Prestige 652H/HW Series User’s Guide
13-22
Firewall
Screens
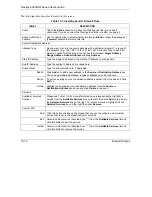
Table 13-5 Predefined Services
SERVICE
DESCRIPTION
SSDP(UDP:1900)
Simple Service Discovery Protocol (SSDP) is a discovery service
searching for Universal Plug and Play devices on your home network or
upstream Internet gateways using UDP port 1900.
SSH(TCP/UDP:22)
Secure Shell Remote Login Program.
STRMWORKS(UDP:1558)
Stream Works Protocol.
SYSLOG(UDP:514)
Syslog allows you to send system logs to a UNIX server.
TACACS(UDP:49)
Login Host Protocol used for (Terminal Access Controller Access Control
System).
TELNET(TCP:23)
Telnet is the login and terminal emulation protocol common on the Internet
and in UNIX environments. It operates over TCP/IP networks. Its primary
function is to allow users to log into remote host systems.
TFTP(UDP:69)
Trivial File Transfer Protocol is an Internet file transfer protocol similar to
FTP, but uses the UDP (User Datagram Protocol) rather than TCP
(Transmission Control Protocol).
VDOLIVE(TCP:7000)
Another videoconferencing solution.
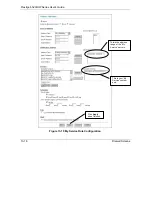
13.8 Anti-Probing
If an outside user attempts to probe an unsupported port on your Prestige, an ICMP response packet is
automatically returned. This allows the outside user to know the Prestige exists. The Prestige supports anti-
probing, which prevents the ICMP response packet from being sent. This keeps outsiders from discovering
your Prestige when unsupported ports are probed.
Internet Control Message Protocol (ICMP) is a message control and error-reporting protocol between a host
server and a gateway to the Internet. ICMP uses Internet Protocol (IP) datagrams, but the messages are
processed by the TCP/IP software and directly apparent to the application user.
Click
Firewall
, then the
Anti Probing
tab to open the screen.
Summary of Contents for Prestige 652H series
Page 32: ......
Page 50: ......
Page 66: ......
Page 68: ......
Page 76: ......
Page 80: ......
Page 120: ...Prestige 652H HW Series User s Guide 8 12 WAN Setup Figure 8 6 Advanced WAN Backup ...
Page 128: ......
Page 146: ......
Page 148: ......
Page 162: ......
Page 178: ...Prestige 652H HW Series User s Guide 13 16 Firewall Screens Figure 13 8 Rule Edit Example ...
Page 196: ......
Page 198: ......
Page 204: ......
Page 214: ...Prestige 652H HW Series User s Guide 16 10 VPN Screens Figure 16 5 VPN IKE ...
Page 227: ...Prestige 652H HW Series User s Guide VPN Screens 16 23 Figure 16 8 Manual Setup ...
Page 238: ......
Page 258: ......
Page 277: ...Maintenance VIII Part VIII Maintenance This part covers the maintenance screens ...
Page 278: ......
Page 296: ......
Page 298: ......
Page 308: ......
Page 324: ......
Page 330: ......
Page 386: ......
Page 406: ......
Page 418: ......
Page 428: ......
Page 450: ......
Page 454: ......
Page 464: ......
Page 470: ......
Page 486: ......
Page 494: ......
Page 500: ......
Page 512: ......
Page 516: ......
Page 520: ......
Page 560: ......
Page 574: ......