CHAPTER 11: Using Virtual Private Networks (VPN)
320
Vcontroller
N
OTE
You cannot choose
None
for both encryption and
authentication when creating an ESP transform.
9
Repeat this process to create additional ESP
transforms.
10
You can use the arrow keys to the left of the transforms
list to reorganize the transforms into the proper order
of application. Click the transform you want, and then
click the up or down arrow to move the transform.
The order of transforms represents the preference of the
encryption/authentication algorithm and lifetime of keys in this
security protocol. Only one of the transforms is chosen when
negotiation is complete. If none of the transforms are matched by
the peer appliance, the proposal is rejected.
11
When you are finished, click
Done
.
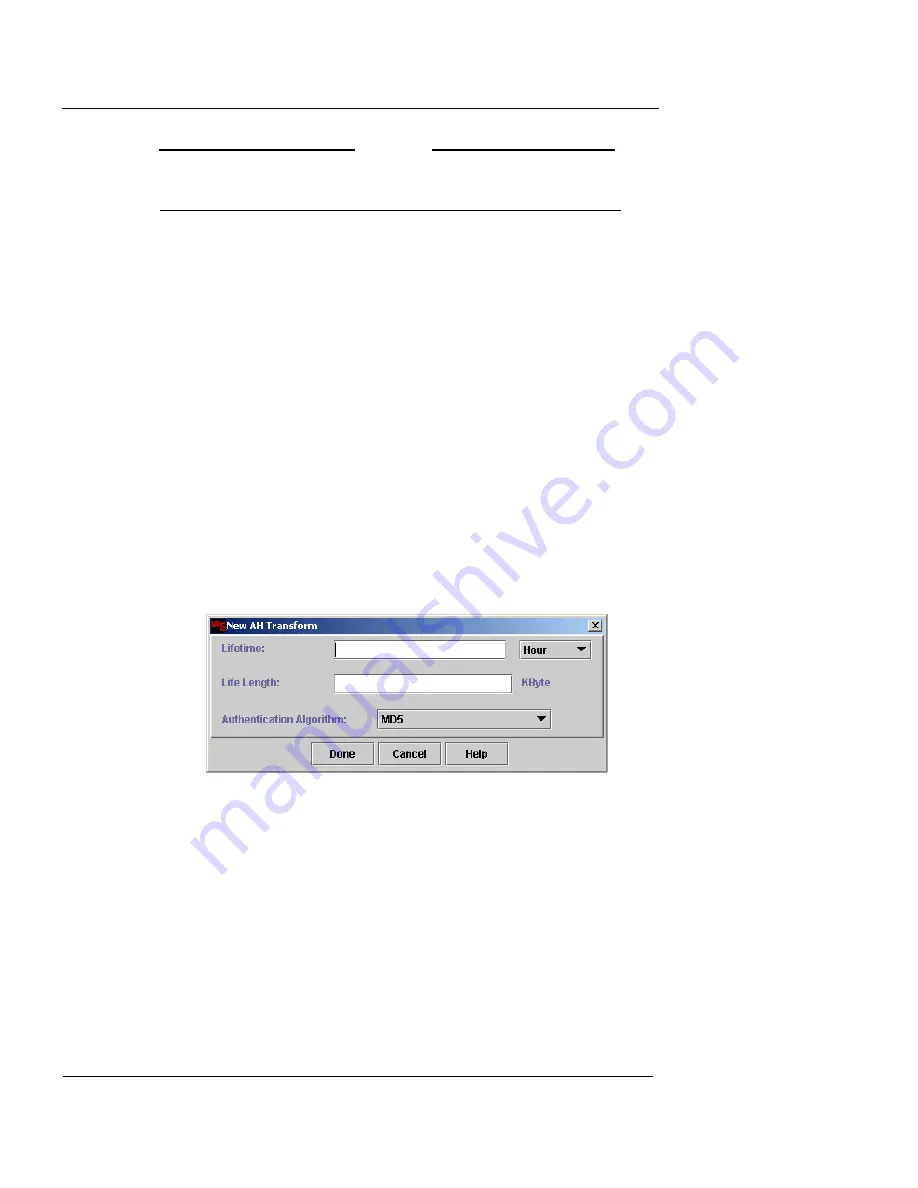
To define an AH transform:
1
Enable the
AH
checkbox.
2
Click
New
to open the
New AH Transform
dialog
box.
3
In the
Lifetime
field, type the number of hours or
minutes a key will be in effect.
If you type zero, this key will have an unlimited lifetime.
4
From the
Lifetime
drop-down list, select either
Hours
or
Minutes
.
5
Type the maximum number of kilobytes of traffic that
can be encrypted by this key before it expires in the
Life Length
field.
If you type zero, there is no maximum limit to the amount of
traffic encrypted by this key.
Summary of Contents for Firebox V10
Page 1: ...WatchGuard Firebox Vclass User Guide Vcontroller 5 0 ...
Page 32: ...xxxii Vcontroller ...
Page 40: ...CHAPTER 1 Introduction 8 Vcontroller ...
Page 52: ...CHAPTER 2 Service and Support 20 Vcontroller ...
Page 70: ...CHAPTER 3 Getting Started 38 Vcontroller ...
Page 110: ...CHAPTER 4 Firebox Vclass Basics 78 Vcontroller ...
Page 190: ...CHAPTER 7 Using Account Manager 158 Vcontroller ...
Page 268: ...CHAPTER 9 Security Policy Examples 236 Vcontroller ...
Page 410: ...CHAPTER 14 Monitoring the Firebox Vclass 378 Vcontroller ...
Page 456: ...CHAPTER 18 Using the Diagnostics CLI Feature 424 Vcontroller ...