Appendix D Importing Certificates
ZyWALL USG 100/200 Series User’s Guide
1048
3
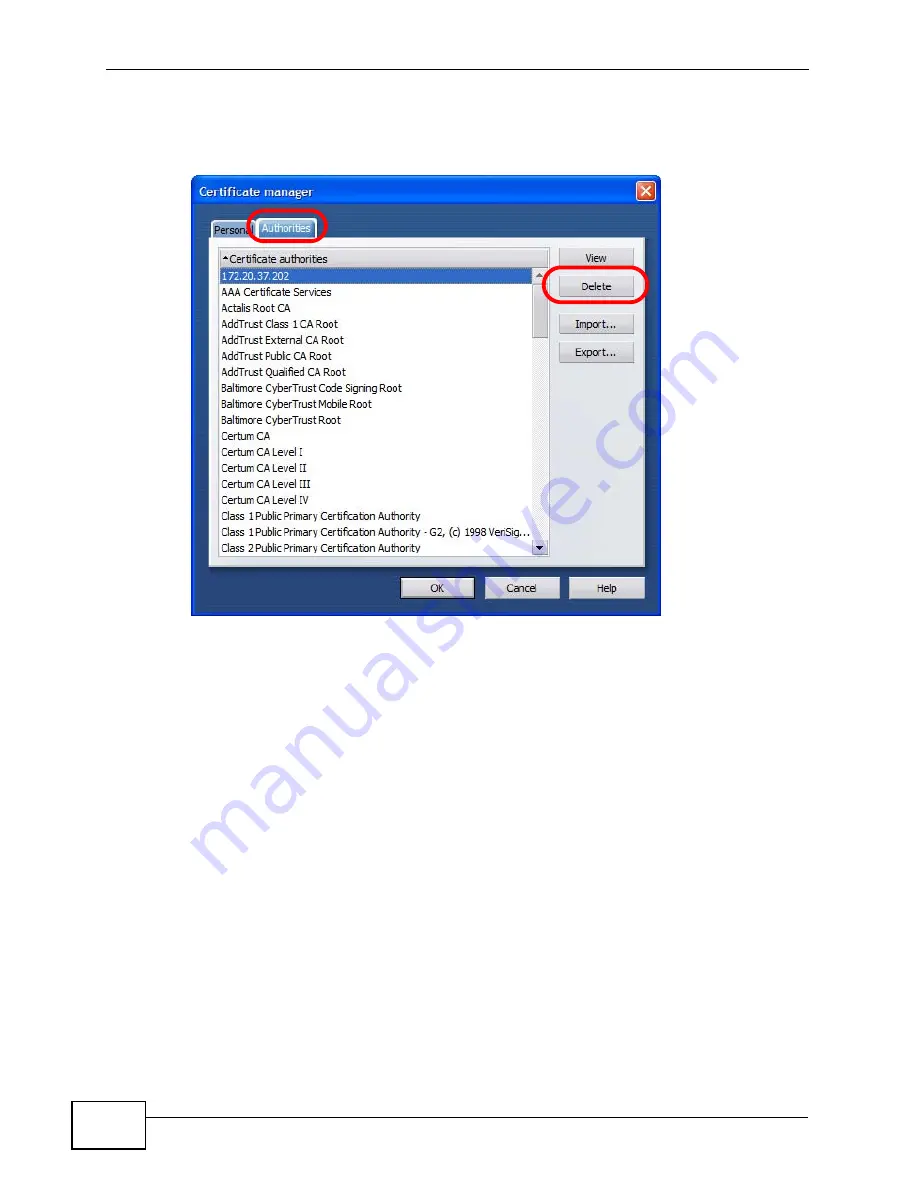
In the
Certificates manager
, select the
Authorities
tab, select the certificate
that you want to remove, and then click
Delete
.
Figure 660
Opera 9: Certificate manager
4
The next time you go to the web site that issued the public key certificate you just
removed, a certification error appears.
Note: There is no confirmation when you delete a certificate authority, so be
absolutely certain that you want to go through with it before clicking the button.
Konqueror
The following example uses Konqueror 3.5 on openSUSE 10.3, however the
screens apply to Konqueror 3.5 on all Linux KDE distributions.
1
If your device’s Web Configurator is set to use SSL certification, then the first time
you browse to it you are presented with a certification error.
Summary of Contents for ZyWALL USG 100 Series
Page 2: ......
Page 30: ...Table of Contents ZyWALL USG 100 200 Series User s Guide 30 ...
Page 31: ...31 PART I User s Guide ...
Page 32: ...32 ...
Page 46: ...Chapter 2 Features and Applications ZyWALL USG 100 200 Series User s Guide 46 ...
Page 64: ...Chapter 3 Web Configurator ZyWALL USG 100 200 Series User s Guide 64 ...
Page 186: ...Chapter 7 Tutorials ZyWALL USG 100 200 Series User s Guide 186 ...
Page 223: ...Chapter 8 L2TP VPN Example ZyWALL USG 100 200 Series User s Guide 223 ...
Page 224: ...Chapter 8 L2TP VPN Example ZyWALL USG 100 200 Series User s Guide 224 ...
Page 225: ...225 PART II Technical Reference ...
Page 226: ...226 ...
Page 240: ...Chapter 9 Dashboard ZyWALL USG 100 200 Series User s Guide 240 ...
Page 284: ...Chapter 10 Monitor ZyWALL USG 100 200 Series User s Guide 284 ...
Page 372: ...Chapter 13 Interfaces ZyWALL USG 100 200 Series User s Guide 372 ...
Page 382: ...Chapter 14 Trunks ZyWALL USG 100 200 Series User s Guide 382 ...
Page 398: ...Chapter 15 Policy and Static Routes ZyWALL USG 100 200 Series User s Guide 398 ...
Page 412: ...Chapter 16 Routing Protocols ZyWALL USG 100 200 Series User s Guide 412 ...
Page 432: ...Chapter 19 NAT ZyWALL USG 100 200 Series User s Guide 432 ...
Page 437: ...Chapter 20 HTTP Redirect ZyWALL USG 100 200 Series User s Guide 437 ...
Page 438: ...Chapter 20 HTTP Redirect ZyWALL USG 100 200 Series User s Guide 438 ...
Page 460: ...Chapter 23 Authentication Policy ZyWALL USG 100 200 Series User s Guide 460 ...
Page 478: ...Chapter 24 Firewall ZyWALL USG 100 200 Series User s Guide 478 ...
Page 519: ...Chapter 25 IPSec VPN ZyWALL USG 100 200 Series User s Guide 519 ...
Page 520: ...Chapter 25 IPSec VPN ZyWALL USG 100 200 Series User s Guide 520 ...
Page 534: ...Chapter 26 SSL VPN ZyWALL USG 100 200 Series User s Guide 534 ...
Page 544: ...Chapter 27 SSL User Screens ZyWALL USG 100 200 Series User s Guide 544 ...
Page 546: ...Chapter 28 SSL User Application Screens ZyWALL USG 100 200 Series User s Guide 546 ...
Page 554: ...Chapter 29 SSL User File Sharing ZyWALL USG 100 200 Series User s Guide 554 ...
Page 639: ...Chapter 34 IDP ZyWALL USG 100 200 Series User s Guide 639 ...
Page 640: ...Chapter 34 IDP ZyWALL USG 100 200 Series User s Guide 640 ...
Page 661: ...Chapter 35 ADP ZyWALL USG 100 200 Series User s Guide 661 ...
Page 662: ...Chapter 35 ADP ZyWALL USG 100 200 Series User s Guide 662 ...
Page 694: ...Chapter 37 Content Filter Reports ZyWALL USG 100 200 Series User s Guide 694 ...
Page 712: ...Chapter 38 Anti Spam ZyWALL USG 100 200 Series User s Guide 712 ...
Page 734: ...Chapter 39 Device HA ZyWALL USG 100 200 Series User s Guide 734 ...
Page 750: ...Chapter 40 User Group ZyWALL USG 100 200 Series User s Guide 750 ...
Page 756: ...Chapter 41 Addresses ZyWALL USG 100 200 Series User s Guide 756 ...
Page 768: ...Chapter 43 Schedules ZyWALL USG 100 200 Series User s Guide 768 ...
Page 784: ...Chapter 45 Authentication Method ZyWALL USG 100 200 Series User s Guide 784 ...
Page 806: ...Chapter 46 Certificates ZyWALL USG 100 200 Series User s Guide 806 ...
Page 818: ...Chapter 48 SSL Application ZyWALL USG 100 200 Series User s Guide 818 ...
Page 828: ...Chapter 49 Endpoint Security ZyWALL USG 100 200 Series User s Guide 828 ...
Page 880: ...Chapter 50 System ZyWALL USG 100 200 Series User s Guide 880 ...
Page 920: ...Chapter 54 Reboot ZyWALL USG 100 200 Series User s Guide 920 ...
Page 922: ...Chapter 55 Shutdown ZyWALL USG 100 200 Series User s Guide 922 ...
Page 942: ...Chapter 56 Troubleshooting ZyWALL USG 100 200 Series User s Guide 942 ...
Page 954: ...Chapter 57 Product Specifications ZyWALL USG 100 200 Series User s Guide 954 ...
Page 1126: ...Appendix F Open Software Announcements ZyWALL USG 100 200 Series User s Guide 1126 ...