Chapter 30 IPSec VPN
ZyWALL USG Series User’s Guide
623
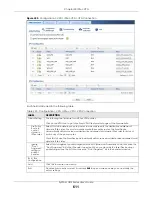
Pre-Shared Key
Select this to have the Zyxel Device and remote IPSec router use a pre-shared key
(password) of up to 128 characters to identify each other when they negotiate the IKE SA.
Type the pre-shared key in the field to the right. The pre-shared key can be:
• alphanumeric characters or ,;.|`~!@#$%^&*()_+\{}':./<>=-"
• pairs of hexadecimal (0-9, A-F) characters, preceded by “0x”.
Type “0x” at the beginning of a hexadecimal key. For example, "0x0123456789ABCDEF" is in
hexadecimal format; “0123456789ABCDEF” is in ASCII format. If you use hexadecimal, you
must enter twice as many characters since you need to enter pairs.
The Zyxel Device and remote IPSec router must use the same pre-shared key.
Select
unmasked
to see the pre-shared key in readable plain text.
Certificate
Select this to have the Zyxel Device and remote IPSec router use certificates to
authenticate each other when they negotiate the IKE SA. Then select the certificate the
Zyxel Device uses to identify itself to the remote IPSec router.
This certificate is one of the certificates in
My Certificates
. If this certificate is self-signed,
import it into the remote IPsec router. If this certificate is signed by a CA, the remote IPsec
router must trust that CA.
Note: The IPSec routers must trust each other’s certificates.
The Zyxel Device uses one of its
Trusted Certificates
to authenticate the remote IPSec
router’s certificate. The trusted certificate can be a self-signed certificate or that of a
trusted CA that signed the remote IPSec router’s certificate.
User-based PSK
User-based PSK (IKEv1 only) generates and manages separate pre-shared keys for every
user. This enables multiple users, each with a unique key, to access the same VPN gateway
policy with one-to-one authentication and strong encryption. Access can be denied on a
per-user basis thus allowing VPN SA user-based policies. Click
User-Based PSK
then select a
user or group object who is allowed VPN SA access using this VPN gateway policy. This is for
IKEv1 only.
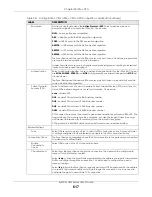
Local ID Type
This field is read-only if the Zyxel Device and remote IPSec router use certificates to identify
each other. Select which type of identification is used to identify the Zyxel Device during
authentication. Choices are:
IPv4
or
IPv6
- the Zyxel Device is identified by an IP address
DNS
- the Zyxel Device is identified by a domain name
- the Zyxel Device is identified by the string specified in this field
Content
This field is read-only if the Zyxel Device and remote IPSec router use certificates to identify
each other. Type the identity of the Zyxel Device during authentication. The identity
depends on the
Local ID Type
.
IP
- type an IP address; if you type 0.0.0.0, the Zyxel Device uses the IP address specified in
the
My Address
field. This is not recommended in the following situations:
• There is a NAT router between the Zyxel Device and remote IPSec router.
• You want the remote IPSec router to be able to distinguish between IPSec SA requests
that come from IPSec routers with dynamic WAN IP addresses.
In these situations, use a different IP address, or use a different
Local ID Type
.
DNS
- type the fully qualified domain name (FQDN). This value is only used for identification
and can be any string that matches the peer ID string.
- the Zyxel Device is identified by the string you specify here; you can use up to 63
ASCII characters including spaces, although trailing spaces are truncated. This value is only
used for identification and can be any string.
Table 223 Configuration > VPN > IPSec VPN > VPN Gateway > Add/Edit (continued)
LABEL
DESCRIPTION
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...