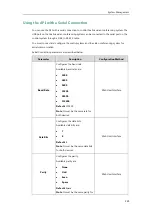
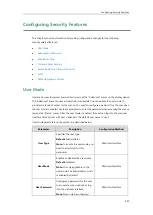
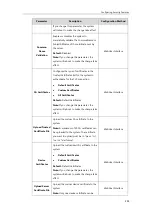
Configuring Security Features
253
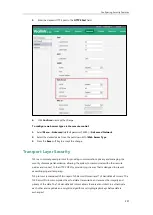
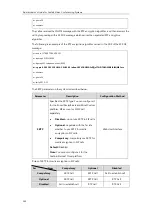
The following figure illustrates the TLS messages exchanged between the system and TLS server
to establish an encrypted communication channel:
Step1:
The system sends “Client Hello” message proposing SSL options.
Step2:
Server responds with “Server Hello” message selecting the SSL options, sends its public
key information in “Server Key Exchange” message and concludes its part of the negotiation
with “Server Hello Done” message.
Step3:
The system sends key session information (encrypted by server’s public key) in the
“Client Key Exchange” message.
Step4:
Server sends “Change Cipher Spec” message to activate the negotiated options for all
future messages it will send.
The system can encrypt SIP with TLS, which is called SIPS. When TLS is enabled for the SIP
account, the message of the SIP account will be encrypted after the successful TLS negotiation.
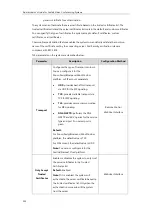
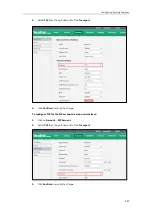
Certificates
The system can serve as a TLS client or a TLS server. The TLS requires the following security
certificates to perform the TLS handshake:
Trusted Certificate
: When the system requests a TLS connection with a server, the system
should verify the certificate sent by the server to decide whether it is trusted based on the
trusted certificates list. The system has 36 built-in trusted certificates. You can upload up to
10 custom certificates to the system. The format of the certificates must be *.pem, *.cer,
*.crt and *.der. For more information on 36 trusted certificates, refer to
on page
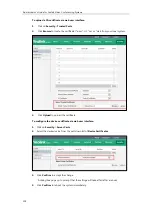
Server Certificate
: When clients request a TLS connection with the system, the system
sends the server certificate to the clients for authentication. The system has two types of
built-in server certificates: a unique server certificate and a generic server certificate. You
can only upload one server certificate to the system. The old server certificate will be
overridden by the new one. The format of the server certificate files must be *.pem and
*.cer.
-
A unique server certificate
: It is installed by default and is unique to a system
(based on the MAC address) and issued by the Yealink Certificate Authority (CA).
-
A generic server certificate
: It is installed by default and is issued by the Yealink
Certificate Authority (CA). Only if no unique certificate exists, the system may send a
Summary of Contents for VC120
Page 1: ......
Page 4: ...Administrator s Guide for Yealink Video Conferencing Systems ...
Page 16: ...Administrator s Guide for Yealink Video Conferencing Systems xvi ...
Page 48: ...Administrator s Guide for Yealink Video Conferencing Systems 32 ...
Page 114: ...Administrator s Guide for Yealink Video Conferencing Systems 98 ...
Page 180: ...Administrator s Guide for Yealink Video Conferencing Systems 164 ...
Page 242: ...Administrator s Guide for Yealink Video Conferencing Systems 226 ...
Page 284: ...Administrator s Guide for Yealink Video Conferencing Systems 268 ...
Page 292: ...Administrator s Guide for Yealink Video Conferencing Systems 276 ...
Page 310: ...Administrator s Guide for Yealink Video Conferencing Systems 294 ...
Page 316: ...Administrator s Guide for Yealink Video Conferencing Systems 300 ...