Chapter 6 Dashboard
ZyWALL USG Series User’s Guide
193
This table describes the fields in the above screen.
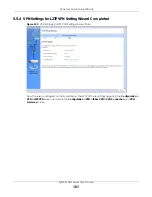
6.2.11 Top 5 Intrusions Screen
Figure 164
Dashboard > Top 5 Intrusions
This table describes the fields in the above screen.
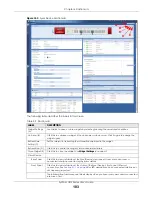
6.2.12 Top 5 IPv4/IPv6 Security Policy Rules that Blocked Traffic Screen
Figure 165
Dashboard > Top 5 IPv4/IPv6 Security Policy Rules that Blocked Traffic
This table describes the fields in the above screen.
Table 32 Dashboard > Top 5 Viruses
LABEL
DESCRIPTION
#
This is the entry’s rank in the list of the most commonly detected viruses.
Virus Name
This is the name of a detected virus.
Hits
This is how many times the Zyxel Device has detected the event described in the
entry.
Table 33 Dashboard > Top 5 Intrusions
LABEL
DESCRIPTION
#
This is the entry’s rank in the list of the most commonly triggered signature policies.
Signature ID
This is the identification number of the signature.
Signature Name
This is the name of the signature.
Type
This is the type of the signature, for example
Schedule
.
Severity
This is the level of threat that the intrusions may pose.
Hits
This is how many times the Zyxel Device has detected the event described in the
entry.
Table 34 Dashboard > Top 5 IPv4/IPv6 Security Policy Rules that Blocked Traffic
LABEL
DESCRIPTION
#
This is the entry’s rank in the list of the most commonly triggered security policies.
From
This shows the zone packets came from that the triggered security policy.
To
This shows the zone packets went to that the triggered security policy.
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...