ZyWALL ATP Series User’s Guide
567
C
HAPTER
33
SSL Inspection
33.1 Overview
Secure Socket Layer (SSL) traffic, such as https://www.google.com/HTTPS, FTPs, POP3s, SMTPs, etc. is
encrypted, and cannot be inspected using Security Service profiles such as App Patrol, Content Filter,
Intrusion, Detection and Prevention (IDP), or Anti-Malware. The Zyxel Device uses SSL Inspection to
decrypt SSL traffic, sends it to the Security Service engines for inspection, then encrypts traffic that
passes inspection and forwards it to the destination server, such as Google.
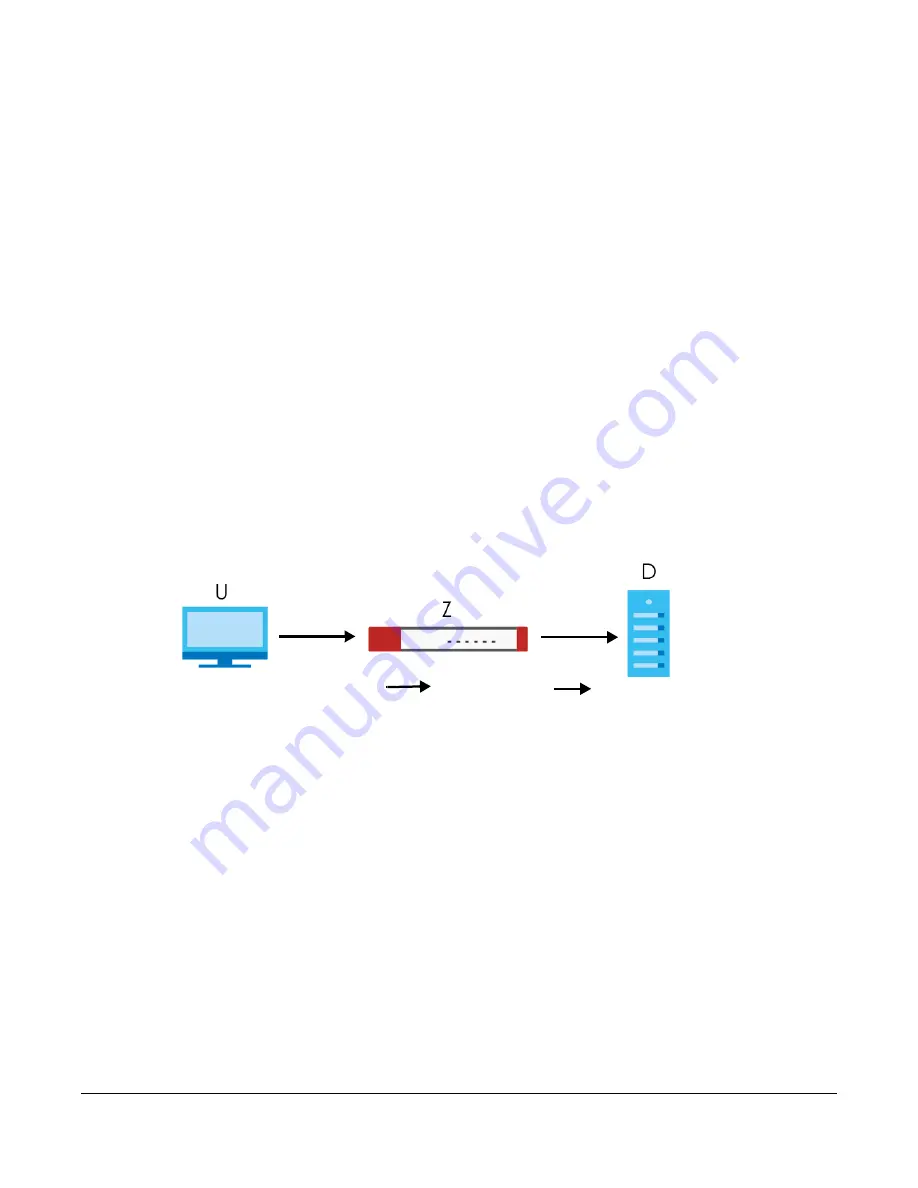
An example process is shown in the following figure. User
U
sends a HTTPS request (SSL) to destination
server
D
, via the Zyxel Device,
Z
. The traffic matches an SSL Inspection profile in a security policy, so the
Zyxel Device decrypts the traffic using SSL Inspection. The decrypted traffic is then inspected by the
Security Service profiles in the same security profile that matched the SSL Inspection profile. If all is OK,
then the Zyxel Device re-encrypts the traffic using SSL Inspection and forwards it to the destination server
D
. SSL traffic could be in the opposite direction for other examples.
Figure 368
SSL Inspection Overview
Note: Email security cannot be applied to traffic decrypted by SSL Inspection.
33.1.1 What You Can Do in this Chapter
• Use the
Security Service > SSL Inspection > Profile
screen (
) to view SSL
Inspection profiles. Click the
Add
or
Edit
icon in this screen to configure the CA certificate, action and
log in an SSL Inspection profile.
• Use the
Security Service > SSL Inspection >
Exclude List
screens (
) to create a
whitelist of destination servers to which traffic is passed through uninspected.
33.1.2 What You Need To Know
• Supported Cipher Suite
• DES (Data Encryption Standard)
HTTPS
SSL
Inspection
Decrypt
Security Service
AP
CF
IDP
Anti-Malware
SSL
Inspection
Encrypt







































