ZyXEL G-120 User’s Guide
Chapter 3 Wireless LAN Network
31
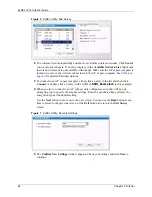
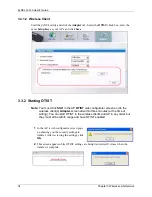
For WLAN adapters without the passphrase feature, you can still take advantage of this
feature by writing down the four automatically generated WEP keys from the
Security
Setting
screen of the ZyXEL utility and entering them manually as the WEP keys in the
other WLAN adapter(s).
• Enter the WEP keys manually.
Your G-120 allows you to configure up to four 64-bit, 128-bit or 256-bit WEP keys and
only one key is used as the default key at any one time.
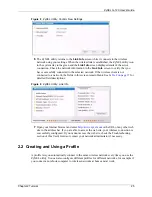
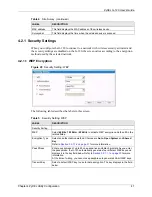
3.2.1.1.2 Authentication Type
The IEEE 802.11b/g standard describes a simple authentication method between the wireless
stations and AP. Three authentication types are defined:
Auto
,
Open System
and
Shared
Key
.
• Open System mode is implemented for ease-of-use and when security is not an issue.
The wireless station and the AP or peer computer do not share a secret key. Thus the
wireless stations can associate with any AP or peer computer and listen to any transmitted
data that is not encrypted.
• Shared Key mode involves a shared secret key to authenticate the wireless station to the
AP or peer computer. This requires you to enable the wireless LAN security and use same
settings on both the wireless station and the AP or peer computer.
• Auto authentication mode allows the G-120 to switch between the open system and
shared key modes automatically. Use the auto mode if you do not know the
authentication mode of the other wireless stations.
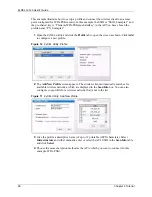
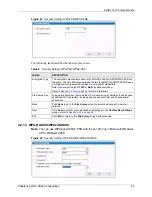
3.2.1.2 IEEE 802.1x
The IEEE 802.1x standard outlines enhanced security methods for both the authentication of
wireless stations and encryption key management. Authentication can be done using an
external RADIUS server.
3.2.1.2.1 EAP Authentication
EAP (Extensible Authentication Protocol) is an authentication protocol that runs on top of the
IEEE 802.1x transport mechanism in order to support multiple types of user authentication. By
using EAP to interact with an EAP-compatible RADIUS server, an access point helps a
wireless station and a RADIUS server perform authentication.
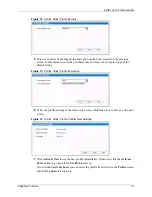
The type of authentication you use depends on the RADIUS server and an intermediary AP(s)
that supports IEEE 802.1x. The G-120 supports EAP-TLS and EAP-PEAP. Refer to
for descriptions.
For EAP-TLS authentication type, you must first have a wired connection to the network and
obtain the certificate(s) from a certificate authority (CA). A certificate (also called digital IDs)
can be used to authenticate users and a CA issues certificates and guarantees the identity of
each certificate owner.
Summary of Contents for G-120
Page 1: ...ZyXEL G 120 802 11g Wireless CardBus Card User s Guide Version 1 00 Edition 1 6 2006...
Page 2: ......
Page 11: ...ZyXEL G 120 User s Guide Table of Contents 11 Index 93...
Page 12: ...ZyXEL G 120 User s Guide 12 Table of Contents...
Page 16: ...ZyXEL G 120 User s Guide 16 List of Tables...
Page 36: ...ZyXEL G 120 User s Guide 36 Chapter 3 Wireless LAN Network...
Page 58: ...ZyXEL G 120 User s Guide 58 Chapter 5 Maintenance...
Page 74: ...ZyXEL G 120 User s Guide 74 Appendix B Management with Wireless Zero Configuration...
Page 92: ...ZyXEL G 120 User s Guide 92 Appendix D Setting up Your Computer s IP Address...