Chapter 30 IDP
ZyWALL ATP Series User’s Guide
551
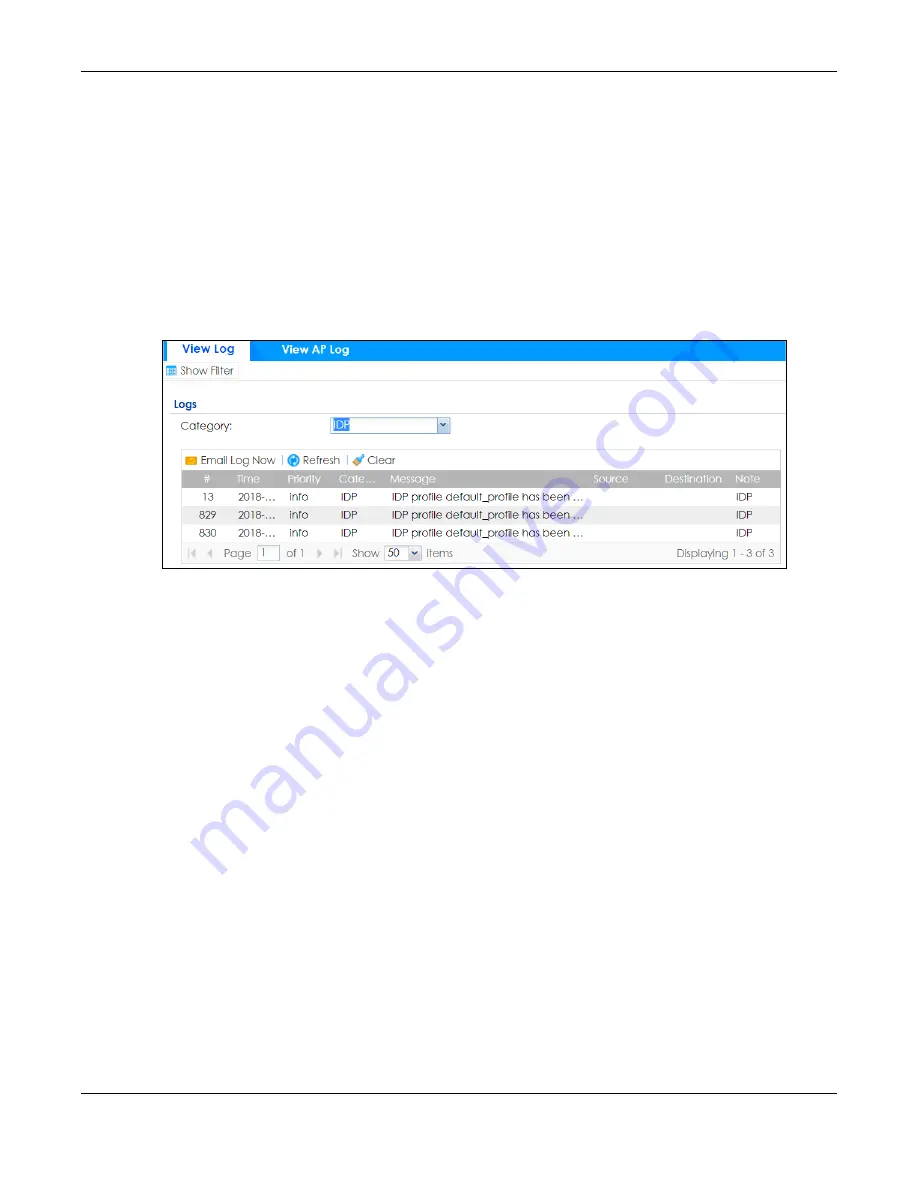
30.3.4 Verifying Custom Signatures
Configure the signature to create a log when traffic matches the signature. (You may also want to
configure an alert if it is for a serious attack and needs immediate attention.) After you apply the
signature to a zone, you can see if it works by checking the logs (
Monitor > Log
).
The
Priority
column shows
warn
for signatures that are configured to generate a log only. It shows
critical
for signatures that are configured to generate a log and alert. All IDP signatures come under the
IDP
category. The
Note
column displays
ACCESS FORWARD
when no action is configured for the signature. It
displays
ACCESS DENIED
if you configure the signature action to drop the packet. The destination port is
the service port (53 for DNS in this case) that the attack tries to exploit.
Figure 360
Custom Signature Log
30.4 IDP Technical Reference
This section contains some background information on IDP.
Host Intrusions
The goal of host-based intrusions is to infiltrate files on an individual computer or server in with the goal of
accessing confidential information or destroying information on a computer.
You must install a host IDP directly on the system being protected. It works closely with the operating
system, monitoring and intercepting system calls to the kernel or APIs in order to prevent attacks as well
as log them.
Disadvantages of host IDPs are that you have to install them on each device (that you want to protect)
in your network and due to the necessarily tight integration with the host operating system, future
operating system upgrades could cause problems.
Network Intrusions
Network-based intrusions have the goal of bringing down a network or networks by attacking
computer(s), switch(es), router(s) or modem(s). If a LAN switch is compromised for example, then the
whole LAN is compromised. Host-based intrusions may be used to cause network-based intrusions when
the goal of the host virus is to propagate attacks on the network, or attack computer/server operating






































