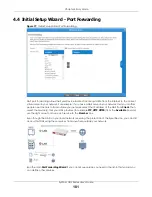
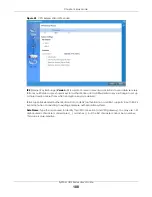
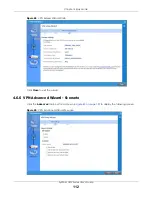
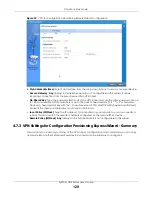
Chapter 4 Easy Mode
ZyWALL USG Series User’s Guide
114
•
Negotiation Mode
: This displays
Main
or
Aggressive
:
•
Main
encrypts the ZyWALL/USG’s and remote IPSec router’s identities but takes more time to
establish the IKE SA
•
Aggressive
is faster but does not encrypt the identities.
The ZyWALL/USG and the remote IPSec router must use the same negotiation mode. Multiple SAs
connecting through a secure gateway must have the same negotiation mode.
•
Encryption Algorithm
:
3DES
and
AES
use encryption. The longer the key, the higher the security (this
may affect throughput). Both sender and receiver must use the same secret key, which can be used
to encrypt and decrypt the message or to generate and verify a message authentication code. The
DES encryption algorithm uses a 56-bit key. Triple DES (
3DES
) is a variation on DES that uses a 168-bit
key. As a result, 3DES is more secure than DES. It also requires more processing power, resulting in
increased latency and decreased throughput. A
ES128
uses a 128-bit key and is faster than 3DES.
AES192 uses a 192-bit key, and AES256 uses a 256-bit key.
•
Authentication Algorithm
:
MD5
gives minimal security and
SHA512
gives the highest security. MD5
(Message Digest 5) and SHA (Secure Hash Algorithm) are hash algorithms used to authenticate
packet data. The stronger the algorithm the slower it is.
•
Key Group
:
DH5
is more secure than
DH1
or
DH2
(although it may affect throughput). DH1 (default)
refers to Diffie-Hellman Group 1 a 768 bit random number. DH2 refers to Diffie-Hellman Group 2 a 1024
bit (1Kb) random number. DH5 refers to Diffie-Hellman Group 5 a 1536 bit random number.
•
SA Life Time
: Set how often the Zyxel Device renegotiates the IKE SA. A short SA life time increases
security, but renegotiation temporarily disconnects the VPN tunnel.
•
NAT Traversal
: Select this if the VPN tunnel must pass through NAT (there is a NAT router between the
IPSec devices).
Note: The remote IPSec device must also have NAT traversal enabled. See the help in the
main IPSec VPN screens for more information.
•
Dead Peer Detection (DPD)
has the Zyxel Device make sure the remote IPSec device is there before
transmitting data through the IKE SA. If there has been no traffic for at least 15 seconds, the Zyxel
Device sends a message to the remote IPSec device. If it responds, the Zyxel Device transmits the
data. If it does not respond, the Zyxel Device shuts down the IKE SA.
•
Authentication Method
: Select
Pre-Shared Key
to use a password or
Certificate
to use one of the Zyxel
Device’s certificates.
4.6.8 VPN Advanced Wizard - Phase 2
Phase 2 in an IKE uses the SA that was established in phase 1 to negotiate SAs for IPSec.
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...