Chapter 25 Security Policy
UAG Series User’s Guide
292
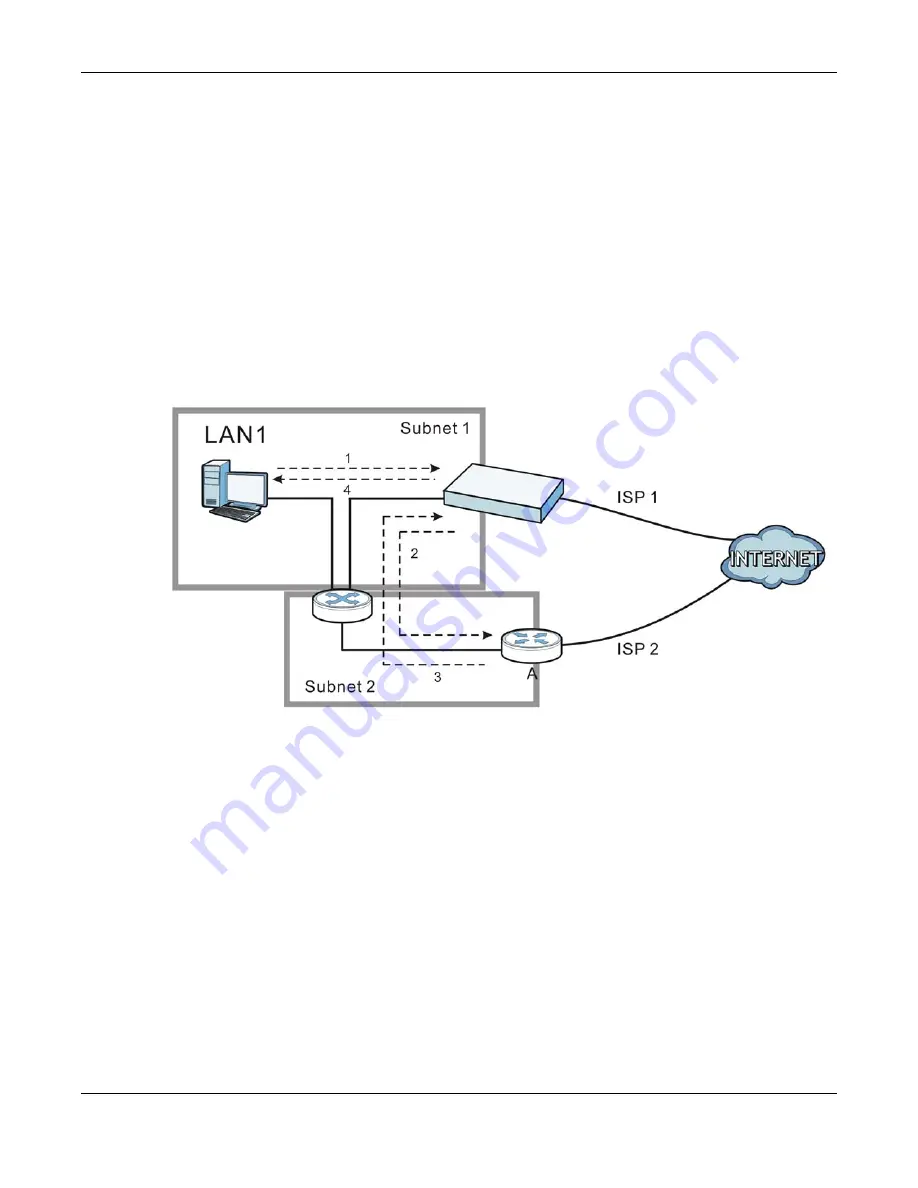
and the backup gateway on separate subnets. Virtual interfaces allow you to partition your network
into logical sections over the same interface. See the chapter about interfaces for more information.
By putting LAN 1 and the alternate gateway (
A
in the figure) in different subnets, all returning
network traffic must pass through the UAG to the LAN. The following steps and figure describe such
a scenario.
1
A computer on the LAN1 initiates a connection by sending a SYN packet to a receiving server on the
WAN.
2
The UAG
reroutes the packet to gateway
A
, which is in
Subnet 2
.
3
The reply from the WAN goes to the UAG.
4
The UAG then sends it to the computer on the LAN1 in
Subnet 1
.
Figure 206
Using Virtual Interfaces to Avoid Asymmetrical Routes
25.2.1 Configuring the Security Policy Control Screen
Click
Configuration > Security Policy > Policy Control
to open the
Policy
screen. Use this
screen to enable or disable policy control and asymmetrical routes, set a maximum number of
sessions per host, and display the configured policy control rules. Specify from which zone packets
come and to which zone packets travel to display only the rules specific to the selected direction.
Note the following.
• Besides configuring policy control, you also need to configure NAT rules to allow computers on
the WAN to access LAN devices. See
for more information.
• The UAG applies NAT (Destination NAT) settings before applying the policy control rules. So for
example, if you configure a NAT entry that sends WAN traffic to a LAN IP address, when you
configure a corresponding policy control rule to allow the traffic, you need to set the LAN IP
address as the destination.
• The ordering of your rules is very important as rules are applied in sequence.