Allowing Internal Hosts to Bypass User Authentication
User Guide
153
authenticate to get access to the Internet. No WebBlocker rules
apply to Web traffic originating from hosts on this list.
1
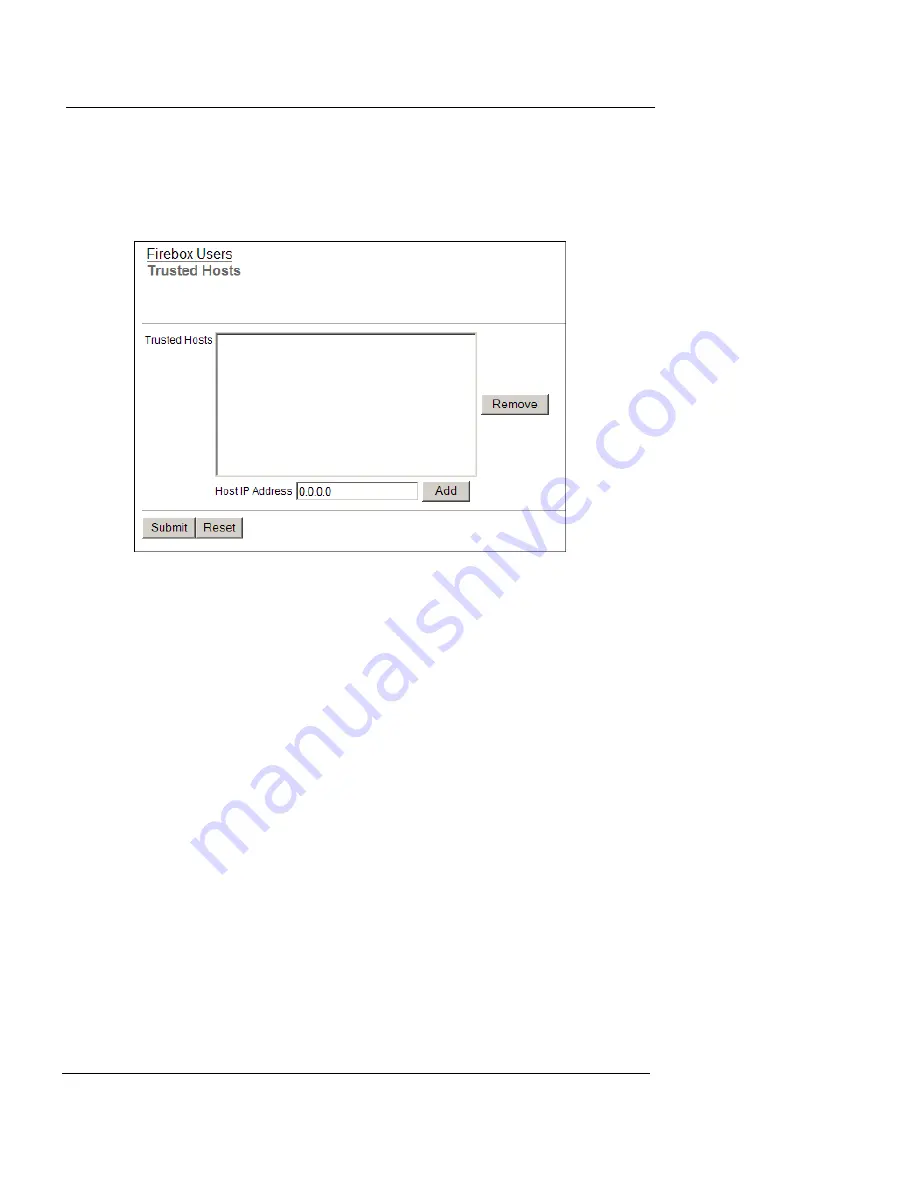
From the navigation bar, select
Firebox Users > Trusted Hosts
.
The Firebox Users Trusted Hosts page appears.
2
In the
Host IP Address
text box, type the IP address of the
computer on your trusted or optional network to allow to
browse the Internet without authentication restrictions.
3
Click
Add
.
Repeat step 2 for other trusted computers.
4
Click
Submit
.
To remove a computer from the list, select the address and click
Remove
.
Summary of Contents for Firebox X15
Page 14: ...xiv WatchGuard Firebox X Edge...
Page 42: ...Installing the Firebox X Edge 28 WatchGuard Firebox X Edge...
Page 72: ...Configuration and Management Basics 58 WatchGuard Firebox X Edge...
Page 146: ...Configuring Logging and System Time 132 WatchGuard Firebox X Edge...
Page 168: ...Managing Users and Groups 154 WatchGuard Firebox X Edge...
Page 204: ...Configuring Virtual Private Networks 190 WatchGuard Firebox X Edge...
Page 242: ...228 WatchGuard Firebox X Edge...
Page 249: ...Certifications and Notices User Guide 235 Taiwanese Notices...
Page 250: ...236 WatchGuard Firebox X Edge Declaration of Conformity...
















































