13
XPLORE TECHNOLOGIES
Xplore has designed a multi-faceted Data Protection System for the iX104C5 to maximize reliability and con-
tinued performance when systems are deployed into formidable environments. For customers who conduct
business in the field or while mobile, system uptime and data integrity are imperative.
The Xplore Data Protection System offers:
EXTERNAL PROTECTION
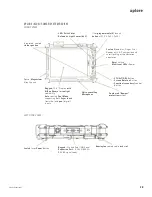
Dense magnesium chassis material, integrated “bumpering” and piston sealing systems provide external struc-
tural shock dampening and protection. This is the first point of defense against shock, drops and potential
ingress of water/dust/sand/dirt.
INTERNAL PROTECTION
Specialized, sealed and shock-isolated storage carrier houses the SSD drive(s). This unique carrier enclosure
uses multi-axis shock absorbing materials and piston gaskets to protect the installed drive(s) against potential
drop, shock and ingress damage. The SSD drive(s) is user-accessible (tool-less) for quick access, and a sec-
ondary latching/locking mechanism can be configured to limit user access in the field.
DATA REDUNDANCy
Utilizing Intel
®
’s mobile QM57 Express Chipset with on-board RAID controller, in combination with Intel
®
’s
Matrix Storage Manager software, and dual mSATA Solid State Drives (SSD) option, the iX104C5 supports
RAID (0,1) and JBOD configurations. The result is superior data integrity and redundancy which help minimize
downtime and maximize in-field productivity by keeping systems up and operating.
TECHNOLOGy LEVERAGE
The iX104C5 utilizes Intel
®
mSATA Solid State Drives in either a standard single-drive or optional dual-drive
(RAID) configuration. The RAID array and stability and performance of Intel
®
’s SSD technology provide cus-
tomers peace of mind in the event of a potential hard drive failure scenario. SSD and data encryption options
are also available to maximize data security. By combining the Trusted Platform Module (TPM 1.2)6 with the
Computrace
®
Application Agent or Intel
®
’s Anti-Theft Technology, data can be readily encrypted and remote
assets secured in the event of theft or loss. By implementing the Computrace
®
Application Agent or Intel
®
’s
Anti-Theft Technology, systems that are lost or stolen can effectively be given a “poison pill” when they are
connected to a network, thereby rendering them inoperable.
RUGGED DESIGN
TESTING/
CERTIFICATIONS
DATA PROTECTION
PROVEN RUGGED IN THE REAL WORLD