Chapter 7 Wireless LAN
NBG-510S User’s Guide
63
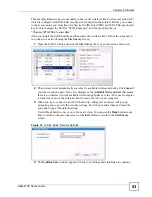
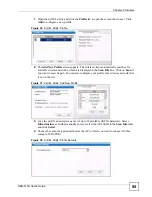
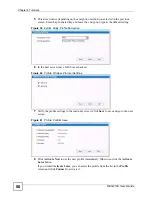
7.2.2 User Authentication
You can use WPA or WPA2 to have a RADIUS server authenticate users before they can use
the wireless network. You store each user’s user name and password on the RADIUS server.
However, every wireless client in the wireless network has to support IEEE 802.1x to do this.
Unauthorized devices can still see the information that is sent in the wireless network, even if
they cannot use the wireless network. Furthermore, there are ways for unauthorized wireless
users to get a valid user name and password. Then, they can use that user name and password
to use the wireless network.
7.2.3 Encryption
Wireless networks can use encryption to protect the information that is sent in the wireless
network. Encryption is like a secret code. If you do not know the secret code, you cannot
understand the message.
Many types of encryption use a key to protect the information in the wireless network. The
longer the key, the stronger the encryption. Every wireless client in the wireless network must
have the same key.
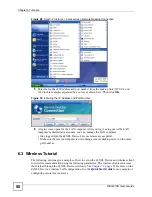
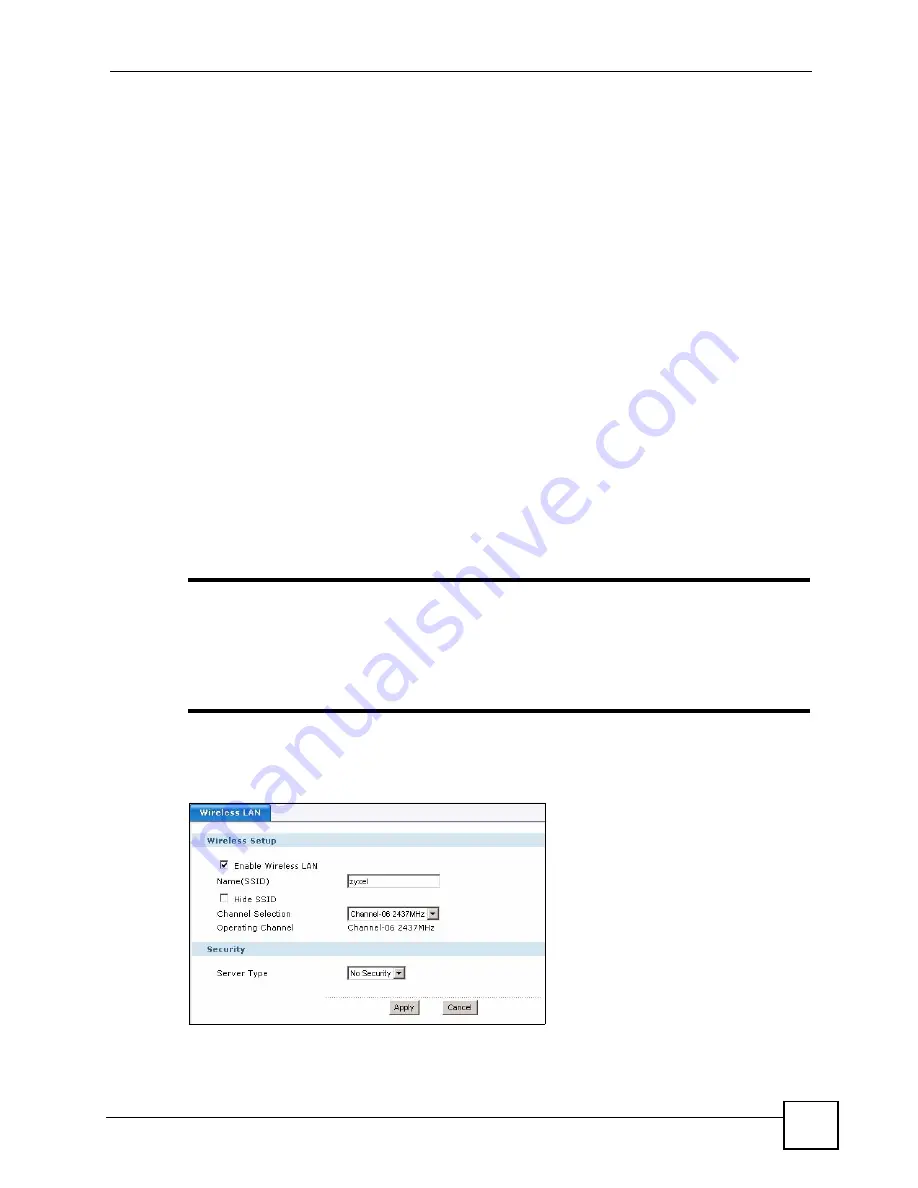
7.3 Wireless LAN Screen
"
If you are configuring the ZyXEL Device from a computer connected to the
wireless LAN and you change the ZyXEL Device’s SSID, channel or security
settings, you will lose your wireless connection when you press
Apply
to
confirm. You must then change the wireless settings of your computer to
match the ZyXEL Device’s new settings.
Click
Network
>
Wireless LAN
to open the
General
screen.
Figure 44
Network > Wireless LAN
Summary of Contents for NBG-510S
Page 2: ......
Page 7: ...Safety Warnings NBG 510S User s Guide 7 This product is recyclable Dispose of it properly ...
Page 8: ...Safety Warnings NBG 510S User s Guide 8 ...
Page 18: ...Table of Contents NBG 510S User s Guide 18 ...
Page 26: ...26 ...
Page 44: ...Chapter 5 Setup Wizard NBG 510S User s Guide 44 Figure 20 Wizard Applying Internet Settings ...
Page 58: ...Chapter 6 Tutorials NBG 510S User s Guide 58 ...
Page 60: ...60 ...
Page 76: ...Chapter 8 WAN NBG 510S User s Guide 76 ...
Page 78: ...Chapter 9 LAN NBG 510S User s Guide 78 ...
Page 88: ...Chapter 11 NAT and Firewall WAN to LAN NBG 510S User s Guide 88 ...
Page 91: ...91 PART III Security Access Control 93 Content Filtering 101 ...
Page 92: ...92 ...
Page 100: ...Chapter 13 Access Control NBG 510S User s Guide 100 ...
Page 103: ...103 PART IV Management UPnP 105 Static Route 113 ...
Page 104: ...104 ...
Page 116: ...Chapter 16 Static Route NBG 510S User s Guide 116 ...
Page 117: ...117 PART V Maintenance System 119 Logs 123 Tools 125 ...
Page 118: ...118 ...
Page 134: ...134 ...
Page 136: ...Chapter 20 Secure Remote Access Title NBG 510S User s Guide 136 ...
Page 140: ...Chapter 21 Secure Remote Access User Info NBG 510S User s Guide 140 ...
Page 150: ...Chapter 23 Manage User Access Permissions NBG 510S User s Guide 150 ...
Page 154: ...Chapter 24 Secure Remote Desktop Control NBG 510S User s Guide 154 ...
Page 162: ...Chapter 25 Secure Remote Access Screens NBG 510S User s Guide 162 ...
Page 164: ...164 ...
Page 170: ...Chapter 26 Troubleshooting NBG 510S User s Guide 170 ...
Page 176: ...Appendix A Product Specifications NBG 510S User s Guide 176 ...
Page 180: ...Appendix B Common Services NBG 510S User s Guide 180 ...
Page 198: ...Appendix D Legal Information NBG 510S User s Guide 198 ...
Page 204: ...Appendix E Customer Support NBG 510S User s Guide 204 ...
Page 209: ...Index NBG 510S User s Guide 209 WPA PSK 189 190 application example 191 ...
Page 210: ...Index NBG 510S User s Guide 210 ...