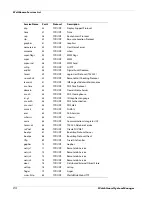
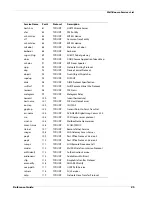
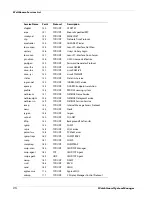
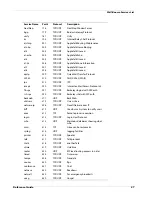
Searching for Blocked Sites
36
WatchGuard System Manager
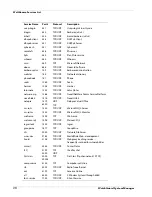
Motor Vehicles
• Car reviews, vehicle purchasing or sales tips, parts catalogs
• Auto trading, photos, discussion of vehicles including
motorcycles, boats, cars, trucks, and RVs
• Journals and magazines on vehicle modification, repair, and
customization
• Online automotive enthusiast clubs
Real Estate
• Home, apartment, and land listings
• Rental or relocation services
• Tips on buying or selling a home
• Real estate agents
• Home improvement
Shopping
• Internet malls and online auctions
• Department stores, retail stores, company catalogs online
• Online downloadable product warehouses; specialty items for sale
• Freebies, shareware, and software downloads
• Freebies or merchandise giveaways
Computers
Chat
Web-based chat
Computing &
Internet
• Reviews, information, computer buyer’s guides, computer parts
and accessories, and software
• Computer/software/Internet companies, industry news, and
magazines
• Sites that desing and/or maintain web pages including individual
web designers
• Design and/or maintain web pages including web designers
• Personal storage or backup
• Pay-to-surf sites
Hosting Sites
• Web sites that host business and individual web pages
Proxies &
Translators
• Remote proxies or anonymous surfing
• Peer-to-peer sharing
Web-based Email
• Web-based e-mail accounts
Downloads
• Downloadable (non-streaming) movie, video, or sound clips
• Downloadable PDA software, including themes and graphics
• Freeware and shareware sites
• Personal storage or backup
• Clip art, fonts, and animated gif pages
Ringtones/
Mobile Phone
Downloads
• Providers of mobile phone downloads, including:
- Ringtones,
- Logos
- Backgrounds
- Screensavers
- Games
Peer-to-Peer
• Peer-to-peer file sharing clients
• Peer-to-peer file sharing servers
Group
Category
Description of Content