Chapter 7 Wireless
EX5501-B0 / AX7501-B0 / PX7501-B0 User’s Guide
122
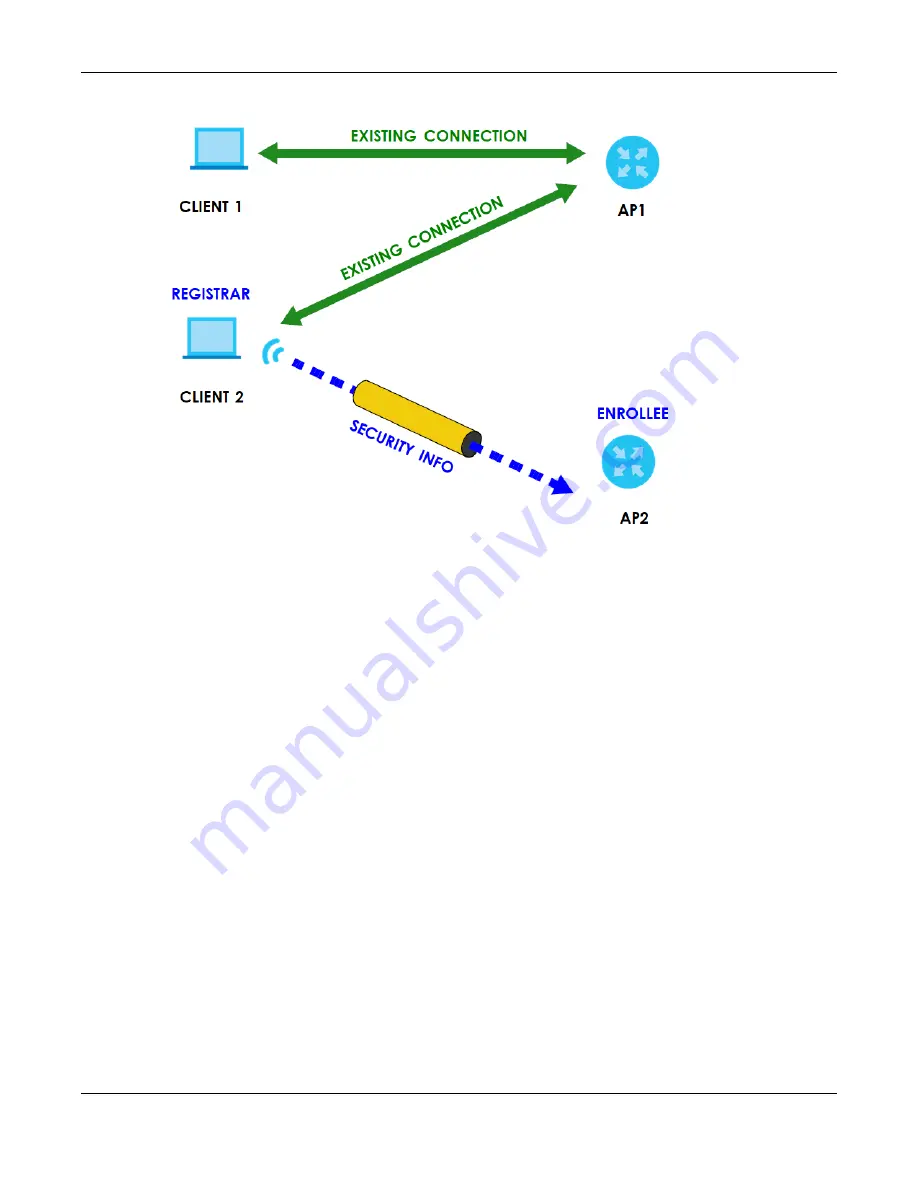
Figure 71
WPS: Example Network Step 3
7.9.8.5 Limitations of WPS
WPS has some limitations of which you should be aware.
• WPS works in Infrastructure networks only (where an AP and a wireless client communicate). It does
not work in Ad-Hoc networks (where there is no AP).
• When you use WPS, it works between two devices only. You cannot enroll multiple devices
simultaneously, you must enroll one after the other.
For instance, if you have two enrollees and one registrar you must set up the first enrollee (by pressing
the WPS button on the registrar and the first enrollee, for example), then check that it successfully
enrolled, then set up the second device in the same way.
• WPS works only with other WPS-enabled devices. However, you can still add non-WPS devices to a
network you already set up using WPS.
WPS works by automatically issuing a randomly-generated WPA-PSK or WPA2-PSK pre-shared key
from the registrar device to the enrollee devices. Whether the network uses WPA-PSK or WPA2-PSK
depends on the device. You can check the configuration interface of the registrar device to discover
the key the network is using (if the device supports this feature). Then, you can enter the key into the
non-WPS device and join the network as normal (the non-WPS device must also support WPA-PSK or
WPA2-PSK).
• When you use the PBC method, there is a short period (from the moment you press the button on one
device to the moment you press the button on the other device) when any WPS-enabled device
could join the network. This is because the registrar has no way of identifying the “correct” enrollee,
and cannot differentiate between your enrollee and a rogue device. This is a possible way for a
hacker to gain access to a network.
You can easily check to see if this has happened. WPS works between only two devices
simultaneously, so if another device has enrolled your device will be unable to enroll, and will not
have access to the network. If this happens, open the access point’s configuration interface and look
at the list of associated clients (usually displayed by MAC address). It does not matter if the access
















































