing authenti-
cation and encryption, it works with many systems and
standards.
IPSec includes two protocols that address issues of data
integrity and confidentiality when securing data across the
Internet. The AH (Authentication Header) protocol han-
dles data integrity, and the ESP (Encapsulated Security
Payload) protocol solves both data integrity and confiden-
tiality issues.
Authentication
An important aspect of security for a VPN is confirming
the identity of all communicating parties. Two ways of
Summary of Contents for Firebox V10
Page 1: ...WatchGuard Firebox Vclass User Guide Vcontroller 5 0 ...
Page 32: ...xxxii Vcontroller ...
Page 40: ...CHAPTER 1 Introduction 8 Vcontroller ...
Page 52: ...CHAPTER 2 Service and Support 20 Vcontroller ...
Page 70: ...CHAPTER 3 Getting Started 38 Vcontroller ...
Page 110: ...CHAPTER 4 Firebox Vclass Basics 78 Vcontroller ...
Page 190: ...CHAPTER 7 Using Account Manager 158 Vcontroller ...
Page 268: ...CHAPTER 9 Security Policy Examples 236 Vcontroller ...
Page 410: ...CHAPTER 14 Monitoring the Firebox Vclass 378 Vcontroller ...
Page 456: ...CHAPTER 18 Using the Diagnostics CLI Feature 424 Vcontroller ...