CHAPTER 12: Creating a Remote User VPN Policy
340
Vcontroller
4
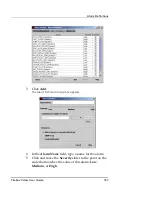
From the
Mode
drop-down list, select
Main
.
5
Select
Enable Extended User Authentication
.
6
Disable NAT Traversal, if necessary (NAT Traversal is
enabled by default). For more information, see “NAT
Traversal (UDP Encapsulation)” on page 303.
7
Select an IKE transform from the list or click
New
to
create a new IKE transform.
The New IKE Transform dialog box appears.
.
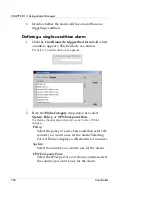
8
From the
Authentication Type
drop-down list, select
the Authentication Type.
9
From the
DH Group
drop-down list, select a DH
group type.
DH (Diffie-Helman) groups enable two peer systems to publicly
exchange and agree on a shared secret key. The numbers
available on the drop-down list (768 and 1024) are the number
of bits used for exponentiation to generate private and public
keys. The larger the number, the greater the protection.
10
From the
Encryption Algorithm
drop-down list,
select an encryption algorithm.
11
From the
Hash Algorithm
drop-down list, select a
hash algorithm.
12
In the
Lifetimes
field, type the number of hours or
minutes that the transform will remain active.
Summary of Contents for Firebox V10
Page 1: ...WatchGuard Firebox Vclass User Guide Vcontroller 5 0 ...
Page 32: ...xxxii Vcontroller ...
Page 40: ...CHAPTER 1 Introduction 8 Vcontroller ...
Page 52: ...CHAPTER 2 Service and Support 20 Vcontroller ...
Page 70: ...CHAPTER 3 Getting Started 38 Vcontroller ...
Page 110: ...CHAPTER 4 Firebox Vclass Basics 78 Vcontroller ...
Page 190: ...CHAPTER 7 Using Account Manager 158 Vcontroller ...
Page 268: ...CHAPTER 9 Security Policy Examples 236 Vcontroller ...
Page 410: ...CHAPTER 14 Monitoring the Firebox Vclass 378 Vcontroller ...
Page 456: ...CHAPTER 18 Using the Diagnostics CLI Feature 424 Vcontroller ...