ZyAIR G-300 User’s Guide
Z Management with Wireless Zero Configuration
For added security, certificate-based authentications (EAP-TLS, EAP-TTLS and PEAP) use dynamic keys
for data encryption. They are often deployed in corporate environments, but for public deployment, a
simple user name and password pair is more practical. The following table is a comparison of the features
of five authentication types.
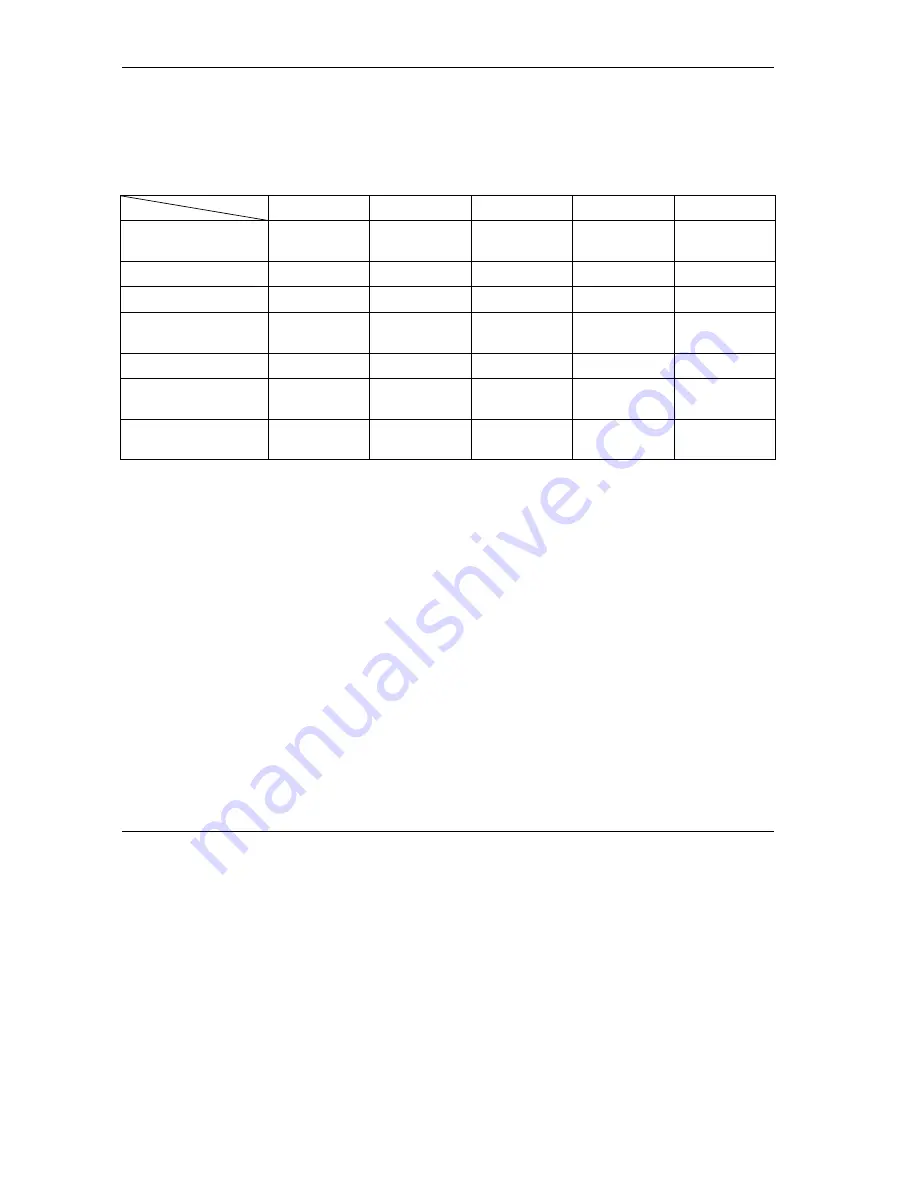
Comparison of EAP Authentication Types
EAP-MD5
EAP-TLS
EAP-TTLS
PEAP
LEAP
Mutual
Authentication
No Yes Yes Yes Yes
Certificate – Client
No Yes
Optional
Optional
No
Certificate – Server
No Yes Yes Yes No
Dynamic Key
Exchange
No Yes Yes Yes Yes
Credential Integrity
None Strong Strong Strong
Moderate
Deployment
Difficulty
Easy
Hard Moderate Moderate Moderate
Client Identity
Protection
No No Yes Yes No
Summary of Contents for ZYAIR G-300
Page 1: ...ZyAIR G 300 Wireless LAN PCI Adapter User s Guide Version 2 00 October 2004 ...
Page 6: ......
Page 38: ......
Page 40: ......
Page 50: ......