ZyWALL 35 User’s Guide
Chapter 24 Logs Screens
387
The following is an example of how a log displays in the command line interpreter and a
description of the sample log. Refer to the appendices for more log message descriptions and
details on using the command line interpreter to display logs.
# .time source destination
notes
message
5|06/08/2004 05:58:20 |172.21.4.187:137 |172.21.255.255:137
|ACCESS BLOCK
Firewall default policy: UDP (W to W/ZW)
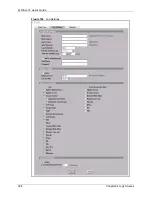
24.3 Configuring Log Settings
To change your ZyWALL’s log settings, click
LOGS
, then the
Log Settings
tab. The screen
appears as shown.
Use the
Log
Settings
screen to configure to where the ZyWALL is to send logs; the schedule
for when the ZyWALL is to send the logs and which logs and/or immediate alerts the
ZyWALL is to send.
An alert is a type of log that warrants more serious attention. They include system errors,
attacks (access control) and attempted access to blocked web sites or web sites with restricted
web features such as cookies, active X and so on. Some categories such as
System Errors
consist of both logs and alerts. You may differentiate them by their color in the
View Log
screen. Alerts display in red and logs display in black.
Note:
Alerts are e-mailed as soon as they happen. Logs may be e-mailed as soon as
the log is full (see
Log Schedule
). Selecting many alert and/or log categories
(especially
Access Control
) may result in many e-mails being sent.
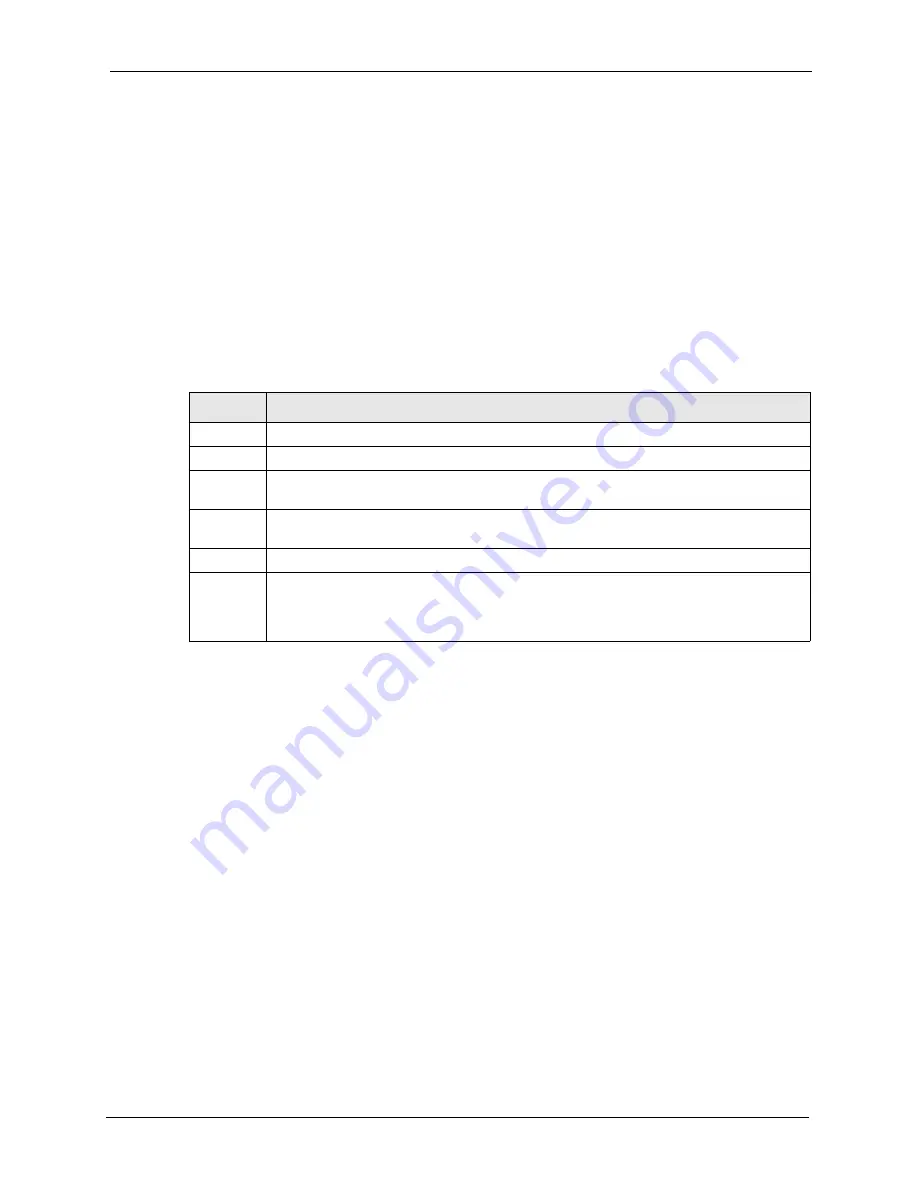
Table 137
Example Log Description
LABEL
DESCRIPTION
#
This is log number five.
time
The log was generated on June 8, 2004 at 5:58 and 20 seconds AM.
source
The log was generated due to a NetBIOS packet sent from IP address 172.21.4.187 port
137.
destination The NetBIOS packet was sent to the 172.21.255.255 subnet port 137. This was a
NetBIOS UDP broadcast packet meant to discover devices on the network.
notes
The ZyWALL blocked the packet.
message
The ZyWALL blocked the packet in accordance with the firewall’s default policy of blocking
sessions that are initiated from the WAN. “UDP” means that this was a User Datagram
Protocol packet. “W to W/ZW” indicates that the packet was traveling from the WAN to the
WAN or the ZyWALL.
Summary of Contents for ZyXEL ZyWALL 35
Page 1: ...ZyWALL 35 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Page 2: ......
Page 38: ...ZyWALL 35 User s Guide 36 ...
Page 46: ...ZyWALL 35 User s Guide 44 ...
Page 74: ...ZyWALL 35 User s Guide 72 Chapter 2 Introducing the Web Configurator ...
Page 90: ...ZyWALL 35 User s Guide 88 Chapter 3 Wizard Setup ...
Page 100: ...ZyWALL 35 User s Guide 98 Chapter 4 LAN Screens ...
Page 106: ...ZyWALL 35 User s Guide 104 Chapter 5 Bridge Screens ...
Page 128: ...ZyWALL 35 User s Guide 126 Chapter 6 Wireless LAN ...
Page 135: ...ZyWALL 35 User s Guide Chapter 7 WAN Screens 133 Figure 47 General ...
Page 152: ...ZyWALL 35 User s Guide 150 Chapter 7 WAN Screens Figure 57 Dial Backup Setup ...
Page 158: ...ZyWALL 35 User s Guide 156 Chapter 7 WAN Screens ...
Page 166: ...ZyWALL 35 User s Guide 164 Chapter 8 DMZ Screens ...
Page 234: ...ZyWALL 35 User s Guide 232 Chapter 13 Introduction to IPSec ...
Page 275: ...ZyWALL 35 User s Guide Chapter 15 Certificates 273 Figure 129 My Certificate Details ...
Page 294: ...ZyWALL 35 User s Guide 292 Chapter 16 Authentication Server Figure 140 Local User Database ...
Page 314: ...ZyWALL 35 User s Guide 312 Chapter 17 Network Address Translation NAT ...
Page 318: ...ZyWALL 35 User s Guide 316 Chapter 18 Static Route ...
Page 324: ...ZyWALL 35 User s Guide 322 Chapter 19 Policy Route ...
Page 340: ...ZyWALL 35 User s Guide 338 Chapter 20 Bandwidth Management ...
Page 376: ...ZyWALL 35 User s Guide 374 Chapter 22 Remote Management ...
Page 390: ...ZyWALL 35 User s Guide 388 Chapter 24 Logs Screens Figure 198 Log Settings ...
Page 413: ...ZyWALL 35 User s Guide Chapter 25 Maintenance 411 Figure 220 Restart Screen ...
Page 414: ...ZyWALL 35 User s Guide 412 Chapter 25 Maintenance ...
Page 440: ...ZyWALL 35 User s Guide 438 Chapter 28 WAN and Dial Backup Setup ...
Page 456: ...ZyWALL 35 User s Guide 454 Chapter 31 DMZ Setup ...
Page 460: ...ZyWALL 35 User s Guide 458 Chapter 32 Route Setup ...
Page 470: ...ZyWALL 35 User s Guide 468 Chapter 33 Remote Node Setup ...
Page 522: ...ZyWALL 35 User s Guide 520 Chapter 39 System Information Diagnosis ...
Page 538: ...ZyWALL 35 User s Guide 536 Chapter 40 Firmware and Configuration File Maintenance ...
Page 550: ...ZyWALL 35 User s Guide 548 Chapter 42 Remote Management ...
Page 558: ...ZyWALL 35 User s Guide 556 Chapter 43 IP Policy Routing ...
Page 574: ...ZyWALL 35 User s Guide 572 Chapter 45 Troubleshooting Figure 364 Java Sun ...
Page 602: ...ZyWALL 35 User s Guide 600 Appendix C IP Subnetting ...
Page 608: ...ZyWALL 35 User s Guide 606 Appendix E PPTP ...
Page 626: ...ZyWALL 35 User s Guide 624 Appendix G Triangle Route ...
Page 656: ...ZyWALL 35 User s Guide 654 Appendix J Importing Certificates ...
Page 658: ...ZyWALL 35 User s Guide 656 Appendix K Command Interpreter ...
Page 664: ...ZyWALL 35 User s Guide 662 Appendix L Firewall Commands ...
Page 668: ...ZyWALL 35 User s Guide 666 Appendix M NetBIOS Filter Commands ...
Page 674: ...ZyWALL 35 User s Guide 672 Appendix O Brute Force Password Guessing Protection ...
Page 696: ...ZyWALL 35 User s Guide 694 Appendix Q Log Descriptions ...