Chapter 30 IPSec VPN
UAG5100 User’s Guide
289
30.1.2 What You Need to Know
An IPSec VPN tunnel is usually established in two phases. Each phase establishes a security
association (SA), a contract indicating what security parameters the UAG and the remote IPSec
router will use. The first phase establishes an Internet Key Exchange (IKE) SA between the UAG
and remote IPSec router. The second phase uses the IKE SA to securely establish an IPSec SA
through which the UAG and remote IPSec router can send data between computers on the local
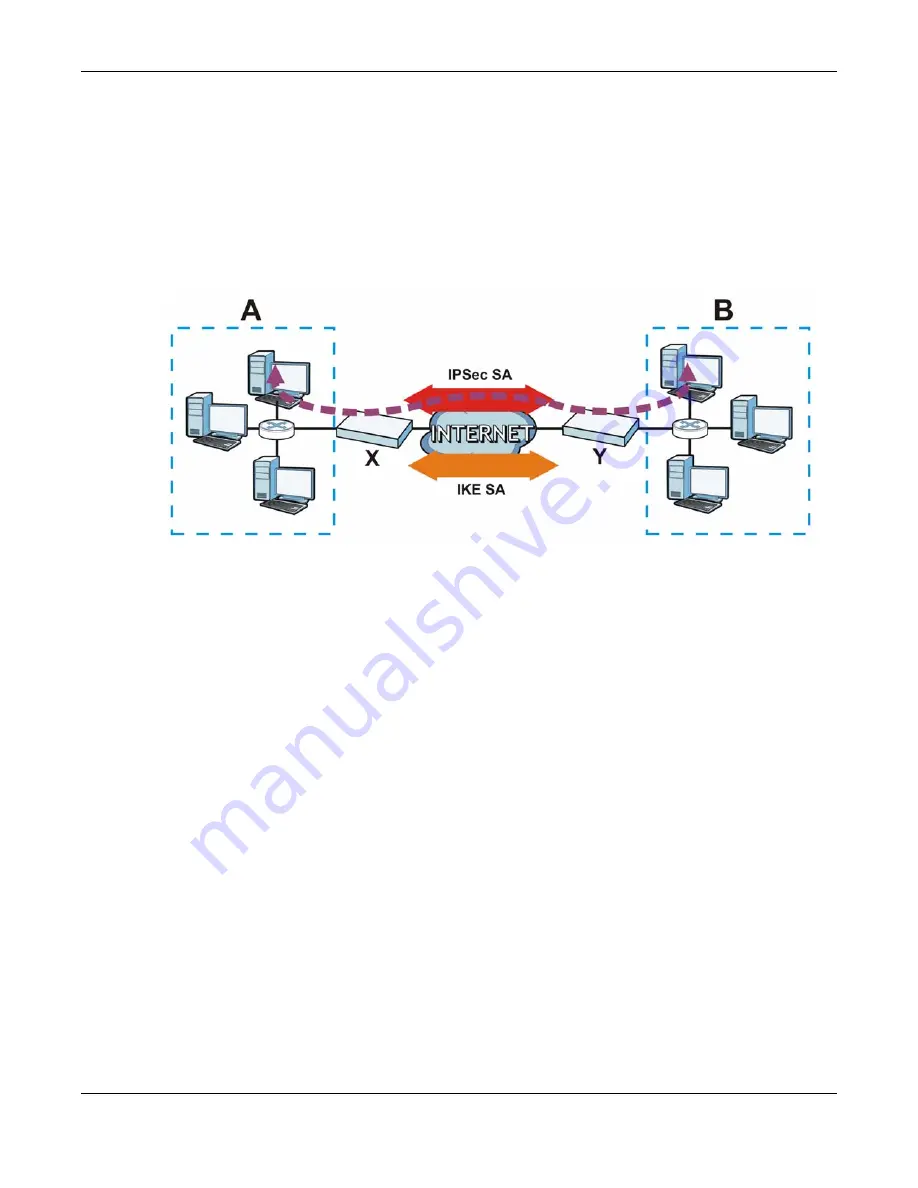
network and remote network. This is illustrated in the following figure.
Figure 199
VPN: IKE SA and IPSec SA
In this example, a computer in network A is exchanging data with a computer in network B. Inside
networks A and B, the data is transmitted the same way data is normally transmitted in the
networks. Between routers X and Y, the data is protected by tunneling, encryption, authentication,
and other security features of the IPSec SA. The IPSec SA is secure because routers X and Y
established the IKE SA first.
Finding Out More
for IPSec VPN background information.
• See the help in the IPSec VPN quick setup wizard screens.
30.1.3 Before You Begin
This section briefly explains the relationship between VPN tunnels and other features. It also gives
some basic suggestions for troubleshooting.
You should set up the following features before you set up the VPN tunnel.
• In any VPN connection, you have to select address objects to specify the local policy and remote
policy. You should set up the address objects first.
• In a VPN gateway, you can select an Ethernet interface, virtual Ethernet interface, VLAN
interface, or virtual VLAN interface to specify what address the UAG uses as its IP address when
it establishes the IKE SA. You should set up the interface first. See
.
• In a VPN gateway, you can enable extended authentication. If the UAG is in server mode, you
should set up the authentication method (AAA server) first. The authentication method specifies
how the UAG authenticates the remote IPSec router. See
















































