Chapter 13 Access Control
NBG-510S User’s Guide
97
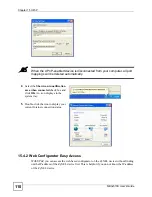
Figure 68
Security > Access Control > Add/Edit
The following table describes the labels in this screen.
Table 27
Security > Access Control > Add/Edit
LABEL
DESCRIPTION
Connections
going to the
Remote System
This firewall rule applies to traffic sent to this Internet destination(s).
You can select all destinations (
Any
), enter an IP address or domain name, enter
an IP subnet, or enter a range of IP addresses.
From the Local
System
This firewall rule applies to traffic sent from this LAN computer(s).
You can select a host name, enter an IP address, enter an IP subnet, or enter a
range of IP addresses.
Select
ALL
in the drop-down list box to apply the rule to all of the LAN computers.
For Services
Select the service (or port numbers) to which the firewall rule applies.
Select a service from the drop-down list box or select
Custom
and specify a port
number (or numbers) and protocol.
To enter a single port number, enter it in both fields.
To enter a range of port numbers, enter the starting port number in the first field
and the ending port number in the second field.
Protocol
Select the protocol that the service uses. Choices are:
TCP
,
UDP
,
AH
,
ESP
, and
GRE
.
Priority
Select the priority you want to give to the traffic that matches this firewall rule.
Should be
Select whether the ZyXEL Device should forward (
Allowed
) or drop (
Denied
)
outgoing traffic that matches this rule.
During the Access
Schedule
Select a time schedule to apply the rule only during the schedule’s times. You
must have already configured the schedule. See
to configure schedules.
Always
applies the rule all the time.
Schedules only apply to your custom firewall rules. The pre-defined (default)
firewall rules apply all the time.
Apply
Click
Apply
to save the settings.
Cancel
Click
Cancel
to return to the previous screen and not save your changes.
Summary of Contents for NBG-510S
Page 2: ......
Page 7: ...Safety Warnings NBG 510S User s Guide 7 This product is recyclable Dispose of it properly ...
Page 8: ...Safety Warnings NBG 510S User s Guide 8 ...
Page 18: ...Table of Contents NBG 510S User s Guide 18 ...
Page 26: ...26 ...
Page 44: ...Chapter 5 Setup Wizard NBG 510S User s Guide 44 Figure 20 Wizard Applying Internet Settings ...
Page 58: ...Chapter 6 Tutorials NBG 510S User s Guide 58 ...
Page 60: ...60 ...
Page 76: ...Chapter 8 WAN NBG 510S User s Guide 76 ...
Page 78: ...Chapter 9 LAN NBG 510S User s Guide 78 ...
Page 88: ...Chapter 11 NAT and Firewall WAN to LAN NBG 510S User s Guide 88 ...
Page 91: ...91 PART III Security Access Control 93 Content Filtering 101 ...
Page 92: ...92 ...
Page 100: ...Chapter 13 Access Control NBG 510S User s Guide 100 ...
Page 103: ...103 PART IV Management UPnP 105 Static Route 113 ...
Page 104: ...104 ...
Page 116: ...Chapter 16 Static Route NBG 510S User s Guide 116 ...
Page 117: ...117 PART V Maintenance System 119 Logs 123 Tools 125 ...
Page 118: ...118 ...
Page 134: ...134 ...
Page 136: ...Chapter 20 Secure Remote Access Title NBG 510S User s Guide 136 ...
Page 140: ...Chapter 21 Secure Remote Access User Info NBG 510S User s Guide 140 ...
Page 150: ...Chapter 23 Manage User Access Permissions NBG 510S User s Guide 150 ...
Page 154: ...Chapter 24 Secure Remote Desktop Control NBG 510S User s Guide 154 ...
Page 162: ...Chapter 25 Secure Remote Access Screens NBG 510S User s Guide 162 ...
Page 164: ...164 ...
Page 170: ...Chapter 26 Troubleshooting NBG 510S User s Guide 170 ...
Page 176: ...Appendix A Product Specifications NBG 510S User s Guide 176 ...
Page 180: ...Appendix B Common Services NBG 510S User s Guide 180 ...
Page 198: ...Appendix D Legal Information NBG 510S User s Guide 198 ...
Page 204: ...Appendix E Customer Support NBG 510S User s Guide 204 ...
Page 209: ...Index NBG 510S User s Guide 209 WPA PSK 189 190 application example 191 ...
Page 210: ...Index NBG 510S User s Guide 210 ...