ZyWALL 35 User’s Guide
Chapter 37 Filter Configuration
499
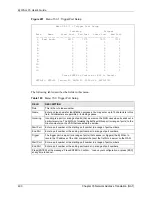
The following figure illustrates the logic flow of an IP filter.
Destination
IP Addr
Enter the destination IP Address of the packet you wish to filter. This field is ignored
if it is 0.0.0.0.
IP Mask
Enter the IP mask to apply to the
Destination: IP Addr
.
Port #
Enter the destination port of the packets that you wish to filter. The range of this field
is 0 to 65535. This field is ignored if it is 0.
Port # Comp
Press [SPACE BAR] and then [ENTER] to select the comparison to apply to the
destination port in the packet against the value given
in Destination: Port #
.
Options are
None
,
Equal
,
Not Equal
,
Less
and
Greater
.
Source
IP Addr
Enter the source IP Address of the packet you wish to filter. This field is ignored if it
is 0.0.0.0.
IP Mask
Enter the IP mask to apply to the
Source: IP Addr
.
Port #
Enter the source port of the packets that you wish to filter. The range of this field is 0
to 65535. This field is ignored if it is 0.
Port # Comp
Press [SPACE BAR] and then [ENTER] to select the comparison to apply to the
source port in the packet against the value given in
Source: Port #
.
Options are
None
,
Equal
,
Not Equal
,
Less
and
Greater
.
TCP Estab
This field is applicable only when the IP Protocol field is 6, TCP. Press [SPACE
BAR] and then [ENTER] to select
Yes
, to have the rule match packets that want to
establish a TCP connection (SYN=1 and ACK=0); if
No
, it is ignored.
More
Press [SPACE BAR] and then [ENTER] to select
Yes
or
No
. If
Yes
, a matching
packet is passed to the next filter rule before an action is taken; if
No
, the packet is
disposed of according to the action fields.
If
More
is
Yes
, then
Action Matched
and
Action Not Matched
will be
N/A
.
Log
Press [SPACE BAR] and then [ENTER] to select a logging option from the following:
None
– No packets will be logged.
Action Matched
- Only packets that match the rule parameters will be logged.
Action Not Matched
- Only packets that do not match the rule parameters will be
logged.
Both
– All packets will be logged.
Action Matched
Press [SPACE BAR] and then [ENTER] to select the action for a matching packet.
Options are
Check Next Rule
,
Forward
and
Drop
.
Action Not
Matched
Press [SPACE BAR] and then [ENTER] to select the action for a packet not
matching the rule.
Options are
Check Next Rule
,
Forward
and
Drop
.
When you have
Menu 21.1.1.1 - TCP/IP Filter Rule
configured, press [ENTER] at the message “Press
ENTER to Confirm” to save your configuration, or press [ESC] to cancel. This data will now be
displayed on
Menu 21.1.1 - Filter Rules Summary
.
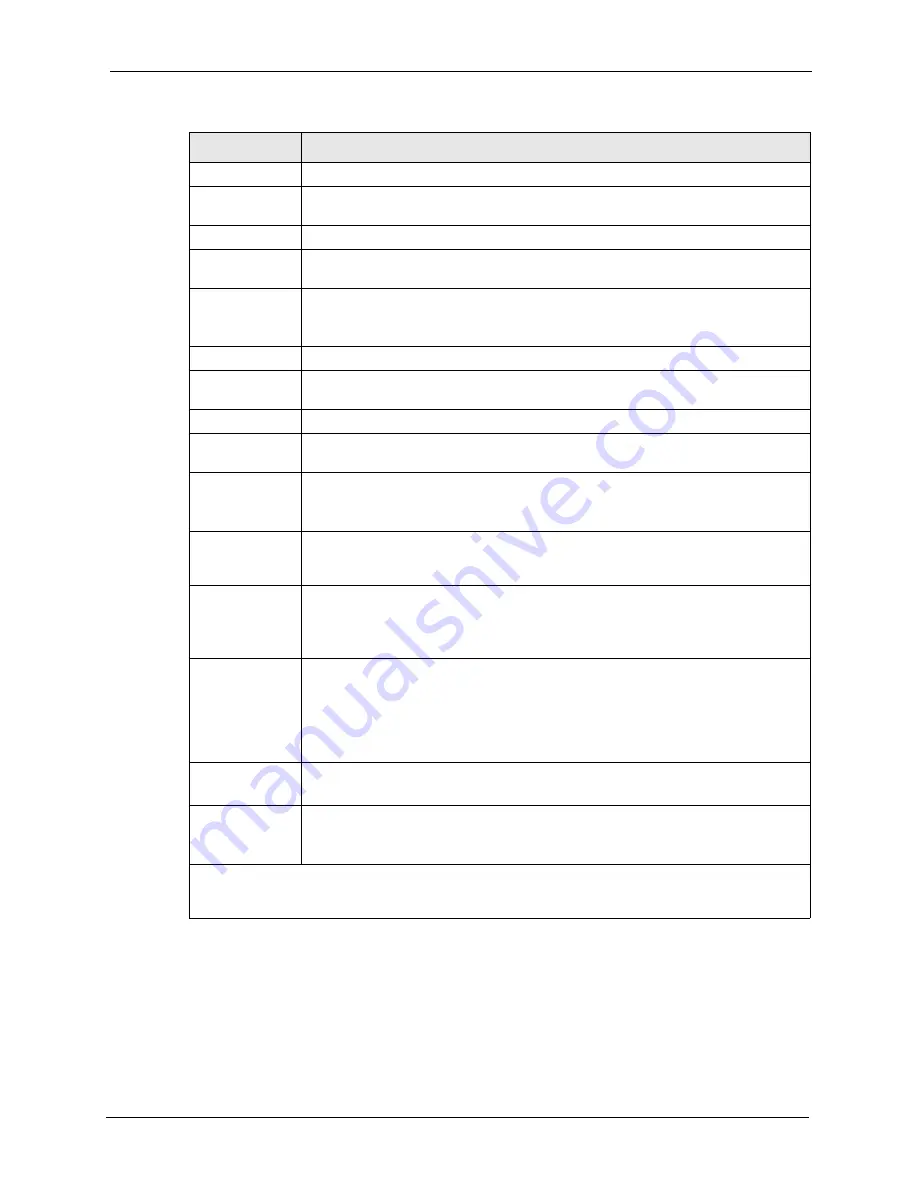
Table 193
Menu 21.1.1.1: TCP/IP Filter Rule
FIELD
DESCRIPTION
Summary of Contents for ZyXEL ZyWALL 35
Page 1: ...ZyWALL 35 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Page 2: ......
Page 38: ...ZyWALL 35 User s Guide 36 ...
Page 46: ...ZyWALL 35 User s Guide 44 ...
Page 74: ...ZyWALL 35 User s Guide 72 Chapter 2 Introducing the Web Configurator ...
Page 90: ...ZyWALL 35 User s Guide 88 Chapter 3 Wizard Setup ...
Page 100: ...ZyWALL 35 User s Guide 98 Chapter 4 LAN Screens ...
Page 106: ...ZyWALL 35 User s Guide 104 Chapter 5 Bridge Screens ...
Page 128: ...ZyWALL 35 User s Guide 126 Chapter 6 Wireless LAN ...
Page 135: ...ZyWALL 35 User s Guide Chapter 7 WAN Screens 133 Figure 47 General ...
Page 152: ...ZyWALL 35 User s Guide 150 Chapter 7 WAN Screens Figure 57 Dial Backup Setup ...
Page 158: ...ZyWALL 35 User s Guide 156 Chapter 7 WAN Screens ...
Page 166: ...ZyWALL 35 User s Guide 164 Chapter 8 DMZ Screens ...
Page 234: ...ZyWALL 35 User s Guide 232 Chapter 13 Introduction to IPSec ...
Page 275: ...ZyWALL 35 User s Guide Chapter 15 Certificates 273 Figure 129 My Certificate Details ...
Page 294: ...ZyWALL 35 User s Guide 292 Chapter 16 Authentication Server Figure 140 Local User Database ...
Page 314: ...ZyWALL 35 User s Guide 312 Chapter 17 Network Address Translation NAT ...
Page 318: ...ZyWALL 35 User s Guide 316 Chapter 18 Static Route ...
Page 324: ...ZyWALL 35 User s Guide 322 Chapter 19 Policy Route ...
Page 340: ...ZyWALL 35 User s Guide 338 Chapter 20 Bandwidth Management ...
Page 376: ...ZyWALL 35 User s Guide 374 Chapter 22 Remote Management ...
Page 390: ...ZyWALL 35 User s Guide 388 Chapter 24 Logs Screens Figure 198 Log Settings ...
Page 413: ...ZyWALL 35 User s Guide Chapter 25 Maintenance 411 Figure 220 Restart Screen ...
Page 414: ...ZyWALL 35 User s Guide 412 Chapter 25 Maintenance ...
Page 440: ...ZyWALL 35 User s Guide 438 Chapter 28 WAN and Dial Backup Setup ...
Page 456: ...ZyWALL 35 User s Guide 454 Chapter 31 DMZ Setup ...
Page 460: ...ZyWALL 35 User s Guide 458 Chapter 32 Route Setup ...
Page 470: ...ZyWALL 35 User s Guide 468 Chapter 33 Remote Node Setup ...
Page 522: ...ZyWALL 35 User s Guide 520 Chapter 39 System Information Diagnosis ...
Page 538: ...ZyWALL 35 User s Guide 536 Chapter 40 Firmware and Configuration File Maintenance ...
Page 550: ...ZyWALL 35 User s Guide 548 Chapter 42 Remote Management ...
Page 558: ...ZyWALL 35 User s Guide 556 Chapter 43 IP Policy Routing ...
Page 574: ...ZyWALL 35 User s Guide 572 Chapter 45 Troubleshooting Figure 364 Java Sun ...
Page 602: ...ZyWALL 35 User s Guide 600 Appendix C IP Subnetting ...
Page 608: ...ZyWALL 35 User s Guide 606 Appendix E PPTP ...
Page 626: ...ZyWALL 35 User s Guide 624 Appendix G Triangle Route ...
Page 656: ...ZyWALL 35 User s Guide 654 Appendix J Importing Certificates ...
Page 658: ...ZyWALL 35 User s Guide 656 Appendix K Command Interpreter ...
Page 664: ...ZyWALL 35 User s Guide 662 Appendix L Firewall Commands ...
Page 668: ...ZyWALL 35 User s Guide 666 Appendix M NetBIOS Filter Commands ...
Page 674: ...ZyWALL 35 User s Guide 672 Appendix O Brute Force Password Guessing Protection ...
Page 696: ...ZyWALL 35 User s Guide 694 Appendix Q Log Descriptions ...