Chapter 30 IPSec VPN
ZyWALL USG Series User’s Guide
632
Note: Both routers must use the same negotiation mode.
These modes are discussed in more detail in
. Main mode is used in various examples
in the rest of this section.
The Zyxel Device supports IKEv1 and IKEv2. See
for more information.
IP Addresses of the Zyxel Device and Remote IPSec Router
To set up an IKE SA, you have to specify the IP addresses of the Zyxel Device and remote IPSec router.
You can usually enter a static IP address or a domain name for either or both IP addresses. Sometimes,
your Zyxel Device might offer another alternative, such as using the IP address of a port or interface, as
well.
You can also specify the IP address of the remote IPSec router as 0.0.0.0. This means that the remote
IPSec router can have any IP address. In this case, only the remote IPSec router can initiate an IKE SA
because the Zyxel Device does not know the IP address of the remote IPSec router. This is often used for
telecommuters.
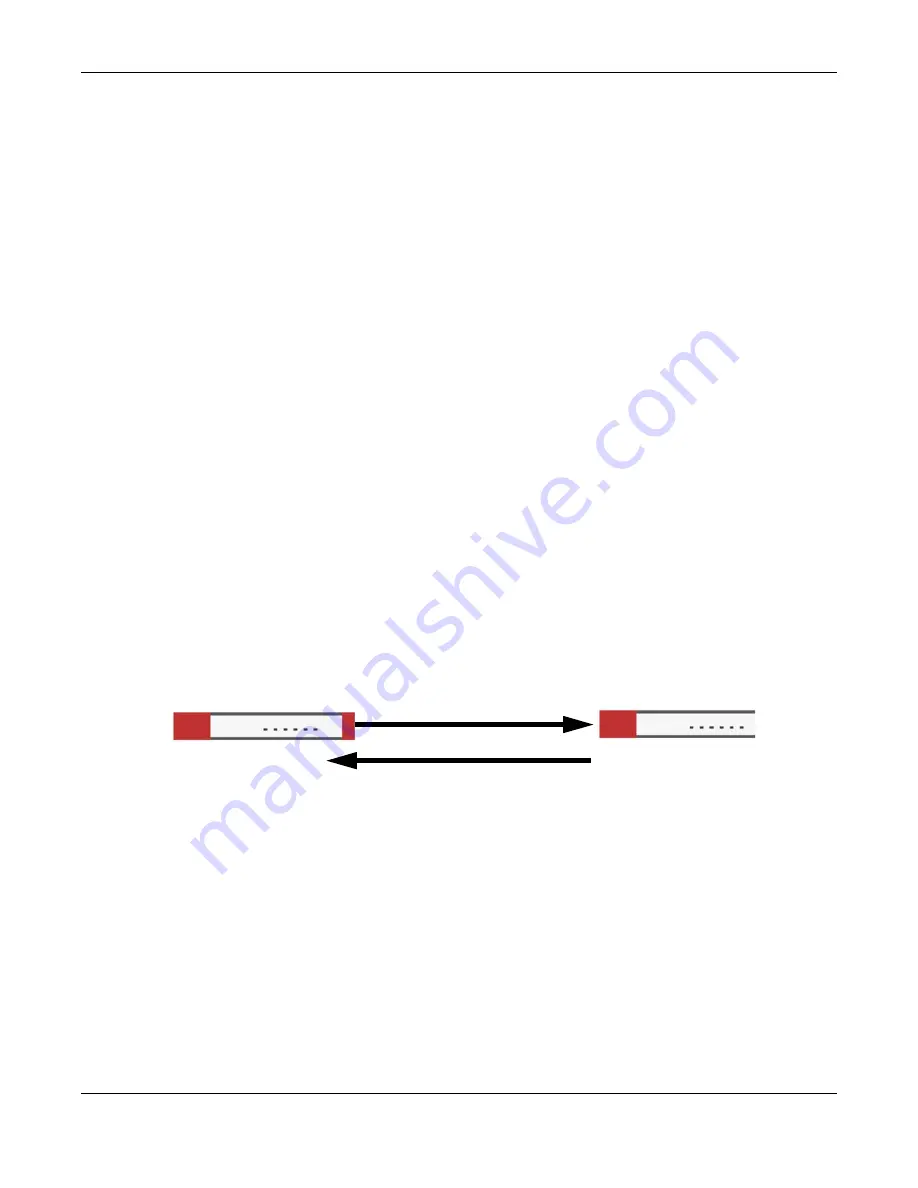
IKE SA Proposal
The IKE SA proposal is used to identify the encryption algorithm, authentication algorithm, and Diffie-
Hellman (DH) key group that the Zyxel Device and remote IPSec router use in the IKE SA. In main mode,
this is done in steps 1 and 2, as illustrated next.
Figure 438
IKE SA: Main Negotiation Mode, Steps 1 - 2: IKE SA Proposal
The Zyxel Device sends one or more proposals to the remote IPSec router. (In some devices, you can
only set up one proposal.) Each proposal consists of an encryption algorithm, authentication algorithm,
and DH key group that the Zyxel Device wants to use in the IKE SA. The remote IPSec router selects an
acceptable proposal and sends the accepted proposal back to the Zyxel Device. If the remote IPSec
router rejects all of the proposals, the Zyxel Device and remote IPSec router cannot establish an IKE SA.
Note: Both routers must use the same encryption algorithm, authentication algorithm, and DH
key group.
In most Zyxel Devices, you can select one of the following encryption algorithms for each proposal. The
algorithms are listed in order from weakest to strongest.
• Data Encryption Standard (DES) is a widely used method of data encryption. It applies a 56-bit key to
each 64-bit block of data.
One or more proposals, each one consisting of:
- encryption algorithm
- authentication algorithm
- Diffie-Hellman key group
1
2
X
Y
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...