Chapter 27 Security Policy
ZyWALL USG Series User’s Guide
584
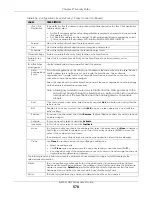
Figure 410
Configuration > Security Policy > ADP > Profile
The following table describes the labels in this screen.
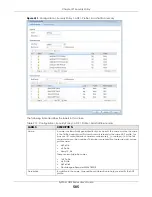
27.5.3 Traffic Anomaly Profiles
Traffic anomaly detection looks for abnormal behavior such as scan or flooding attempts. In the
Configuration > Security Policy > ADP > Profile
screen, click the
Edit
or
Add
icon and choose a base
profile.
Traffic Anomaly
is the first tab in the profile.
Table 209 Configuration > Security Policy > ADP > Profile
LABEL
DESCRIPTION
Profile Management
Create ADP profiles here and then apply them in the
Configuration > Security Policy
> ADP > Profile
screen.
Add
Click
Add
and first choose a
none
or
all
Base Profile
.
•
none
base profile sets all ADP entries to have
Log
set to
no
and
Action
set to
none
by default.
•
all
base profile sets all ADP entries to have
Log
set to
log
and
Action
set to
block
by default.
Edit
Select an entry and click this to be able to modify it.
Remove
Select an entry and click this to delete it.
Clone
Use
Clone
to create a new entry by modifying an existing one.
• Select an existing entry.
• Click
Clone
.
• A configuration copy of the selected entry pops up. You must at least change
the name as duplicate entry names are not allowed.
#
This is the entry’s index number in the list.
Name
This is the name of the profile you created.
Description
This is the description of the profile you created.
Base Profile
This is the name of the base profile used to create this profile.
Reference
This is the number of object references used to create this profile.
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...