Chapter 21 IPSec VPN
USG20(W)-VPN Series User’s Guide
342
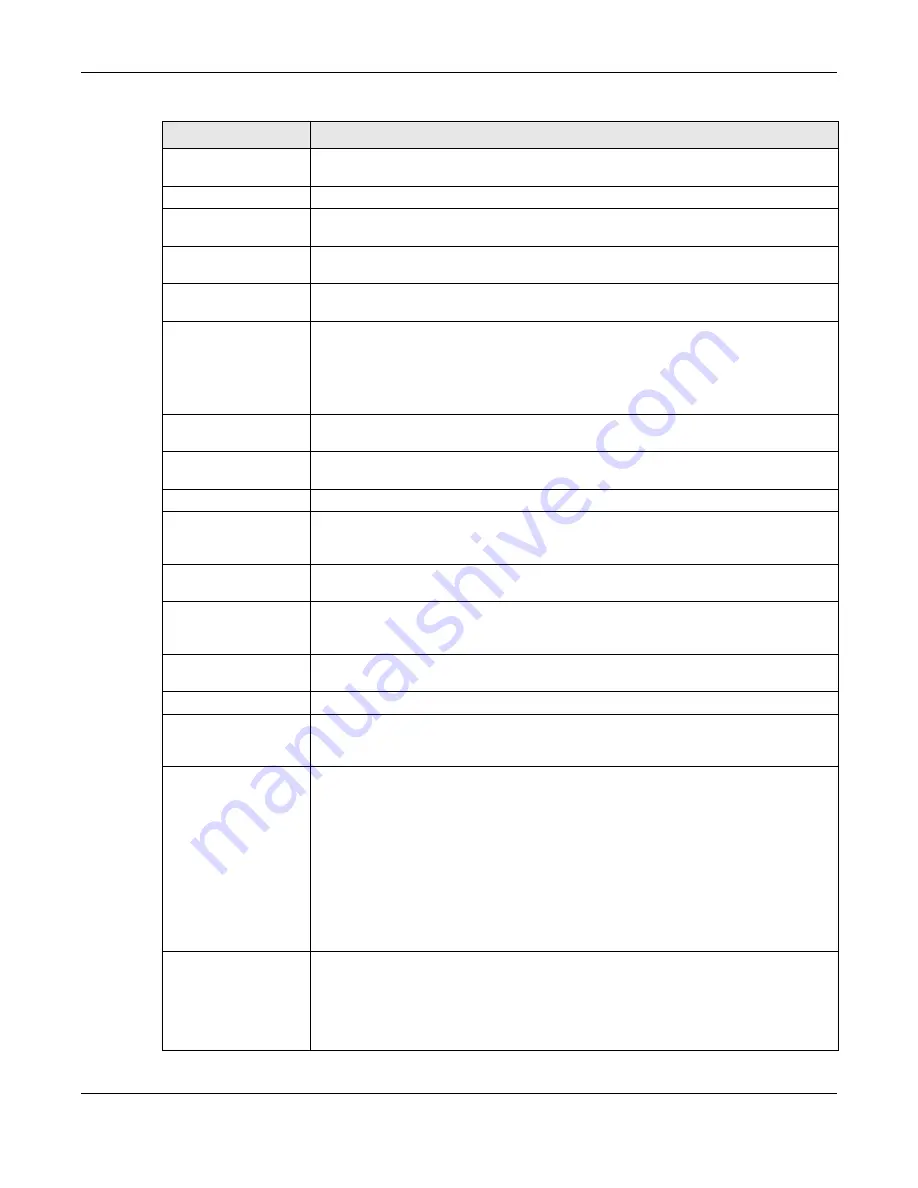
VPN Gateway
Select the VPN gateway this VPN connection is to use or select
Create Object
to add
another VPN gateway for this VPN connection to use.
Policy
Local Policy
Select the address corresponding to the local network. Use
Create new Object
if
you need to configure a new one.
Remote Policy
Select the address corresponding to the remote network. Use
Create new Object
if
you need to configure a new one.
Enable GRE over
IPSec
Select this to allow traffic using the Generic Routing Encapsulation (GRE) tunneling
protocol through an IPSec tunnel.
Policy Enforcement Clear this to allow traffic with source and destination IP addresses that do not match
the local and remote policy to use the VPN tunnel. Leave this cleared for free access
between the local and remote networks.
Selecting this restricts who can use the VPN tunnel. The USG drops traffic with source
and destination IP addresses that do not match the local and remote policy.
Configuration Payload
This is only available when you have created an IKEv2 Gateway and are using
Remote Access (Server Role)
.
Enable Configuration
Payload
Select this to have at least have the IP address pool included in the VPN setup data.
IP Address Pool:
Select an address object from the drop-down list box.
First DNS Server
(optional)
The Domain Name System (DNS) maps a domain name to an IP address and vice
versa. The USG uses these (in the order you specify here) to resolve domain names
for VPN. Enter a DNS server's IP address.
Second DNS
Server (Optional)
Enter a secondary DNS server's IP address that is checked if the first one is
unavailable.
First WINS Server
(Optional)
Type the IP address of the WINS (Windows Internet Naming Service) server that you
want to send to the DHCP clients. The WINS server keeps a mapping table of the
computer names on your network and the IP addresses that they are currently using.
Second WINS
Server (Optional)
Enter a secondary WINS server's IP address that is checked if the first one is
unavailable.
Phase 2 Settings
SA Life Time
Type the maximum number of seconds the IPSec SA can last. Shorter life times
provide better security. The USG automatically negotiates a new IPSec SA before the
current one expires, if there are users who are accessing remote resources.
Active Protocol
Select which protocol you want to use in the IPSec SA. Choices are:
AH
(RFC 2402) - provides integrity, authentication, sequence integrity (replay
resistance), and non-repudiation but not encryption. If you select
AH
, you must
select an
Authentication
algorithm.
ESP
(RFC 2406) - provides encryption and the same services offered by
AH
, but its
authentication is weaker. If you select
ESP
, you must select an
Encryption
algorithm
and
Authentication
algorithm.
Both
AH
and
ESP
increase processing requirements and latency (delay).
The USG and remote IPSec router must use the same active protocol.
Encapsulation
Select which type of encapsulation the IPSec SA uses. Choices are
Tunnel
- this mode encrypts the IP header information and the data.
Transport
- this mode only encrypts the data.
The USG and remote IPSec router must use the same encapsulation.
Table 135
Configuration > VPN > IPSec VPN > VPN Connection > Edit (continued)
LABEL
DESCRIPTION
Summary of Contents for ZyWall USG20-VPN
Page 17: ...17 PART I User s Guide ...
Page 18: ...18 ...
Page 99: ...99 PART II Technical Reference ...
Page 100: ...100 ...