P-661HW-D Series Support Notes
Configure an Internal Server behind SUA
Introduction
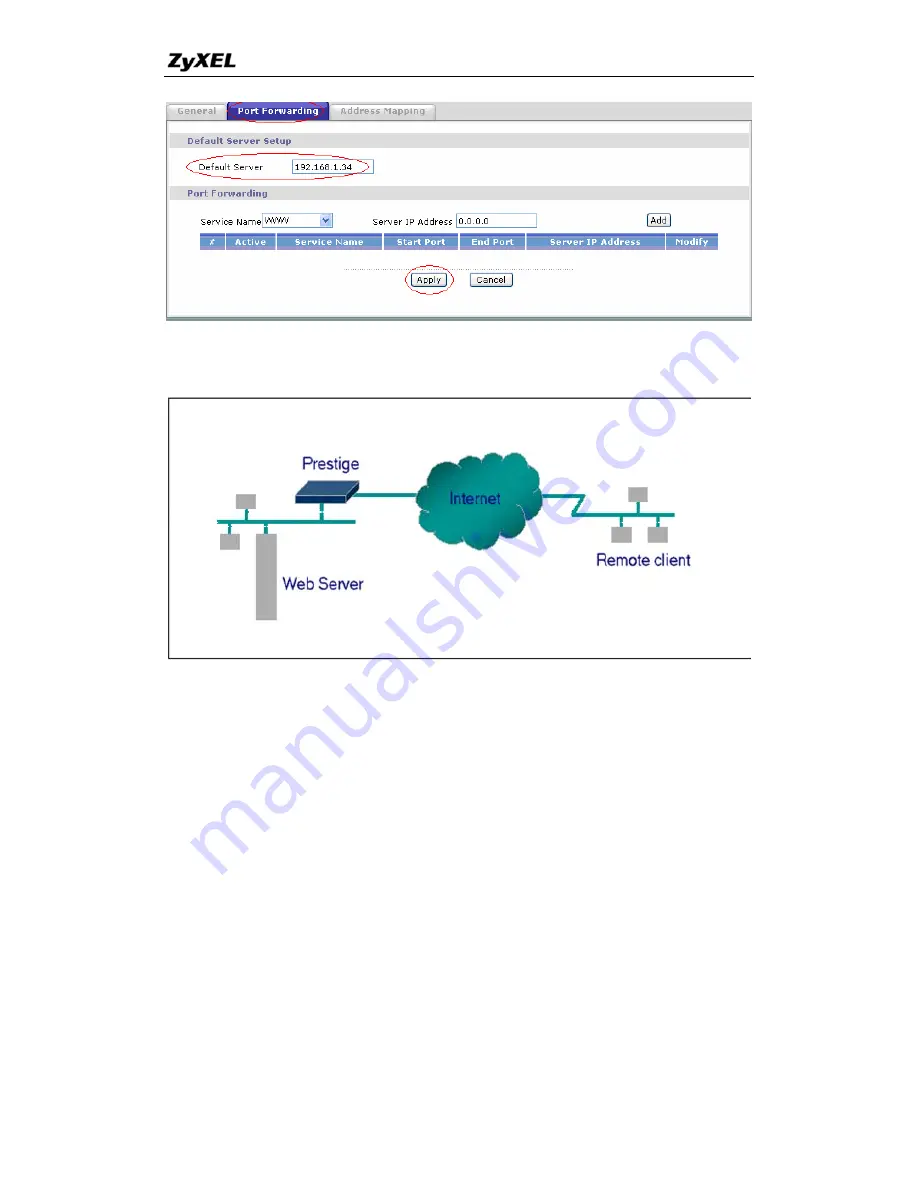
If you wish, you can make internal servers (e.g., Web, ftp or mail server)
accessible for outside users, even though SUA makes your LAN appear as a
single machine to the outside world. A service is identified by the port number.
Also, since you need to specify the IP address of a server behind the
P-661HW-D, a server must have a fixed IP address and not be a DHCP client
whose IP address potentially changes each time P-661HW-D is powered on.
In addition to the servers for specific services, SUA supports a default server.
A service request that does not have a server explicitly designated for is
forwarded to the default server. If the default server is not defined, the service
request is simply discarded.
Configuration
To make a server visible to the outside world, specify the port number of the
service and the inside address of the server in Web Configurator, Advanced
55
All contents copyright © 2006 ZyXEL Communications Corporation.
















































