Chapter 30 IPSec VPN
UAG Series User’s Guide
360
Encapsulation
There are two ways to encapsulate packets. Usually, you should use tunnel mode because it is more
secure. Transport mode is only used when the IPSec SA is used for communication between the
UAG and remote IPSec router (for example, for remote management), not between computers on
the local and remote networks.
Note: The UAG and remote IPSec router must use the same encapsulation.
These modes are illustrated below.
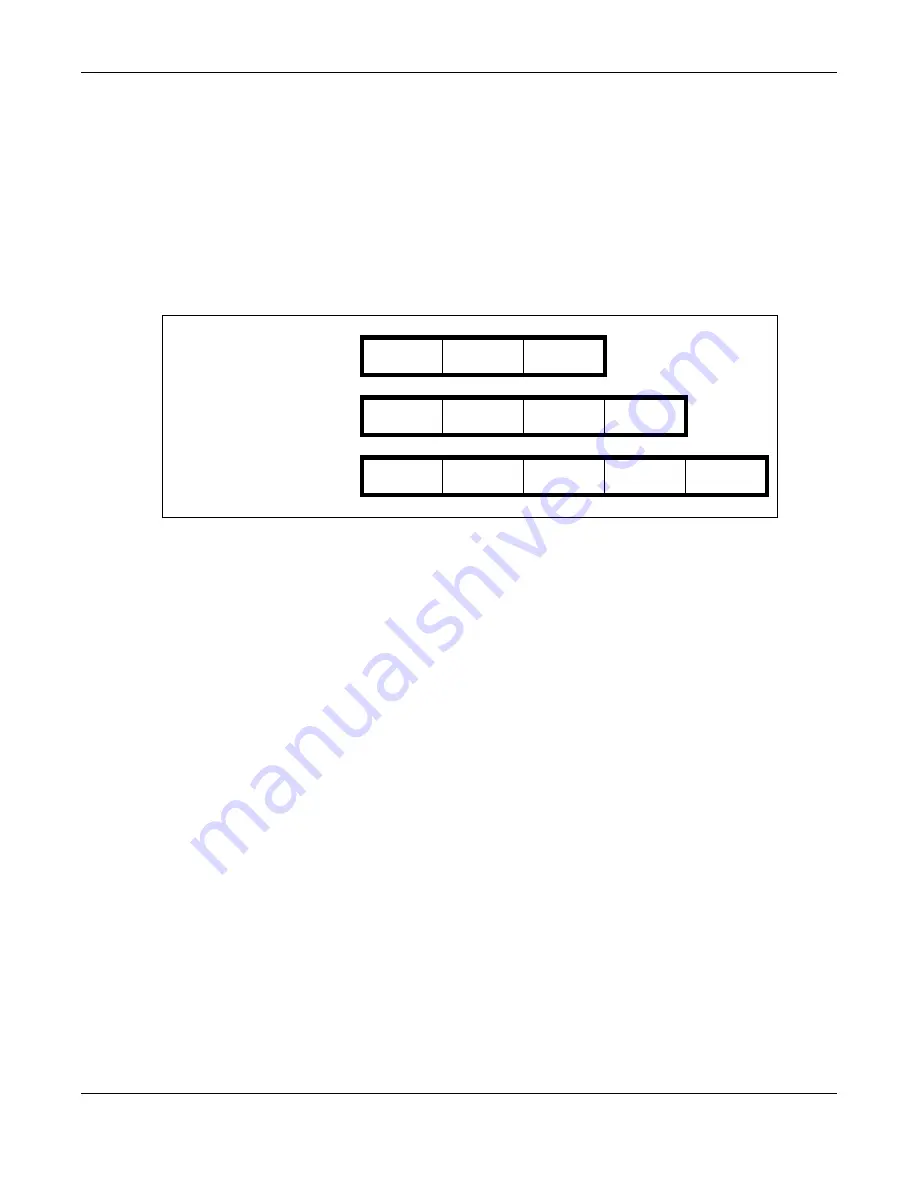
In tunnel mode, the UAG uses the active protocol to encapsulate the entire IP packet. As a result,
there are two IP headers:
• Outside header: The outside IP header contains the IP address of the UAG or remote IPSec
router, whichever is the destination.
• Inside header: The inside IP header contains the IP address of the computer behind the UAG or
remote IPSec router. The header for the active protocol (AH or ESP) appears between the IP
headers.
In transport mode, the encapsulation depends on the active protocol. With AH, the UAG includes
part of the original IP header when it encapsulates the packet. With ESP, however, the UAG does
not include the IP header when it encapsulates the packet, so it is not possible to verify the
integrity of the source IP address.
IPSec SA Proposal and Perfect Forward Secrecy
An IPSec SA proposal is similar to an IKE SA proposal (see
), except
that you also have the choice whether or not the UAG and remote IPSec router perform a new DH
key exchange every time an IPSec SA is established. This is called Perfect Forward Secrecy (PFS).
If you enable PFS, the UAG and remote IPSec router perform a DH key exchange every time an
IPSec SA is established, changing the root key from which encryption keys are generated. As a
result, if one encryption key is compromised, other encryption keys remain secure.
If you do not enable PFS, the UAG and remote IPSec router use the same root key that was
generated when the IKE SA was established to generate encryption keys.
The DH key exchange is time-consuming and may be unnecessary for data that does not require
such security.
Figure 249
VPN: Transport and Tunnel Mode Encapsulation
Original Packet
IP Header
TCP
Header
Data
Transport Mode Packet
IP Header
AH/ESP
Header
TCP
Header
Data
Tunnel Mode Packet
IP Header
AH/ESP
Header
IP Header
TCP
Header
Data
















































