Configuring Policy Parameters
Configuring Web Filtering Settings
User Guide
|
51
Configuring Web Filtering Settings
The Gatekeeper devices can filter Web content. Over fifty Web filtering categories
are available.
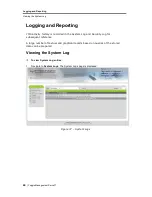
To configure Web filtering settings:
1. Navigate to the
Policy Editor
> Web Filtering
tab. The following page appears.
Figure 36 – Web-Filtering Policy
2. Select the
Activate Web Filtering
checkbox to turn on this feature.
3. Select the checkboxes to the left of one or more categories to specify what type
of content to block.
4. Click
Save
to save the current policy, or
Save As
to name a new policy.