Chapter 18 Port Authentication
XS1930 Series User’s Guide
170
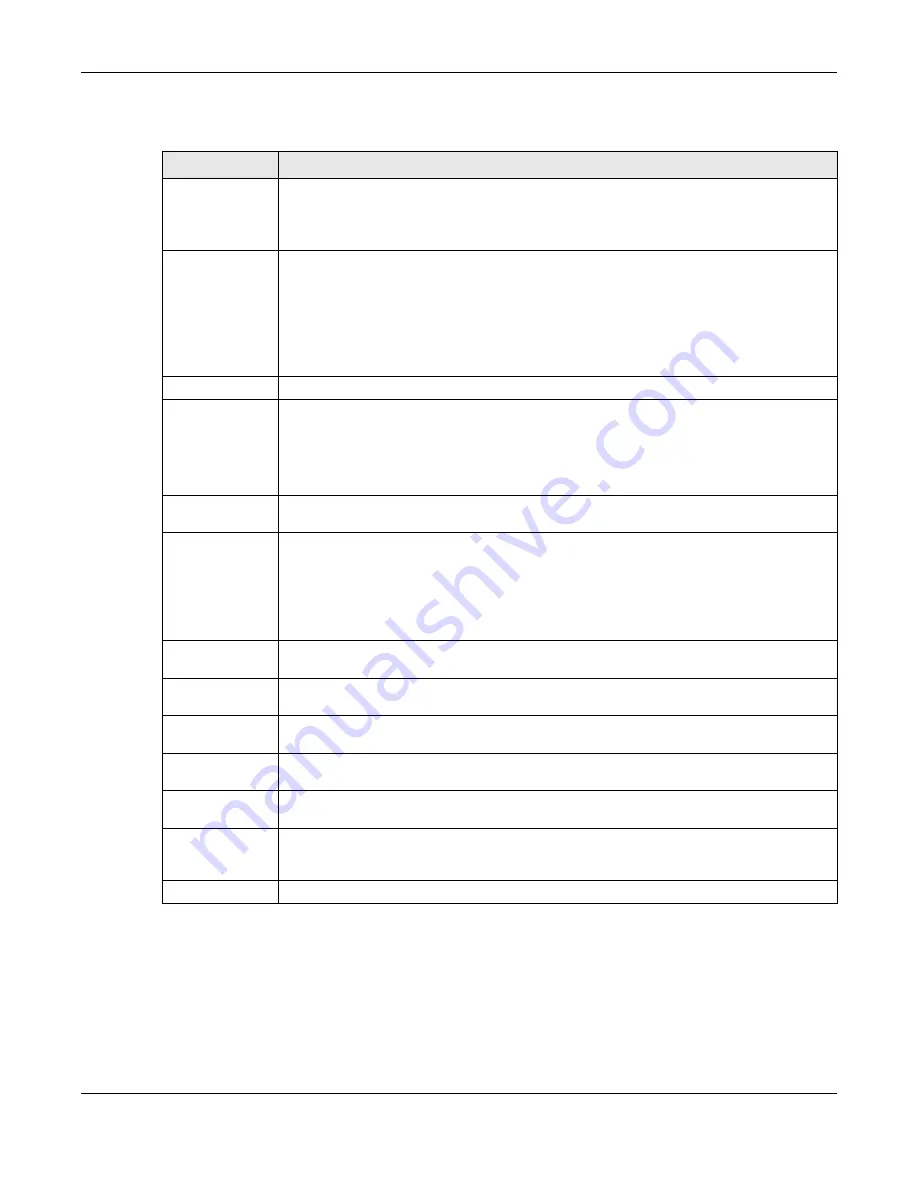
The following table describes the labels in this screen.
18.3.1 Guest VLAN
When 802.1x port authentication is enabled on the Switch and its ports, clients that do not have the
correct credentials are blocked from using the port(s). You can configure your Switch to have one VLAN
that acts as a guest VLAN. If you enable the guest VLAN (
102
in the example) on a port (
2
in the
example), the user (
A
in the example) that is not IEEE 802.1x capable or fails to enter the correct
username and password can still access the port, but traffic from the user is forwarded to the guest
VLAN. That is, unauthenticated users can have access to limited network resources in the same guest
Table 76 Advanced Application > Port Authentication > 802.1x
LABEL
DESCRIPTION
Active
Select this check box to permit 802.1x authentication on the Switch.
Note: You must first enable 802.1x authentication on the Switch before configuring it
on each port.
EAPOL flood
Select this check box to flood EAPoL packets to all ports in the same VLAN.
EAP over LAN (EAPOL) is a port authentication protocol used in IEEE 802.1x. It is used to
encapsulate and transmit EAP packets between the supplicant (a client device that requests
access to the network resources or services) and authenticator (the Switch) directly over the
LAN.
Note:
EAPOL flood
will not take effect when 802.1x authentication is enabled.
Port
This field displays the port number. * means all ports.
*
Settings in this row apply to all ports.
Use this row only if you want to make some settings the same for all ports. Use this row first to set
the common settings and then make adjustments on a port-by-port basis.
Note: Changes in this row are copied to all the ports as soon as you make them.
Active
Select this to permit 802.1x authentication on this port. You must first allow 802.1x
authentication on the Switch before configuring it on each port.
Max-Req
Specify the number of times the Switch tries to authenticate client(s) before sending
unresponsive ports to the Guest VLAN.
This is set to 2 by default. That is, the Switch attempts to authenticate a client twice. If the client
does not respond to the first authentication request, the Switch tries again. If the client still does
not respond to the second request, the Switch sends the client to the Guest VLAN. The client
needs to send a new request to be authenticated by the Switch again.
Reauth
Specify if a subscriber has to periodically re-enter his or her username and password to stay
connected to the port.
Reauth-period
secs
Specify the length of time required to pass before a client has to re-enter his or her username
and password to stay connected to the port.
Quiet-period secs Specify the number of seconds the port remains in the HELD state and rejects further
authentication requests from the connected client after a failed authentication exchange.
Tx-period secs
Specify the number of seconds the Switch waits for client’s response before re-sending an
identity request to the client.
Supp-Timeout
secs
Specify the number of seconds the Switch waits for client’s response to a challenge request
before sending another request.
Apply
Click
Apply
to save your changes to the Switch’s run-time memory. The Switch loses these
changes if it is turned off or loses power, so use the
Save
link on the top navigation panel to
save your changes to the non-volatile memory when you are done configuring.
Cancel
Click
Cancel
to begin configuring this screen afresh.
















































