Chapter 24 Web Authentication
UAG4100 User’s Guide
227
24.2.2 User-aware Access Control Example
You can configure many policies and security settings for specific users or groups of users. Users
can be authenticated locally by the UAG or by an external (RADIUS) authentication server.
In this example the users are authenticated by an external RADIUS server at 172.16.1.200. First,
set up the user accounts and user groups in the UAG. Then, set up user authentication using the
RADIUS server. Finally, set up the policies in the table above.
24.2.2.1 Set Up User Accounts
Set up user accounts in the RADIUS server. This example uses the Web Configurator. If you can
export user names from the RADIUS server to a text file, then you might configure a script to
create the user accounts instead.
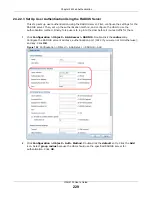
1
Click
Configuration > Object > User/Group > User
. Click the
Add
icon.
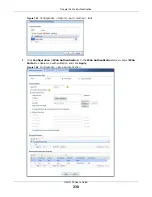
2
Enter the same user name that is used in the RADIUS server, and set the
User Type
to
ext-user
because this user account is authenticated by an external server. Click
OK
.
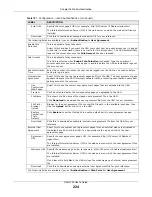
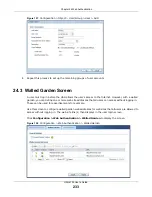
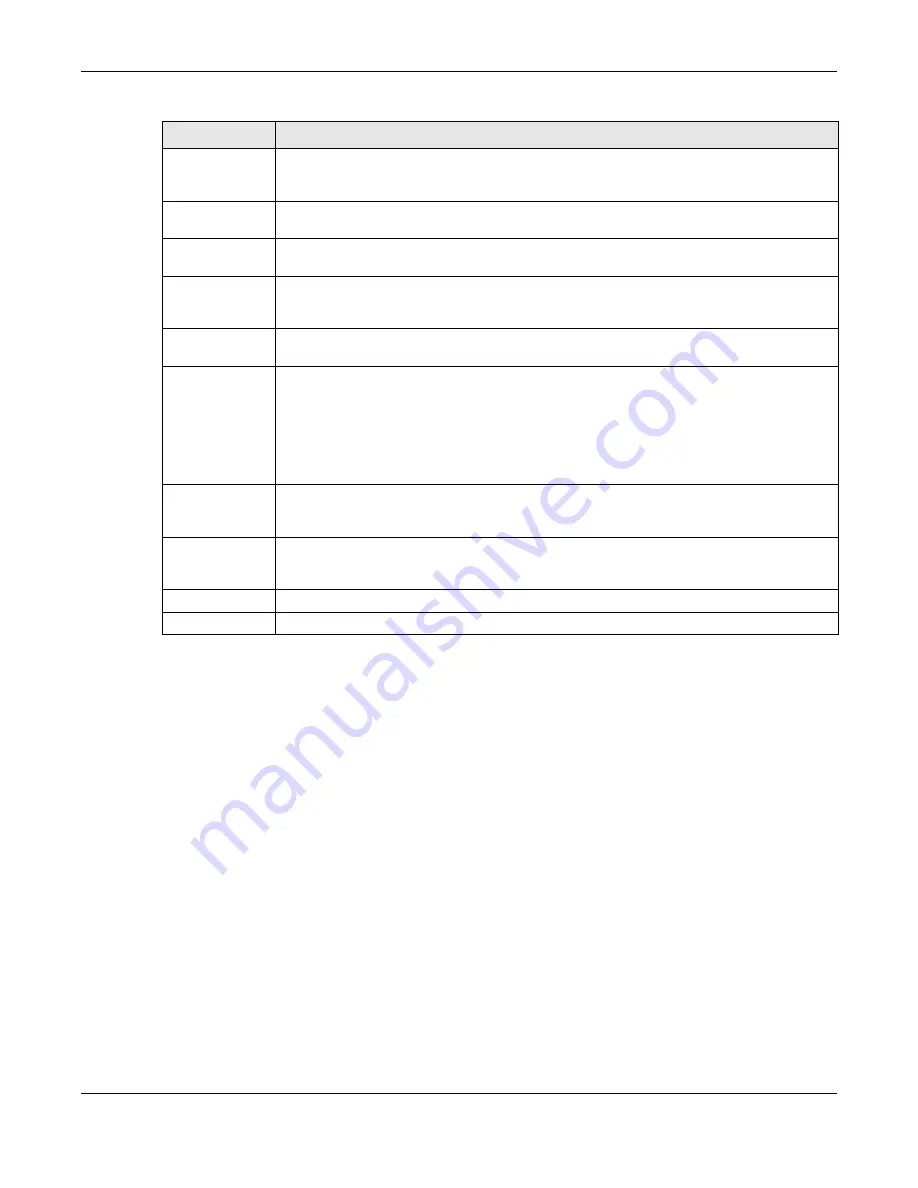
User
Authentication
Policy
Use this section of the screen to determine which traffic requires (or does not require) the
senders to be authenticated in order to be routed.
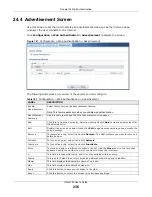
Incoming
Interface
Select an interface on which packets for the policy must be received. Select
any
if the
policy is effective for every interface.
Source Address
Select a source address or address group for whom this policy applies. Select
any
if the
policy is effective for every source. This is
any
and not configurable for the default policy.
Destination
Address
Select a destination address or address group for whom this policy applies. Select
any
if
the policy is effective for every destination. This is
any
and not configurable for the default
policy.
Schedule
Select a schedule that defines when the policy applies. Otherwise, select
none
and the rule
is always effective. This is
none
and not configurable for the default policy.
Authentication
Select the authentication requirement for users when their traffic matches this policy.
unnecessary
- Users do not need to be authenticated.
required
- Users need to be authenticated. If
Force User Authentication
is selected, all
HTTP traffic from unauthenticated users is redirected to a default or user-defined login
page. Otherwise, they must manually go to the login screen. The UAG will not redirect
them to the login screen.
Log
This field is available for the default policy. Select whether to have the UAG generate a log
(
log
), log and alert (
log alert
) or not (
no
) for packets that match the default policy. See
for more on logs.
Force User
Authentication
This field is available for user-configured policies that require authentication. Select this to
have the UAG automatically display the login screen when users who have not logged in yet
try to send HTTP traffic.
OK
Click
OK
to save your changes back to the UAG.
Cancel
Click
Cancel
to exit this screen without saving.
Table 102
Configuration > Web Authentication > Add (continued)
LABEL
DESCRIPTION