Chapter 27 Security Policy
ZyWALL USG Series User’s Guide
586
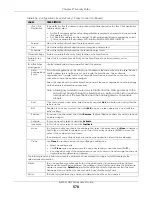
Scan/Flood Detection
Scan detection, such as port scanning, tries to find attacks where an attacker scans
device(s) to determine what types of network protocols or services a device
supports.
Flood detection tries to find attacks that saturate a network with useless data, use up
all available bandwidth, and so aim to make communications in the network
impossible.
Sensitivity
(Scan detection only.) Select a sensitivity level so as to reduce false positives in your
network. If you choose low sensitivity, then scan thresholds and sample times are set
low, so you will have fewer logs and false positives; however some traffic anomaly
attacks may not be detected.
If you choose high sensitivity, then scan thresholds and sample times are set high, so
most traffic anomaly attacks will be detected; however you will have more logs and
false positives.
Block Period
Specify for how many seconds the Zyxel Device blocks all packets from being sent
to the victim (destination) of a detected anomaly attack. Flood Detection applies
blocking to the destination IP address and Scan Detection applies blocking to the
source IP address.
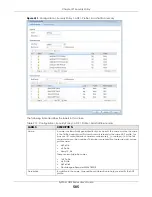
Edit (Flood Detection
only)
Select an entry and click this to be able to modify it.
Activate
To turn on an entry, select it and click
Activate
.
Inactivate
To turn off an entry, select it and click
Inactivate
.
Log
To edit an item’s log option, select it and use the
Log
icon. Select whether to have
the Zyxel Device generate a log (
log
), log and alert (
log alert
) or neither (
no
) when
traffic matches this anomaly policy.
Action
To edit what action the Zyxel Device takes when a packet matches a policy, select
the policy and use the
Action
icon.
none
: The Zyxel Device takes no action when a packet matches the policy.
block
: The Zyxel Device silently drops packets that matches the policy. Neither
sender nor receiver are notified.
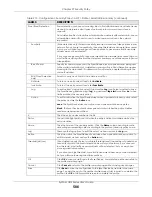
#
This is the entry’s index number in the list.
Status
The activate (light bulb) icon is lit when the entry is active and dimmed when the
entry is inactive.
Name
This is the name of the anomaly policy. Click the
Name
column heading to sort in
ascending or descending order according to the protocol anomaly policy name.
Log
These are the log options. To edit this, select an item and use the
Log
icon.
Action
This is the action the Zyxel Device should take when a packet matches a policy. To
edit this, select an item and use the
Action
icon.
Threshold (pkt/sec)
(Flood detection only.) Select a suitable threshold level (the number of packets per
second that match the flood detection criteria) for your network. If you choose a
low threshold, most traffic anomaly attacks will be detected, but you may have
more logs and false positives.
If you choose a high threshold, some traffic anomaly attacks may not be detected,
but you will have fewer logs and false positives.
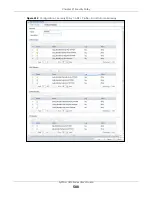
OK
Click
OK
to save your settings to the Zyxel Device, complete the profile and return to
the profile summary page.
Cancel
Click
Cancel
to return to the profile summary page without saving any changes.
Save
Click
Save
to save the configuration to the Zyxel Device but remain in the same
page. You may then go to the another profile screen (tab) in order to complete the
profile. Click
OK
in the final profile screen to complete the profile.
Table 210 Configuration > Security Policy > ADP > Profile > Add-Traffic-Anomaly (continued)
LABELS
DESCRIPTION
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...