ZyXEL NWA-3500 User’s Guide
231
C
H A P T E R
23
System Information and
Diagnosis
This chapter covers the information and diagnostic tools in SMT menus 24.1 to 24.4.
These tools include updates on system status, port status, log and trace capabilities and
upgrades for the system software. This chapter describes how to use these tools in detail.
Type “24” in the main menu and press
[ENTER]
to open
Menu 24 – System Maintenance
, as
shown in the following figure.
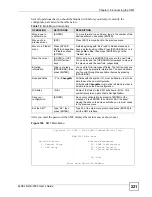
Figure 154
Menu 24 System Maintenance
23.1 System Status
The first selection,
System Status
gives you information on the status and statistics of the
ports, as shown next.
System Status
is a tool that can be used to monitor your ZyXEL Device.
Specifically, it gives you information on your Ethernet and Wireless LAN status, and the
number of packets sent and received.
To get to System Status, type “24” to go to
Menu 24 –
System Maintenance.
From this menu,
type “1”. There are two commands in
Menu 24.1 –
System Maintenance –
Status
. Entering 9
resets the counters; pressing
[ESC]
takes you back to the previous screen.
The following table describes the fields present in
Menu 24.1 –
System Maintenance –
Status
which are read-only and meant for diagnostic purposes.
Menu 24 - System Maintenance
1. System Status
2. System Information and Console Port Speed
3. Log and Trace
4. Diagnostic
8. Command Interpreter Mode
10. Time and Date Setting
11. Remote Management Setup
Enter Menu Selection Number:
Summary of Contents for NWA-3500
Page 2: ......
Page 7: ...Safety Warnings ZyXEL NWA 3500 User s Guide 7 ...
Page 8: ...Safety Warnings ZyXEL NWA 3500 User s Guide 8 ...
Page 10: ...Contents Overview ZyXEL NWA 3500 User s Guide 10 ...
Page 20: ...Table of Contents ZyXEL NWA 3500 User s Guide 20 ...
Page 26: ...List of Figures ZyXEL NWA 3500 User s Guide 26 ...
Page 30: ...List of Tables ZyXEL NWA 3500 User s Guide 30 ...
Page 32: ...32 ...
Page 42: ...Chapter 1 Introducing the ZyXEL Device ZyXEL NWA 3500 User s Guide 42 ...
Page 50: ...Chapter 3 Status Screens ZyXEL NWA 3500 User s Guide 50 ...
Page 78: ...Chapter 4 Tutorial ZyXEL NWA 3500 User s Guide 78 ...
Page 80: ...80 ...
Page 102: ...Chapter 6 Wireless Configuration ZyXEL NWA 3500 User s Guide 102 ...
Page 118: ...Chapter 7 Wireless Security Configuration ZyXEL NWA 3500 User s Guide 118 ...
Page 126: ...Chapter 8 MBSSID and SSID ZyXEL NWA 3500 User s Guide 126 ...
Page 140: ...Chapter 10 IP Screen ZyXEL NWA 3500 User s Guide 140 ...
Page 156: ...Chapter 12 Remote Management Screens ZyXEL NWA 3500 User s Guide 156 ...
Page 180: ...Chapter 14 Certificates ZyXEL NWA 3500 User s Guide 180 ...
Page 204: ...Chapter 16 VLAN ZyXEL NWA 3500 User s Guide 204 ...
Page 214: ...Chapter 17 Maintenance ZyXEL NWA 3500 User s Guide 214 ...
Page 216: ...216 ...
Page 230: ...Chapter 22 System Password ZyXEL NWA 3500 User s Guide 230 ...
Page 250: ...Chapter 25 System Maintenance and Information ZyXEL NWA 3500 User s Guide 250 ...
Page 256: ...256 ...
Page 260: ...Appendix B Power over Ethernet PoE Specifications ZyXEL NWA 3500 User s Guide 260 ...
Page 262: ...Appendix C Power Adaptor Specifications ZyXEL NWA 3500 User s Guide 262 ...
Page 274: ...Appendix D Setting up Your Computer s IP Address ZyXEL NWA 3500 User s Guide 274 ...
Page 310: ...Appendix H Text File Based Auto Configuration ZyXEL NWA 3500 User s Guide 310 ...
Page 314: ...Appendix I Legal Information ZyXEL NWA 3500 User s Guide 314 ...