Appendix C Wireless LANs
NBG-510S User’s Guide
185
If the
Fragmentation Threshold
value is smaller than the
RTS/CTS
value (see previously)
you set then the RTS (Request To Send)/CTS (Clear to Send) handshake will never occur as
data frames will be fragmented before they reach
RTS/CTS
size.
Preamble Type
Preamble is used to signal that data is coming to the receiver. Short and long refer to the length
of the synchronization field in a packet.
Short preamble increases performance as less time sending preamble means more time for
sending data. All IEEE 802.11 compliant wireless adapters support long preamble, but not all
support short preamble.
Use long preamble if you are unsure what preamble mode other wireless devices on the
network support, and to provide more reliable communications in busy wireless networks.
Use short preamble if you are sure all wireless devices on the network support it, and to
provide more efficient communications.
Use the dynamic setting to automatically use short preamble when all wireless devices on the
network support it, otherwise the ZyXEL Device uses long preamble.
"
The wireless devices MUST
use the same preamble mode in order to
communicate.
IEEE 802.11g Wireless LAN
IEEE 802.11g is fully compatible with the IEEE 802.11b standard. This means an IEEE
802.11b adapter can interface directly with an IEEE 802.11g access point (and vice versa) at
11 Mbps or lower depending on range. IEEE 802.11g has several intermediate rate steps
between the maximum and minimum data rates. The IEEE 802.11g data rate and modulation
are as follows:
Wireless Security Overview
Wireless security is vital to your network to protect wireless communication between wireless
clients, access points and the wired network.
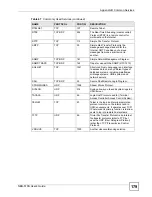
Table 68
IEEE 802.11g
DATA RATE (MBPS)
MODULATION
1
DBPSK (Differential Binary Phase Shift Keyed)
2
DQPSK (Differential Quadrature Phase Shift Keying)
5.5 / 11
CCK (Complementary Code Keying)
6/9/12/18/24/36/48/54
OFDM (Orthogonal Frequency Division Multiplexing)
Summary of Contents for NBG-510S
Page 2: ......
Page 7: ...Safety Warnings NBG 510S User s Guide 7 This product is recyclable Dispose of it properly ...
Page 8: ...Safety Warnings NBG 510S User s Guide 8 ...
Page 18: ...Table of Contents NBG 510S User s Guide 18 ...
Page 26: ...26 ...
Page 44: ...Chapter 5 Setup Wizard NBG 510S User s Guide 44 Figure 20 Wizard Applying Internet Settings ...
Page 58: ...Chapter 6 Tutorials NBG 510S User s Guide 58 ...
Page 60: ...60 ...
Page 76: ...Chapter 8 WAN NBG 510S User s Guide 76 ...
Page 78: ...Chapter 9 LAN NBG 510S User s Guide 78 ...
Page 88: ...Chapter 11 NAT and Firewall WAN to LAN NBG 510S User s Guide 88 ...
Page 91: ...91 PART III Security Access Control 93 Content Filtering 101 ...
Page 92: ...92 ...
Page 100: ...Chapter 13 Access Control NBG 510S User s Guide 100 ...
Page 103: ...103 PART IV Management UPnP 105 Static Route 113 ...
Page 104: ...104 ...
Page 116: ...Chapter 16 Static Route NBG 510S User s Guide 116 ...
Page 117: ...117 PART V Maintenance System 119 Logs 123 Tools 125 ...
Page 118: ...118 ...
Page 134: ...134 ...
Page 136: ...Chapter 20 Secure Remote Access Title NBG 510S User s Guide 136 ...
Page 140: ...Chapter 21 Secure Remote Access User Info NBG 510S User s Guide 140 ...
Page 150: ...Chapter 23 Manage User Access Permissions NBG 510S User s Guide 150 ...
Page 154: ...Chapter 24 Secure Remote Desktop Control NBG 510S User s Guide 154 ...
Page 162: ...Chapter 25 Secure Remote Access Screens NBG 510S User s Guide 162 ...
Page 164: ...164 ...
Page 170: ...Chapter 26 Troubleshooting NBG 510S User s Guide 170 ...
Page 176: ...Appendix A Product Specifications NBG 510S User s Guide 176 ...
Page 180: ...Appendix B Common Services NBG 510S User s Guide 180 ...
Page 198: ...Appendix D Legal Information NBG 510S User s Guide 198 ...
Page 204: ...Appendix E Customer Support NBG 510S User s Guide 204 ...
Page 209: ...Index NBG 510S User s Guide 209 WPA PSK 189 190 application example 191 ...
Page 210: ...Index NBG 510S User s Guide 210 ...