Chapter 29 Object
USG20(W)-VPN Series User’s Guide
528
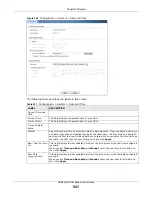
29.10.4.2 The Trusted Certificates Import Screen
Click
Configuration > Object > Certificate > Trusted Certificates > Import
to open the
Trusted Certificates Import
screen. Follow the instructions in this screen to save a trusted
certificate to the USG.
Note: You must remove any spaces from the certificate’s filename before you can import
the certificate.
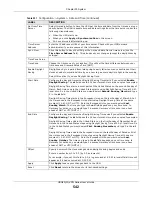
Issuer
This field displays identifying information about the certificate’s issuing certification
authority, such as Common Name, Organizational Unit, Organization and Country.
With self-signed certificates, this is the same information as in the
Subject Name
field.
Signature Algorithm This field displays the type of algorithm that was used to sign the certificate. Some
certification authorities use rsa-pkcs1-sha1 (RSA public-private key encryption
algorithm and the SHA1 hash algorithm). Other certification authorities may use rsa-
pkcs1-md5 (RSA public-private key encryption algorithm and the MD5 hash algorithm).
Valid From
This field displays the date that the certificate becomes applicable. The text displays in
red and includes a Not Yet Valid! message if the certificate has not yet become
applicable.
Valid To
This field displays the date that the certificate expires. The text displays in red and
includes an Expiring! or Expired! message if the certificate is about to expire or has
already expired.
Key Algorithm
This field displays the type of algorithm that was used to generate the certificate’s key
pair (the USG uses RSA encryption) and the length of the key set in bits (1024 bits for
example).
Subject Alternative
Name
This field displays the certificate’s owner‘s IP address (IP), domain name (DNS) or e-
mail address (EMAIL).
Key Usage
This field displays for what functions the certificate’s key can be used. For example,
“DigitalSignature” means that the key can be used to sign certificates and
“KeyEncipherment” means that the key can be used to encrypt text.
Basic Constraint
This field displays general information about the certificate. For example, Subject
Type=CA means that this is a certification authority’s certificate and “Path Length
Constraint=1” means that there can only be one certification authority in the
certificate’s path.
MD5 Fingerprint
This is the certificate’s message digest that the USG calculated using the MD5
algorithm. You can use this value to verify with the certification authority (over the
phone for example) that this is actually their certificate.
SHA1 Fingerprint
This is the certificate’s message digest that the USG calculated using the SHA1
algorithm. You can use this value to verify with the certification authority (over the
phone for example) that this is actually their certificate.
Certificate
This read-only text box displays the certificate or certification request in Privacy
Enhanced Mail (PEM) format. PEM uses lowercase letters, uppercase letters and
numerals to convert a binary certificate into a printable form.
You can copy and paste the certificate into an e-mail to send to friends or colleagues or
you can copy and paste the certificate into a text editor and save the file on a
management computer for later distribution (via floppy disk for example).
Export Certificate
Click this button and then
Save
in the
File Download
screen. The
Save As
screen
opens, browse to the location that you want to use and click
Save
.
OK
Click
OK
to save your changes back to the USG. You can only change the name.
Cancel
Click
Cancel
to quit and return to the
Trusted Certificates
screen.
Table 223
Configuration > Object > Certificate > Trusted Certificates > Edit (continued)
LABEL
DESCRIPTION
Summary of Contents for ZyWall USG20-VPN
Page 17: ...17 PART I User s Guide ...
Page 18: ...18 ...
Page 99: ...99 PART II Technical Reference ...
Page 100: ...100 ...