Chapter 30 IDP
ZyWALL ATP Series User’s Guide
539
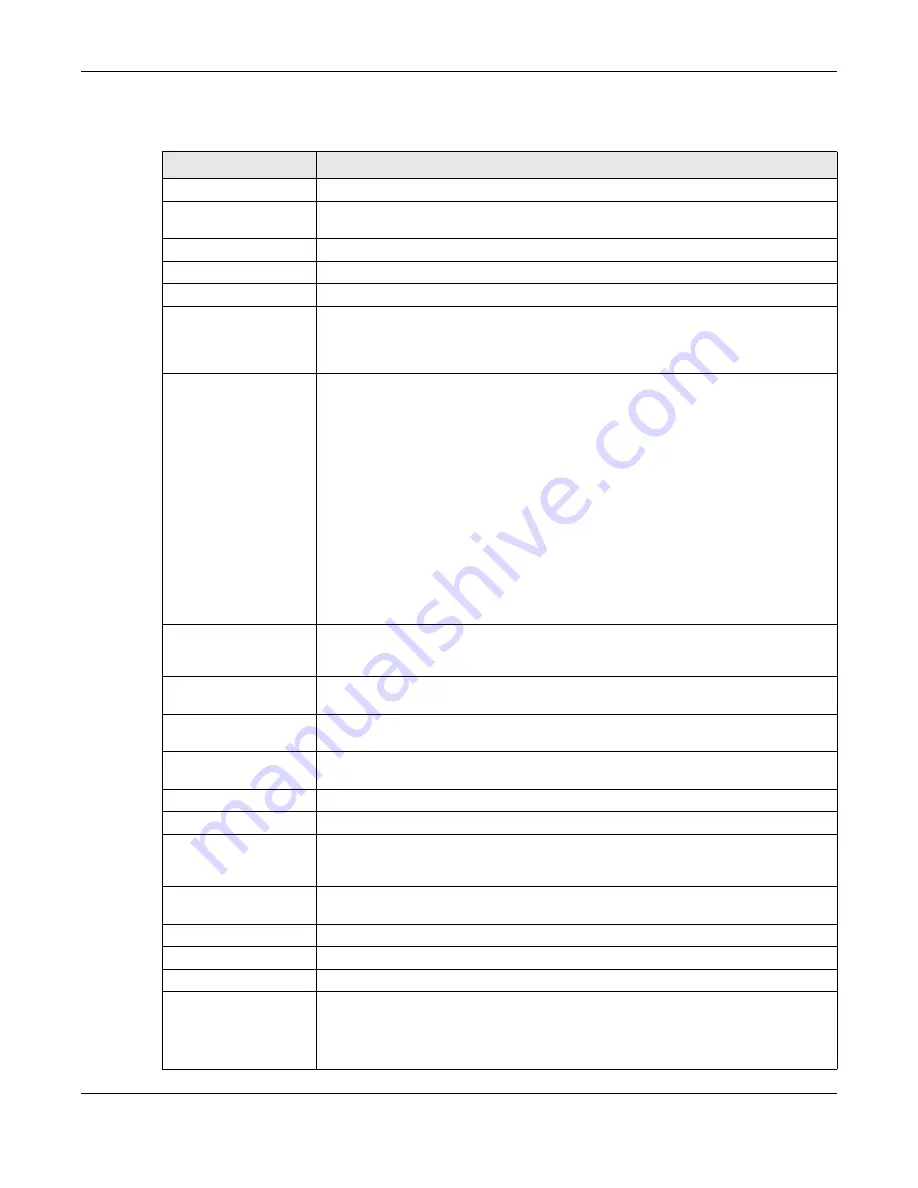
The following table describes the fields in this screen.
Table 217 Configuration > Security Service > IDP
LABEL
DESCRIPTION
General Settings
Enable
Select this check box to activate the IDP feature which detects and prevents malicious
or suspicious packets and responds instantaneously.
Query Signatures
Name
Type the name or part of the name of the signature(s) you want to find.
Signature ID
Type the ID or part of the ID of the signature(s) you want to find.
Search all custom
signatures
Select this check box to include signatures you created or imported in the
Custom
Signatures
screen in the search. You can search for specific signatures by name or ID. If
the name and ID fields are left blank, then all signatures are searched according to the
criteria you select.
Severity
Search for signatures by severity level(s). Hold down the [Ctrl] key if you want to make
multiple selections.
These are the severities as defined in the Zyxel Device. The number in brackets is the
number you use if using commands.
Severe
(5): These denote attacks that try to run arbitrary code or gain system privileges.
High
(4): These denote known serious vulnerabilities or attacks that are probably not
false alarms.
Medium
(3): These denote medium threats, access control attacks or attacks that could
be false alarms.
Low
(2): These denote mild threats or attacks that could be false alarms.
Very-Low
(1): These denote possible attacks caused by traffic such as Ping, trace route,
ICMP queries etc.
Classification Type
Search for signatures by attack type(s) (see
). Attack types are
known as policy types in the group view screen. Hold down the [Ctrl] key if you want to
make multiple selections.
Platform
Search for signatures created to prevent intrusions targeting specific operating
system(s). Hold down the [Ctrl] key if you want to make multiple selections.
Service
Search for signatures by IDP service group(s). See
for group
details. Hold down the [Ctrl] key if you want to make multiple selections.
Action
Search for signatures by the response the Zyxel Device takes when a packet matches a
signature.Hold down the [Ctrl] key if you want to make multiple selections.
Activation
Search for activated and/or inactivated signatures here.
Log
Search for signatures by log option here.
Query Result
The results are displayed in a table showing the
SID, Name, Severity, Classification Type,
Platform, Service, Log
, and
Action
criteria as selected in the search. Click the
SID
column
header to sort search results by signature ID.
Custom Signature Rules
Use this part of the screen to create, edit, delete or export (save to your computer)
custom signatures.
Add
Click this to create a new entry.
Edit
Select an entry and click this to be able to modify it.
Remove
Select an entry and click this to delete it.
Export
To save an entry or entries as a file on your computer, select them and click
Export
. Click
Save
in the file download dialog box and then select a location and name for the file.
Custom signatures must end with the ‘rules’ file name extension, for example,
MySig.rules.










































