Prestige 652H/HW Series User’s Guide
Firewalls
12-13
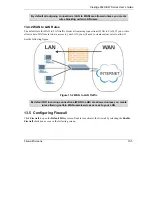
3. To block/allow both inbound (WAN to LAN) and outbound (LAN to WAN) traffic between the specific
inside host/network "A" and outside host/network "B". If the filter blocks the traffic from A to B, it also
blocks the traffic from B to A. Filters cannot distinguish traffic originating from an inside host or an
outside host by IP address.
4. To block/allow IP trace route.
12.7.2 Firewall
The firewall inspects packet contents as well as their source and destination addresses. Firewalls of this
type employ an inspection module, applicable to all protocols, that understands data in the packet is
intended for other layers, from the network layer (IP headers) up to the application layer.
The firewall performs stateful inspection. It takes into account the state of connections it handles so that,
for example, a legitimate incoming packet can be matched with the outbound request for that packet and
allowed in. Conversely, an incoming packet masquerading as a response to a nonexistent outbound
request can be blocked.
The firewall uses session filtering, i.e., smart rules, that enhance the filtering process and control the
network session rather than control individual packets in a session.
The firewall provides e-mail service to notify you of routine reports and when alerts occur.
When To Use The Firewall
1. To prevent DoS attacks and prevent hackers cracking your network.
2. A range of source and destination IP addresses as well as port numbers can be specified within one
firewall rule making the firewall a better choice when complex rules are required.
3. To selectively block/allow inbound or outbound traffic between inside host/networks and outside
host/networks. Remember that filters cannot distinguish traffic originating from an inside host or an
outside host by IP address.
4. The firewall performs better than filtering if you need to check many rules.
5. Use the firewall if you need routine e-mail reports about your system or need to be alerted when attacks
occur.
6. The firewall can block specific URL traffic that might occur in the future. The URL can be saved in an
Access Control List (ACL) database.
Summary of Contents for Prestige 652H series
Page 32: ......
Page 50: ......
Page 66: ......
Page 68: ......
Page 76: ......
Page 80: ......
Page 120: ...Prestige 652H HW Series User s Guide 8 12 WAN Setup Figure 8 6 Advanced WAN Backup ...
Page 128: ......
Page 146: ......
Page 148: ......
Page 162: ......
Page 178: ...Prestige 652H HW Series User s Guide 13 16 Firewall Screens Figure 13 8 Rule Edit Example ...
Page 196: ......
Page 198: ......
Page 204: ......
Page 214: ...Prestige 652H HW Series User s Guide 16 10 VPN Screens Figure 16 5 VPN IKE ...
Page 227: ...Prestige 652H HW Series User s Guide VPN Screens 16 23 Figure 16 8 Manual Setup ...
Page 238: ......
Page 258: ......
Page 277: ...Maintenance VIII Part VIII Maintenance This part covers the maintenance screens ...
Page 278: ......
Page 296: ......
Page 298: ......
Page 308: ......
Page 324: ......
Page 330: ......
Page 386: ......
Page 406: ......
Page 418: ......
Page 428: ......
Page 450: ......
Page 454: ......
Page 464: ......
Page 470: ......
Page 486: ......
Page 494: ......
Page 500: ......
Page 512: ......
Page 516: ......
Page 520: ......
Page 560: ......
Page 574: ......