G-3000H User’s Guide
Chapter 17 LAN Setup
169
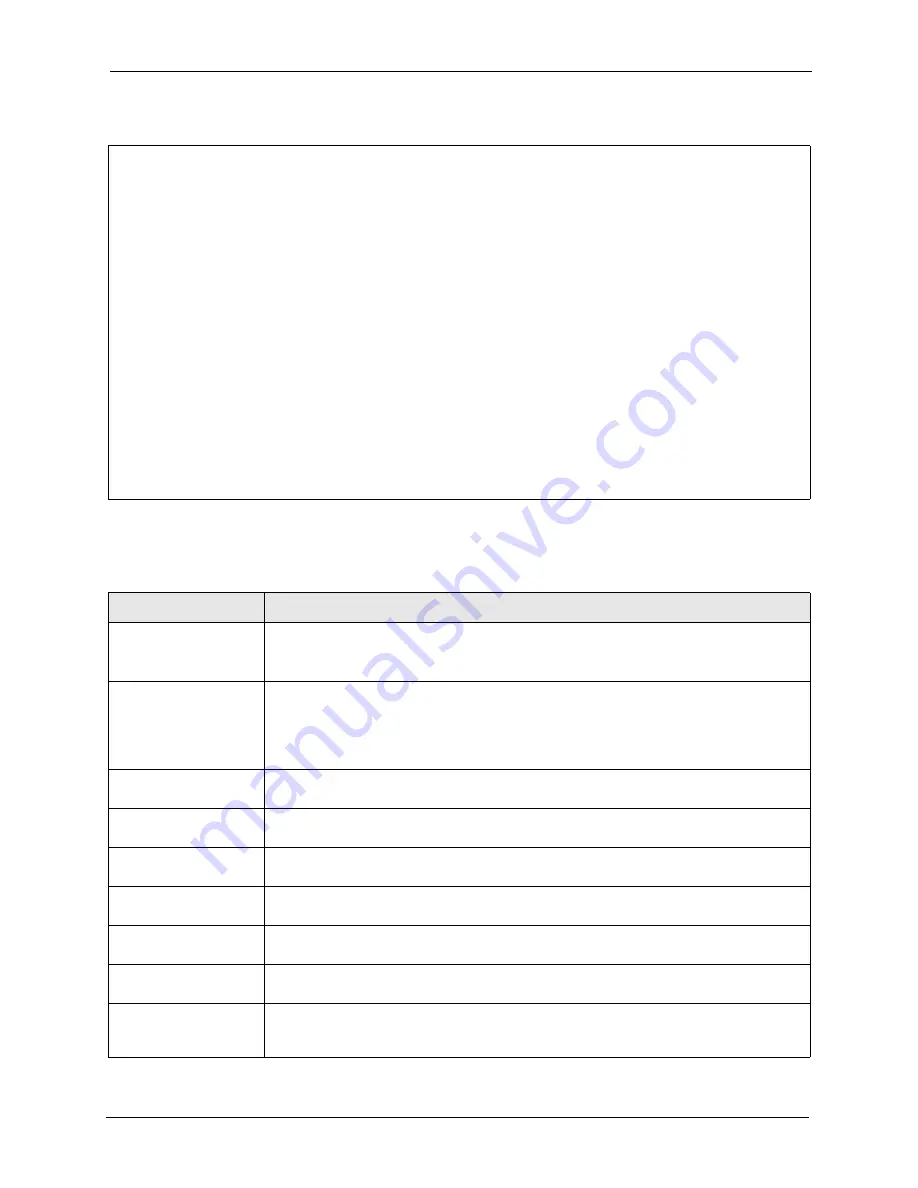
Figure 110
Menu 3.5 Wireless LAN Setup
The following table describes the fields in this menu.
Menu 3.5 - Wireless LAN Setup
Edit MAC Address Filter= N/A
Operating Mode= Bridge / Repeater Edit Roaming Configuration= N/A
Edit SSID Profile= N/A
Hide Name (SSID)= N/A Select SSID Profile= N/A
Channel ID= CH06 2437MHz Edit Bridge Link Configuration= No
RTS Threshold= 2432 Preamble= Long
Frag. Threshold= 2432 802.11 Mode= Mixed
Max. Frame Burst= 650
Breathing LED= Yes
Block Intra-BSS Traffic= No
Output Power= <11b>17dBm/<11g>13dBm
Edit Layer-2 Isolation= N/A
Press ENTER to Confirm or ESC to Cancel:
Press Space Bar to Toggle.
Table 64
Menu 3.5 Wireless LAN Setup
FIELD
DESCRIPTION
Operating Mode
Press [SPACE BAR] and select
Access Point
,
Bridge / Repeater
,
AP + Bridge
or
MESSID
.
This field is not available on all models.
Name (SSID)
The SSID (Service Set IDentity) identifies the AP to which the wireless stations associate.
Wireless stations associating to the AP must have the same SSID. Enter a descriptive
name of up to 32 printable 7-bit ASCII characters.
This field is only available when you select
Access Point
or
AP + Bridge
in the
Operating
Mode
field.
Hide Name (SSID)
Press [SPACE BAR] and select
Yes
to hide the SSID in the outgoing data frame so an
intruder cannot obtain the SSID through scanning.
Channel ID
Press [SPACE BAR] to select a channel. This allows you to set the operating frequency/
channel depending on your particular region.
RTS Threshold
Setting this attribute to zero turns on the RTS/CTS handshake. Enter a value between 800
and 2432.
Frag. Threshold
This is the maximum data fragment size that can be sent. Enter a value between 256 and
2432.
Edit MAC Address Filter Press [SPACE BAR] to select
Yes
and press [ENTER] to display
Menu 3.5.1 - WLAN
MAC Address Filter
.
Edit Bridge Link
Configuration
Use [SPACE BAR] to choose
Yes
and press [ENTER] to go to
Menu 3.5.4 - Bridge Link
Configuration
.
Edit Roaming
Configuration
Use [SPACE BAR] to choose
Yes
and press [ENTER] to go to
Menu 3.5.2 - Roaming
Configuration
. This field is not available when you select
Bridge / Repeater
in the
Operating Mode
field.
Summary of Contents for ZyAIR G-3000H
Page 1: ...G 3000H 802 11g Wireless Access Point User s Guide Version 3 50 1 2006 ...
Page 22: ...G 3000H User s Guide 22 List of Figures ...
Page 26: ...G 3000H User s Guide 26 List of Tables ...
Page 114: ...G 3000H User s Guide 114 Chapter 9 VLAN ...
Page 134: ...G 3000H User s Guide 134 Chapter 11 Certificates ...
Page 164: ...G 3000H User s Guide 164 Chapter 15 Introducing the SMT ...
Page 180: ...G 3000H User s Guide 180 Chapter 17 LAN Setup ...
Page 218: ...G 3000H User s Guide 218 Chapter 24 System Maintenance and Information ...
Page 224: ...G 3000H User s Guide 224 Appendix C Power over Ethernet PoE Specifications ...
Page 226: ...G 3000H User s Guide 226 Appendix D Brute Force Password Guessing Protection ...
Page 238: ...G 3000H User s Guide 238 Appendix E Setting up Your Computer s IP Address ...
Page 242: ...G 3000H User s Guide 242 Appendix F IP Address Assignment Conflicts ...
Page 254: ...G 3000H User s Guide 254 Appendix G Wireless LANs ...
Page 262: ...G 3000H User s Guide 262 Appendix H IP Subnetting ...
Page 264: ...G 3000H User s Guide 264 Appendix I Command Interpreter ...
Page 268: ...G 3000H User s Guide 268 Appendix J Log Descriptions ...
Page 272: ...G 3000H User s Guide 272 Appendix L Power Adaptor Specifications ...
Page 280: ...G 3000H User s Guide 280 Appendix M Text File Based Auto Configuration ...
Page 294: ...G 3000H User s Guide 294 Appendix N Wireless LAN Manager ...
Page 299: ...G 3000H User s Guide Index 299 ZyNOS F W Version 196 zyxel prowireless mib 287 ...
















































