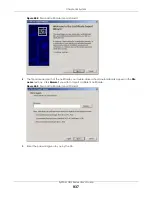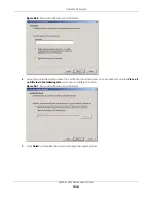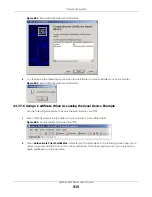
Chapter 44 System
ZyWALL USG Series User’s Guide
942
3
Authentication and Data Transmission
After the identification is verified and data encryption activated, a secure tunnel is established between
the client and the server. The client then sends its authentication information (user name and password)
to the server to log in to the server.
44.8.2 SSH Implementation on the Zyxel Device
Your Zyxel Device supports SSH versions 1 and 2 using RSA authentication and four encryption methods
(AES, 3DES, Archfour, and Blowfish). The SSH server is implemented on the Zyxel Device for management
using port 22 (by default).
44.8.3 Requirements for Using SSH
You must install an SSH client program on a client computer (Windows or Linux operating system) that is
used to connect to the Zyxel Device over SSH.
44.8.4 Configuring SSH
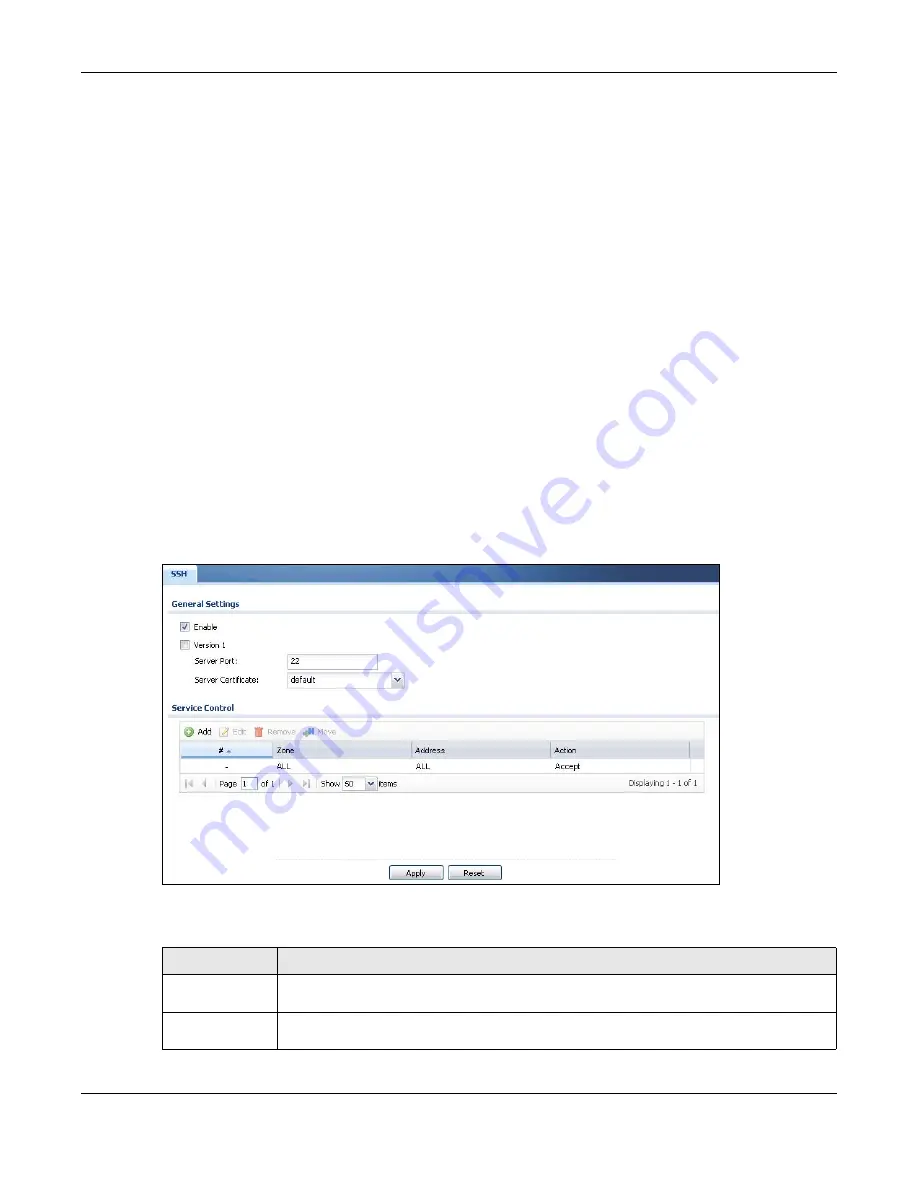
Click
Configuration > System > SSH
to change your Zyxel Device’s Secure Shell settings. Use this screen to
specify from which zones SSH can be used to manage the Zyxel Device. You can also specify from
which IP addresses the access can come.
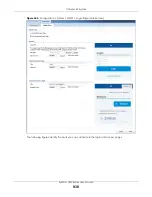
Figure 669
Configuration > System > SSH
The following table describes the labels in this screen.
Table 377 Configuration > System > SSH
LABEL
DESCRIPTION
Enable
Select the check box to allow or disallow the computer with the IP address that matches the IP
address(es) in the
Service Control
table to access the Zyxel Device CLI using this service.
Version 1
Select the check box to have the Zyxel Device use both SSH version 1 and version 2 protocols.
If you clear the check box, the Zyxel Device uses only SSH version 2 protocol.
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...