Prestige 652H/HW Series User’s Guide
15-4
Introduction to IPSec
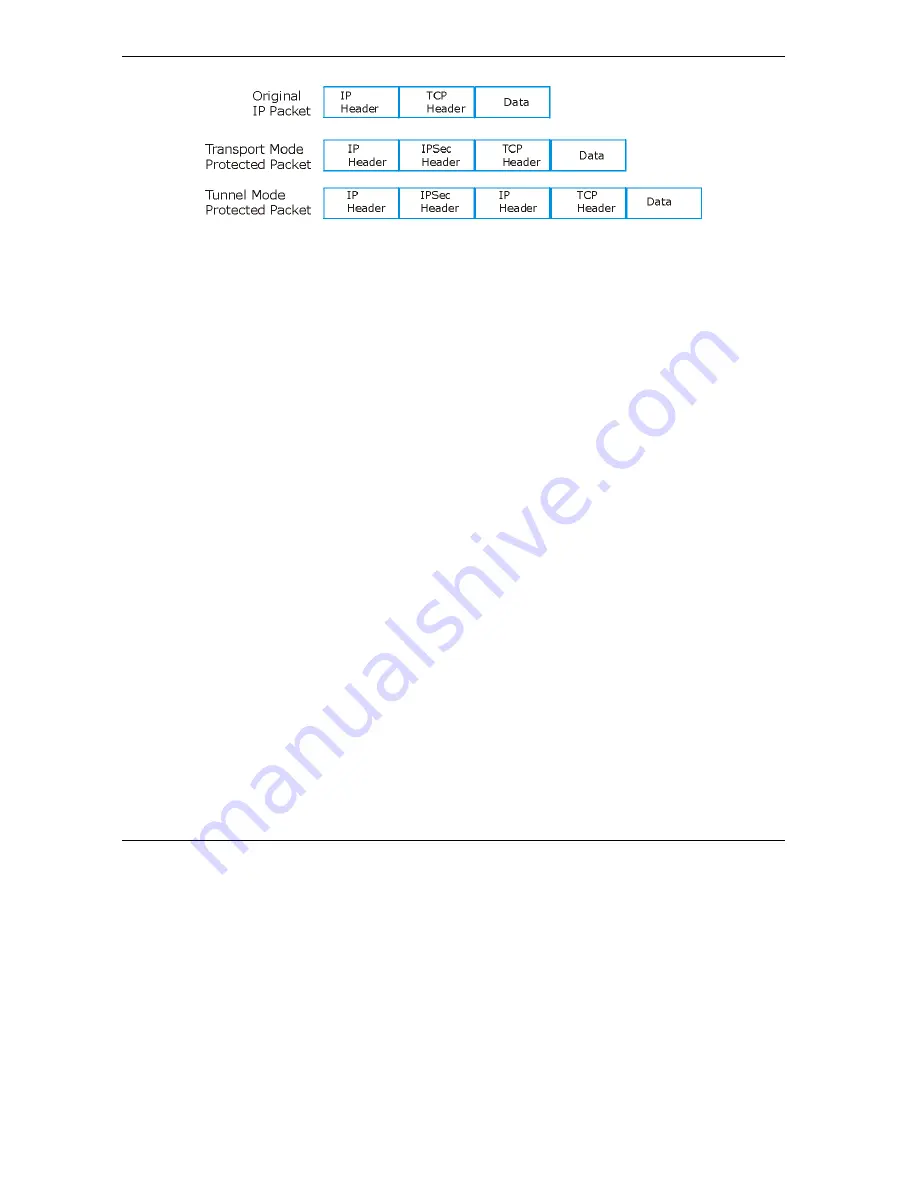
Figure 15-3 Transport and Tunnel Mode IPSec Encapsulation
15.3.1 Transport Mode
Transport
mode is used to protect upper layer protocols and only affects the data in the IP packet. In
Transport
mode, the IP packet contains the security protocol (
AH
or
ESP
) located after the original IP
header and options, but before any upper layer protocols contained in the packet (such as TCP and UDP).
With
ESP,
protection is applied only to the upper layer protocols contained in the packet. The IP header
information and options are not used in the authentication process. Therefore, the originating IP address
cannot be verified for integrity against the data.
With the use of
AH
as the security protocol, protection is extended forward into the IP header to verify the
integrity of the entire packet by use of portions of the original IP header in the hashing process.
15.3.2 Tunnel Mode
Tunnel
mode encapsulates the entire IP packet to transmit it securely. A
Tunnel
mode is required for
gateway services to provide access to internal systems.
Tunnel
mode is fundamentally an IP tunnel with
authentication and encryption. This is the most common mode of operation.
Tunnel
mode is required for
gateway to gateway and host to gateway communications.
Tunnel
mode communications have two sets of IP
headers:
Outside header
: The outside IP header contains the destination IP address of the VPN gateway.
Inside header
: The inside IP header contains the destination IP address of the final system behind
the VPN gateway. The security protocol appears after the outer IP header and before the inside IP
header.
15.4 IPSec and NAT
Read this section if you are running IPSec on a host computer behind the Prestige.
NAT is incompatible with the
AH
protocol in both
Transport
and
Tunnel
mode. An IPSec VPN using the
AH
protocol digitally signs the outbound packet, both data payload and headers, with a hash value appended
to the packet. When using
AH
protocol, packet contents (the data payload) are not encrypted.
A NAT device in between the IPSec endpoints will rewrite either the source or destination address with one
of its own choosing. The VPN device at the receiving end will verify the integrity of the incoming packet by
computing its own hash value, and complain that the hash value appended to the received packet doesn't
Summary of Contents for Prestige 652H series
Page 32: ......
Page 50: ......
Page 66: ......
Page 68: ......
Page 76: ......
Page 80: ......
Page 120: ...Prestige 652H HW Series User s Guide 8 12 WAN Setup Figure 8 6 Advanced WAN Backup ...
Page 128: ......
Page 146: ......
Page 148: ......
Page 162: ......
Page 178: ...Prestige 652H HW Series User s Guide 13 16 Firewall Screens Figure 13 8 Rule Edit Example ...
Page 196: ......
Page 198: ......
Page 204: ......
Page 214: ...Prestige 652H HW Series User s Guide 16 10 VPN Screens Figure 16 5 VPN IKE ...
Page 227: ...Prestige 652H HW Series User s Guide VPN Screens 16 23 Figure 16 8 Manual Setup ...
Page 238: ......
Page 258: ......
Page 277: ...Maintenance VIII Part VIII Maintenance This part covers the maintenance screens ...
Page 278: ......
Page 296: ......
Page 298: ......
Page 308: ......
Page 324: ......
Page 330: ......
Page 386: ......
Page 406: ......
Page 418: ......
Page 428: ......
Page 450: ......
Page 454: ......
Page 464: ......
Page 470: ......
Page 486: ......
Page 494: ......
Page 500: ......
Page 512: ......
Page 516: ......
Page 520: ......
Page 560: ......
Page 574: ......
















































