ZyWALL 5 User’s Guide
126
Chapter 7 WAN Screens
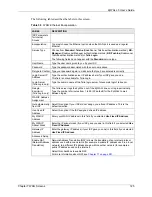
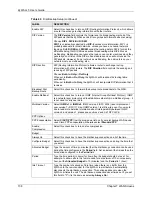
RIP Direction
RIP (Routing Information Protocol) allows a router to exchange routing information
with other routers. The
RIP Direction
field controls the sending and receiving of
RIP packets.
Choose
Both
,
None
,
In Only
or
Out Only
.
When set to
Both
or
Out Only
, the ZyWALL will broadcast its routing table
periodically.
When set to
Both
or
In Only
, the ZyWALL will incorporate RIP information that it
receives.
When set to
None
, the ZyWALL will not send any RIP packets and will ignore any
RIP packets received.
By default,
RIP Direction
is set to
Both
.
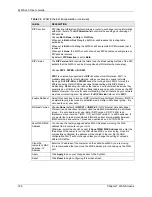
RIP Version
The
RIP Version
field controls the format and the broadcasting method of the RIP
packets that the ZyWALL sends (it recognizes both formats when receiving).
Choose
RIP-1
,
RIP-2B
or
RIP-2M
.
RIP-1
is universally supported; but
RIP-2
carries more information. RIP-1 is
probably adequate for most networks, unless you have an unusual network
topology. Both
RIP-2B
and
RIP-2M
sends the routing data in RIP-2 format; the
difference being that RIP-2B uses subnet broadcasting while RIP-2M uses
multicasting. Multicasting can reduce the load on non-router machines since they
generally do not listen to the RIP multicast address and so will not receive the RIP
packets. However, if one router uses multicasting, then all routers on your network
must use multicasting, also. By default, the
RIP Version
field is set to
RIP-1
.
Enable Multicast
Select this check box to turn on IGMP (Internet Group Multicast Protocol). IGMP is
a network-layer protocol used to establish membership in a Multicast group - it is
not used to carry user data.
Multicast Version
Choose
None
(default),
IGMP-V1
or
IGMP-V2
. IGMP (Internet Group Multicast
Protocol) is a session-layer protocol used to establish membership in a Multicast
group – it is not used to carry user data. IGMP version 2 (RFC 2236) is an
improvement over version 1 (RFC 1112) but IGMP version 1 is still in wide use. If
you would like to read more detailed information about interoperability between
IGMP version 2 and version 1, please see sections 4 and 5 of RFC 2236.
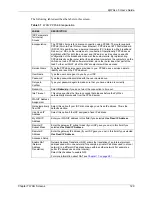
Spoof WAN MAC
Address
You can use the factory assigned default MAC Address or cloning the MAC
address from a computer on your LAN.
Otherwise,
select the check box next to
Spoof WAN MAC Address
and enter the
IP address of the computer on the LAN whose MAC you are cloning. Once it is
successfully configured, the address will be copied to the rom file (ZyNOS
configuration file). It will not change unless you change the setting or upload a
different ROM file.
Clone the
computer’s MAC
address – IP
Address
Enter the IP address of the computer on the LAN whose MAC you are cloning.
It is recommended that you clone the MAC address prior to hooking up the WAN
port.
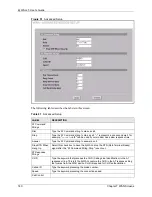
Apply
Click
Apply
to save your changes back to the ZyWALL.
Reset
Click
Reset
to begin configuring this screen afresh.
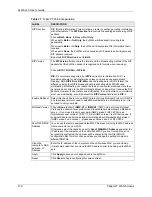
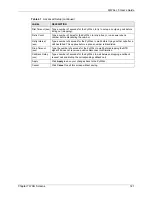
Table 36
WAN: Ethernet Encapsulation (continued)
LABEL
DESCRIPTION
Summary of Contents for ZyXEL ZyWALL 5
Page 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Page 2: ......
Page 26: ...ZyWALL 5 User s Guide 24 ...
Page 44: ...ZyWALL 5 User s Guide 42 ...
Page 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Page 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Page 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
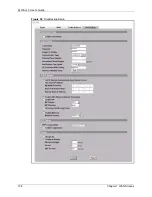
Page 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Page 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Page 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Page 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Page 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Page 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Page 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Page 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Page 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Page 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Page 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Page 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Page 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Page 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Page 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Page 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Page 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Page 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Page 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Page 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Page 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Page 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Page 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Page 571: ...ZyWALL 5 User s Guide 569 ...
Page 572: ...ZyWALL 5 User s Guide 570 ...
Page 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
Page 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Page 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Page 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Page 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Page 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Page 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...