User Guide
39
5
Types of Policies in Fireware
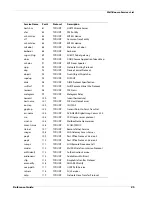
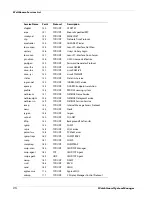
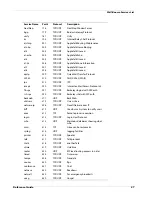
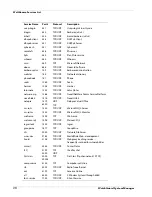
This chapter gives a list of the pre-defined policies included with your Firebox management software,
their protocols, and their ports. It also gives special information about circumstances that could have
an effect on the security of some policies.
In this chapter, policies are divided into two groups—policies that are controlled by a packet filter and
policies that are controlled by a proxy.
Packet Filter Policies
Packet filter policies examine the source and destination headers of each packet. Packets are allowed or
denied based on if the headers appear to come from and go to trusted
ad
dresses.
Any
Use an Any policy only to allow all traffic between two specified trusted IP or network addresses. An
Any policy opens a “hole” through the Firebox, and allows all traffic to flow freely between specified
hosts. We recommend that the Any policy be used only for traffic through a VPN.
The Any policy is different from other policies. For example, if you allow FTP only to a specified host, all
other FTP sessions to other hosts are denied by that policy (unless you have also configured other FTP
policies). The Any policy does not deny like other policies.
You also cannot use an Any policy unless specified IP addresses, network addresses, host aliases, group
names, or user names are used in the
From
or
To
lists. If not, the Any policy does not operate.
Characteristics
•
Internet Protocol(s): Any
•
Port Number(s): Any port