Appendix C Wireless LANs
NBG-510S User’s Guide
186
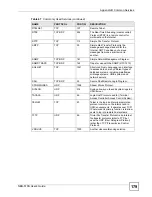
Wireless security methods available on the ZyXEL Device are data encryption, wireless client
authentication, restricting access by device MAC address and hiding the ZyXEL Device
identity.
The following figure shows the relative effectiveness of these wireless security methods
available on your ZyXEL Device.
"
You must enable the same wireless security settings on the ZyXEL Device and
on all wireless clients that you want to associate with it.
IEEE 802.1x
In June 2001, the IEEE 802.1x standard was designed to extend the features of IEEE 802.11 to
support extended authentication as well as providing additional accounting and control
features. It is supported by Windows XP and a number of network devices. Some advantages
of IEEE 802.1x are:
• User based identification that allows for roaming.
• Support for RADIUS (Remote Authentication Dial In User Service, RFC 2138, 2139) for
centralized user profile and accounting management on a network RADIUS server.
• Support for EAP (Extensible Authentication Protocol, RFC 2486) that allows additional
authentication methods to be deployed with no changes to the access point or the wireless
clients.
RADIUS
RADIUS is based on a client-server model that supports authentication, authorization and
accounting. The access point is the client and the server is the RADIUS server. The RADIUS
server handles the following tasks:
• Authentication
Determines the identity of the users.
• Authorization
Table 69
Wireless Security Levels
SECURITY
LEVEL
SECURITY TYPE
Least
Secure
Most Secure
Unique SSID (Default)
Unique SSID with Hide SSID Enabled
MAC Address Filtering
WEP Encryption
IEEE802.1x EAP with RADIUS Server Authentication
Wi-Fi Protected Access (WPA)
WPA2
Summary of Contents for NBG-510S
Page 2: ......
Page 7: ...Safety Warnings NBG 510S User s Guide 7 This product is recyclable Dispose of it properly ...
Page 8: ...Safety Warnings NBG 510S User s Guide 8 ...
Page 18: ...Table of Contents NBG 510S User s Guide 18 ...
Page 26: ...26 ...
Page 44: ...Chapter 5 Setup Wizard NBG 510S User s Guide 44 Figure 20 Wizard Applying Internet Settings ...
Page 58: ...Chapter 6 Tutorials NBG 510S User s Guide 58 ...
Page 60: ...60 ...
Page 76: ...Chapter 8 WAN NBG 510S User s Guide 76 ...
Page 78: ...Chapter 9 LAN NBG 510S User s Guide 78 ...
Page 88: ...Chapter 11 NAT and Firewall WAN to LAN NBG 510S User s Guide 88 ...
Page 91: ...91 PART III Security Access Control 93 Content Filtering 101 ...
Page 92: ...92 ...
Page 100: ...Chapter 13 Access Control NBG 510S User s Guide 100 ...
Page 103: ...103 PART IV Management UPnP 105 Static Route 113 ...
Page 104: ...104 ...
Page 116: ...Chapter 16 Static Route NBG 510S User s Guide 116 ...
Page 117: ...117 PART V Maintenance System 119 Logs 123 Tools 125 ...
Page 118: ...118 ...
Page 134: ...134 ...
Page 136: ...Chapter 20 Secure Remote Access Title NBG 510S User s Guide 136 ...
Page 140: ...Chapter 21 Secure Remote Access User Info NBG 510S User s Guide 140 ...
Page 150: ...Chapter 23 Manage User Access Permissions NBG 510S User s Guide 150 ...
Page 154: ...Chapter 24 Secure Remote Desktop Control NBG 510S User s Guide 154 ...
Page 162: ...Chapter 25 Secure Remote Access Screens NBG 510S User s Guide 162 ...
Page 164: ...164 ...
Page 170: ...Chapter 26 Troubleshooting NBG 510S User s Guide 170 ...
Page 176: ...Appendix A Product Specifications NBG 510S User s Guide 176 ...
Page 180: ...Appendix B Common Services NBG 510S User s Guide 180 ...
Page 198: ...Appendix D Legal Information NBG 510S User s Guide 198 ...
Page 204: ...Appendix E Customer Support NBG 510S User s Guide 204 ...
Page 209: ...Index NBG 510S User s Guide 209 WPA PSK 189 190 application example 191 ...
Page 210: ...Index NBG 510S User s Guide 210 ...