Appendix I How to Access and Use the CLI
ZyXEL NWA-1100 User’s Guide
200
stdio set
command to extend the idle timeout. For example, the ZyXEL Device
automatically logs you out of the management interface after 60 minutes of
inactivity after you use the
sys stdio set 60
command. Use the
sys stdio
show
command to display the current idle timeout setting.
Command Conventions
Command descriptions follow these conventions:
• Commands are in
courier new font
.
• Required input values are in angle brackets <>; for example,
ping <
ip-
address
>
means that you must specify an IP address for this command.
• Optional fields are in square brackets []; for instance in the
show logins
[
name
]
command, the
name
field is optional.
The following is an example of a required field within an optional field:
snmp-
server [contact <
system contact
>]
, the
contact
field is optional. However,
if you use
contact
, then you must provide the
system contact
information.
• The
|
(bar) symbol means “or”.
•
italic
terms represent user-defined input values; for example, in
sys
datetime date [
year month date
]
,
year month date
can be replaced by the
actual year month and date that you want to set, for example, 2007 08 15.
• A key stroke is denoted by square brackets and uppercase text, for example,
[ENTER] means the “Enter” or “Return” key on your keyboard.
•
<cr>
means press the [ENTER] key.
• An arrow (
-->
) indicates that this line is a continuation of the previous line.
A long list of pre-defined values may be replaced by a command input value
‘variable’ so as to avoid a very long command in the description table. Refer to the
command input values table if you are unsure of what to enter.
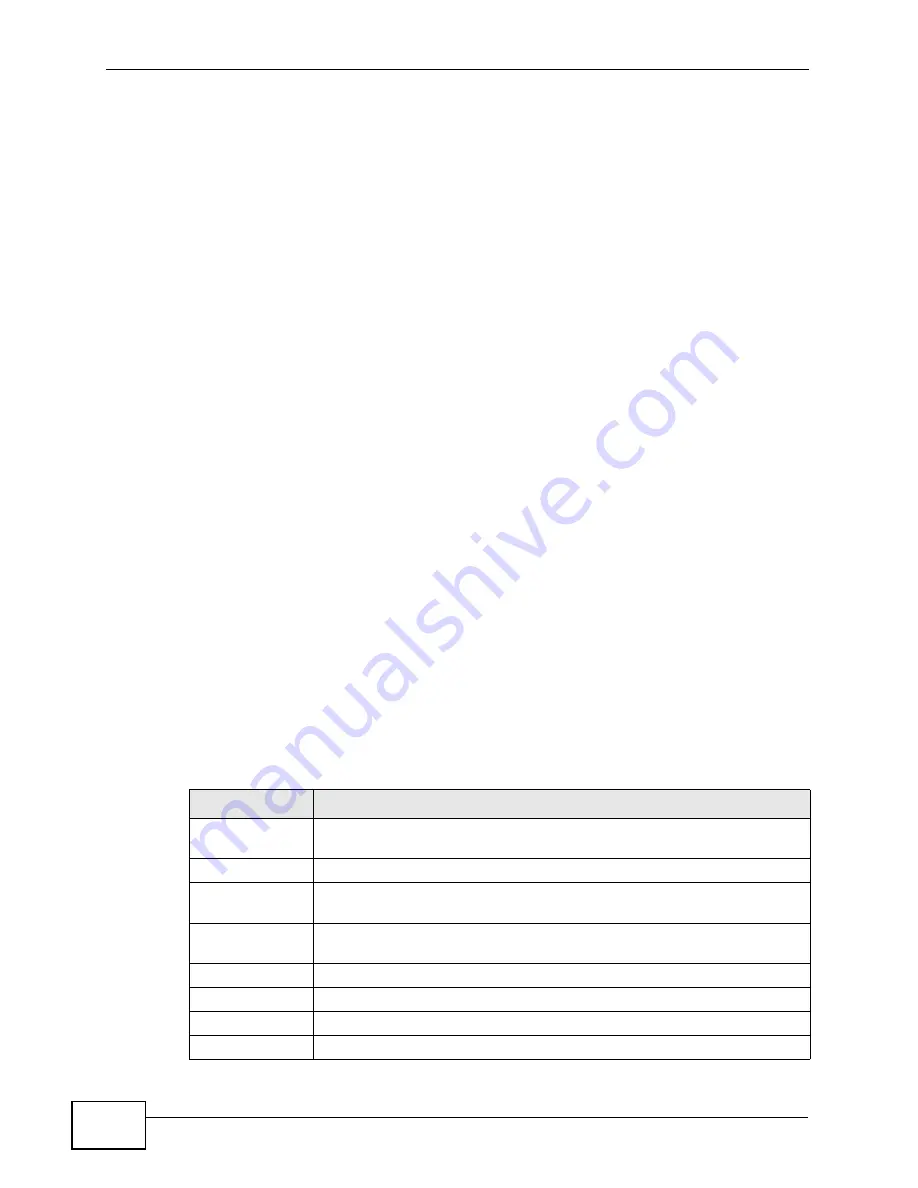
Table 75
Common Command Input Values
LABEL
DESCRIPTION
description
Used when a command has a description field in order to add more
detail.
ip-address
An IP address in dotted decimal notation. For example, 192.168.1.3.
mask
The subnet mask in dotted decimal notation, for example,
255.255.255.0.
mask-bits
The number of bits in an address’s subnet mask. For example type /24
for a subnet mask of 255.255.255.0.
port
A port number.
hostname
The hostname can be an IP address or domain name.
name
Used for the name of a rule, policy, set, group and so on.
number
Used for a number, for example 10, that you have to enter.
Summary of Contents for NWA-1100
Page 2: ......
Page 8: ...Safety Warnings ZyXEL NWA 1100 User s Guide 8 ...
Page 10: ...Contents Overview ZyXEL NWA 1100 User s Guide 10 ...
Page 16: ...Table of Contents ZyXEL NWA 1100 User s Guide 16 ...
Page 18: ...18 ...
Page 32: ...Chapter 2 Introducing the Web Configurator ZyXEL NWA 1100 User s Guide 32 ...
Page 46: ...46 ...
Page 54: ...Chapter 5 System Screens ZyXEL NWA 1100 User s Guide 54 ...
Page 72: ...Chapter 6 Wireless Settings Screen ZyXEL NWA 1100 User s Guide 72 ...
Page 92: ...Chapter 8 RADIUS Screen ZyXEL NWA 1100 User s Guide 92 ...
Page 96: ...Chapter 9 MAC Filter Screen ZyXEL NWA 1100 User s Guide 96 ...
Page 100: ...Chapter 10 IP Screen ZyXEL NWA 1100 User s Guide 100 ...
Page 136: ...Chapter 15 Troubleshooting ZyXEL NWA 1100 User s Guide 136 ...
Page 138: ...138 ...
Page 142: ...Appendix B Power over Ethernet PoE Specifications ZyXEL NWA 1100 User s Guide 142 ...
Page 144: ...Appendix C Power Adaptor Specifications ZyXEL NWA 1100 User s Guide 144 ...
Page 198: ...Appendix H Text File Based Auto Configuration ZyXEL NWA 1100 User s Guide 198 ...
Page 214: ...Appendix J Open Software Announcements ZyWALL USG 300 User s Guide 214 ...
















































