Chapter 25 Access Control
GS-2024 User’s Guide
188
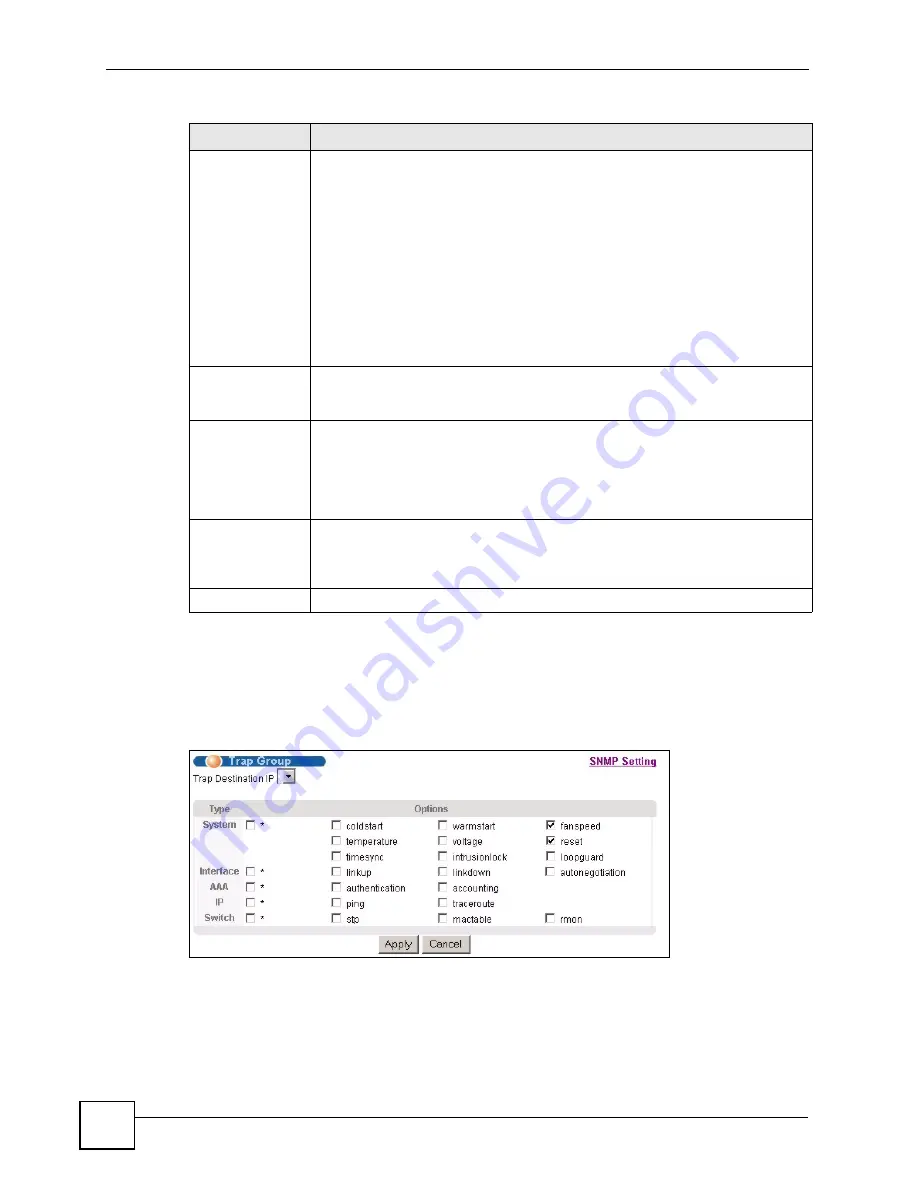
25.3.5 Configuring SNMP Trap Group
From the
SNMP
screen, click
Trap Group
to view the screen as shown. Use the
Trap
Group
screen to specify the types of SNMP traps that should be sent to each SNMP manager.
Figure 104
Management > Access Control > SNMP > Trap Group
Security Level
Select whether you want to implement authentication and/or encryption for SNMP
communication from this user. Choose:
•
noauth
-to use the username as the password string to send to the SNMP
manager. This is equivalent to the Get, Set and Trap Community in SNMP v2c.
This is the lowest security level.
•
auth
- to implement an authentication algorithm for SNMP messages sent by
this user.
•
priv
- to implement authentication and encryption for SNMP messages sent by
this user. This is the highest security level.
Note: The settings on the SNMP manager must be set at the same
security level or higher than the security level settings on the
Switch.
Authentication Select an authentication algorithm. MD5 (Message Digest 5) and SHA (Secure
Hash Algorithm) are hash algorithms used to authenticate SNMP data. SHA
authentication is generally considered stronger than MD5, but is slower.
Privacy
Specify the encryption method for SNMP communication from this user. You can
choose one of the following:
•
DES
- Data Encryption Standard is a widely used (but breakable) method of
data encryption. It applies a 56-bit key to each 64-bit block of data.
•
AES
- Advanced Encryption Standard is another method for data encryption
that also uses a secret key. AES applies a 128-bit key to 128-bit blocks of data.
Apply
Click
Apply
to save your changes to the Switch’s run-time memory. The Switch
loses these changes if it is turned off or loses power, so use the
Save
link on the
top navigation panel to save your changes to the non-volatile memory when you
are done configuring.
Cancel
Click
Cancel
to begin configuring this screen afresh.
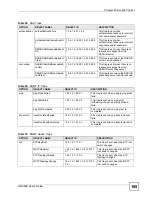
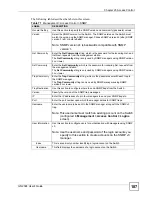
Table 71
Management > Access Control > SNMP (continued)
LABEL
DESCRIPTION
Summary of Contents for Dimension GS-2024
Page 2: ......
Page 7: ...Safety Warnings GS 2024 User s Guide 7 This product is recyclable Dispose of it properly ...
Page 8: ...Safety Warnings GS 2024 User s Guide 8 ...
Page 26: ...List of Tables GS 2024 User s Guide 26 ...
Page 28: ...28 ...
Page 36: ...Chapter 2 Hardware Installation and Connection GS 2024 User s Guide 36 ...
Page 44: ...44 ...
Page 62: ...Chapter 6 System Status and Port Statistics GS 2024 User s Guide 62 ...
Page 70: ...Chapter 7 Basic Setting GS 2024 User s Guide 70 Figure 27 Basic Setting IP Setup ...
Page 74: ...Chapter 7 Basic Setting GS 2024 User s Guide 74 ...
Page 76: ...76 ...
Page 88: ...Chapter 8 VLAN GS 2024 User s Guide 88 ...
Page 110: ...Chapter 13 Mirroring GS 2024 User s Guide 110 ...
Page 120: ...Chapter 15 Port Authentication GS 2024 User s Guide 120 ...
Page 138: ...Chapter 18 Multicast GS 2024 User s Guide 138 ...
Page 152: ...Chapter 19 Authentication Accounting GS 2024 User s Guide 152 ...
Page 157: ...157 PART IV IP Application Static Route 159 Differentiated Services 163 DHCP 167 ...
Page 158: ...158 ...
Page 162: ...Chapter 21 Static Route GS 2024 User s Guide 162 ...
Page 166: ...Chapter 22 Differentiated Services GS 2024 User s Guide 166 ...
Page 174: ...174 ...
Page 198: ...Chapter 25 Access Control GS 2024 User s Guide 198 ...
Page 200: ...Chapter 26 Diagnostic GS 2024 User s Guide 200 ...
Page 204: ...Chapter 27 Syslog GS 2024 User s Guide 204 ...
Page 218: ...218 ...
Page 222: ...Chapter 32 Troubleshooting GS 2024 User s Guide 222 ...
Page 230: ...Chapter 33 Product Specifications GS 2024 User s Guide 230 ...
Page 232: ...232 ...
Page 240: ...Appendix A Pop up Windows JavaScripts and Java Permissions GS 2024 User s Guide 240 ...
Page 252: ...Appendix C Legal Information GS 2024 User s Guide 252 ...
Page 258: ...Appendix D Customer Support GS 2024 User s Guide 258 ...
Page 266: ...Index GS 2024 User s Guide 266 ...