X8824r User’s Manual Version 1.0
51 / 102
9.4 IP
Filter
Click on the IP Filter link to view the IP filter configuration table. The
IP filter feature enables you to create rules that control the
forwarding of incoming and outgoing data between your LAN and the
Internet and within your LAN.
You can create IP filter rules to block attempts by certain computers
on your LAN to access certain types of data or Internet locations.
You can also block incoming access to computers on your LAN.
When you define an IP filter rule and enable the feature, you instruct
the ADSL/Ethernet router to examine data packets to determine
whether they meet criteria set forth in the rule. The criteria can
include the network or internet protocol the packet carries, the
direction in which it is traveling (for example, from the LAN to the
Internet or vice versa), the IP address of the sending computer, the
destination IP address, and other characteristics of the packet data.
If the packet matches the criteria established in a rule, the packet
can either be accepted (forwarded towards its destination), or denied
(discarded), depending on the action specified in the rule.
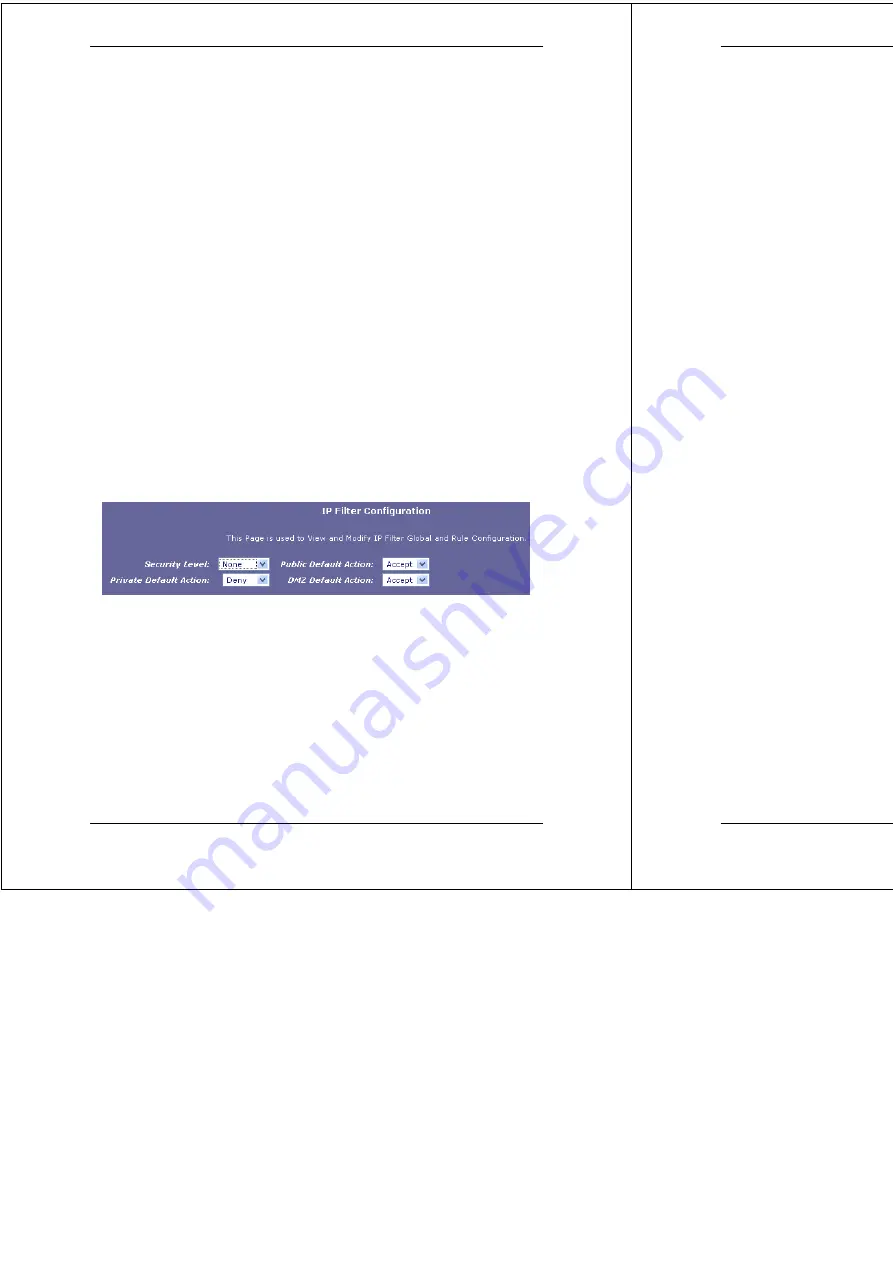
Security Level
: Select
None, Medium, Low,
or
High.
This setting determines which IP Filter rules take effect,
based on the security level specified in each rule. For
example, when
High
is selected, only those rules that are
assigned a security value of High will be in effect. The
same is true for the
Medium
and
Low
settings. When
None
is selected, IP Filtering is disabled.
Private/Public/DMZ Default Action
: This setting specifies
a default action to be taken (Accept or Deny) on private,
public, or DMZ-type device interfaces when they receive
packets that do not match any of the filtering rules. You can
specify a different default action for each interface type. A
X8824r User’s Manual Version 1.0
52 / 102
public
interface typically connects to the Internet. PPP,
EoA, and IPoA interfaces are typically public. Packets
received on a public interface are subject to the most
restrictive set of firewall protections defined in the software.
Typically, the global setting for public interfaces is Deny, so
that all accesses to your LAN initiated from external
computers are denied. A
private
interface connects to your
LAN, such as the Ethernet interface. Packets received on a
private interface are subject to a less restrictive set of
protections, because they originate within the network.
Typically, the global setting for private interfaces is Accept,
so that LAN computers have access to the ADSL/Ethernet
routers' Internet connection. The term
DMZ
(de-militarized
zone), in Internet networking terms, refers to computers
that are available for both public and in-network accesses
(such as a company's public Web server). Packets
received on a DMZ interface -- whether from a LAN or
external source -- are subject to a set of protections that is
in between public and private interfaces in terms of
restrictiveness. The global setting for DMZ-type interfaces
may be set to Deny so that all attempts to access these
servers are denied by default; the administrator may then
configure IP Filter rules to allow accesses of certain types.
9.5 Bridge
Filter
Click on the
Bridge Filter
link to view the bridge filter
configuration table. Bridge filter rules can be created to control
the forwarding of incoming and outgoing data between your
LAN and the Internet and within your LAN. Bridge filter rules
make decisions based on the structure of the "layer 2" data
packets (e.g., Ethernet packets) received on the device
interfaces, unlike IP filter rules, which are based on the
structure of "layer 3" (e.g., IP) packets.
When the bridge filtering feature is enabled, the bridge/router
examines each incoming layer 2 packet and compares it to the
bridge filter rules. The bridge filter rules specify which bits of the
packet are to be examined, and what criteria those bits must
meet in order to qualify as a match for the rule.
















































