Xerox D110/D125 Copier/Printer
セキュリティターゲット
- 28 –
Copyright
2012 by Fuji Xerox Co., Ltd
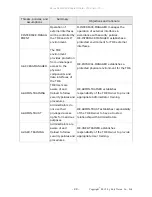
Threats, policies, and
assumptions
Summary
Objectives and rationale
Data may be
disclosed to
unauthorized
persons.
unauthorized disclosure.
O.USER.AUTHORIZED establishes user
identification and authentication as the
basis for authorization.
OE.USER.AUTHORIZED establishes
responsibility of the TOE Owner to
appropriately grant authorization
T.CONF.ALT
TSF Confidential
Data may be altered
by unauthorized
persons.
O.CONF.NO_ALT protects D.CONF from
unauthorized alteration.
O.USER.AUTHORIZED establishes user
identification and authentication as the
basis for authorization.
OE.USER.AUTHORIZED establishes
responsibility of the TOE Owner to
appropriately grant authorization
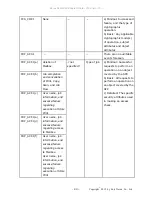
P.USER.AUTHORIZATI
ON
Users will be
authorized to use
the TOE.
O.USER.AUTHORIZED establishes user
authorization to use the TOE.identification
and authentication as the basis for
OE.USER.AUTHORIZED establishes
responsibility of the TOE Owner to
appropriately grant authorization
P.SOFTWARE.VERIFIC
ATION
Procedures will
exist to selfverify
executable code in
the TSF.
O.SOFTWARE.VERIFIED provides
procedures to self-verify executable code in
the TSF.
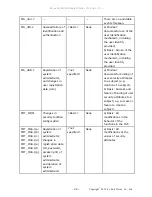
P.AUDIT.LOGGING
An audit trail of TOE
use and
security-relevant
events will be
created,
maintained,
protected, and
reviewed.
O.AUDIT.LOGGED creates and maintains a
log of TOE use and security-relevant events
and prevents unauthorized disclosure or
alteration.
OE.AUDIT.REVIEWED establishes
responsibility of the TOE Owner to ensure
that audit logs are appropriately reviewed.
O.AUDIT_STORAGE.PROTECTED protects
audit logs from unauthorized access,
deletion, and alteration for the TOE.
O.AUDIT_ACCESS.AUTHORIZED enables
the analysis of audit logs only by authorized
users to detect potential security violations
for the TOE.