ZyWALL 5 User’s Guide
Chapter 14 VPN Screens
233
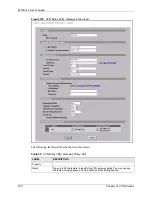
Content
The configuration of the peer content depends on the peer ID type.
Do the following when you set
Authentication Key
to
Pre-shared Key
.
•
For
IP
, type the IP address of the computer with which you will make the VPN
connection. If you configure this field to
0.0.0.0
or leave it blank, the ZyWALL
will use the address in the
Remote Gateway Address
field (refer to the
Remote Gateway Address
field description).
•
For
DNS
or
, type a domain name or e-mail address by which to identify
the remote IPSec router. Use up to 31 ASCII characters including spaces,
although trailing spaces are truncated. The domain name or e-mail address is
for identification purposes only and can be any string.
It is recommended that you type an IP address other than
0.0.0.0
or use the
DNS
or
ID type in the following situations:
•
When there is a NAT router between the two IPSec routers.
•
When you want the ZyWALL to distinguish between VPN connection requests
that come in from remote IPSec routers with dynamic WAN IP addresses.
Do the following when you set
Authentication Key
to
Certificate
.
•
For
IP
, type the IP address from the subject alternative name field of the
certificate the remote IPSec router will use for this VPN connection. If you
configure this field to
0.0.0.0
or leave it blank, the ZyWALL will use the
address in the
Remote Gateway Address
field (refer to the
Remote
Gateway Address
field description).
•
For
DNS
or
, type the domain name or e-mail address from the subject
alternative name field of the certificate the remote IPSec router will use for this
VPN connection.
•
For
Subject Name
, type the subject name of the certificate the remote IPSec
router will use for this VPN connection. Use up to255 ASCII characters
including spaces.
•
For
Any
, the peer
Content
field is not available.
•
Regardless of how you configure the
ID Type
and
Content
fields, two active
SAs cannot have both the local and remote IP address ranges overlap
between rules.
Extended
Authentication
Enable Extended
Authentication
Select this check box to activate extended authentication.
Server Mode
Select
Server Mode
to have this ZyWALL authenticate extended authentication
clients that request this VPN connection.
You must also configure the extended authentication clients’ usernames and
passwords in the authentication server’s local user database or a RADIUS server
Click
Local User
to go to the
Local User Database
screen where you can view
and/or edit the list of user names and passwords. Click
RADIUS
to go to the
RADIUS
screen where you can configure the ZyWALL to check an external
RADIUS server.
During authentication, if the ZyWALL (in server mode) does not find the extended
authentication clients’ user name in its internal user database and an external
RADIUS server has been enabled, it attempts to authenticate the client through
the RADIUS server.
Client Mode
Select
Client Mode
to have your ZyWALL use a username and password when
initiating this VPN connection to the extended authentication server ZyWALL.
Only a VPN extended authentication client can initiate this VPN connection.
Table 68
VPN Rules (IKE): Gateway Policy: Edit (continued)
LABEL
DESCRIPTION
Summary of Contents for ZyXEL ZyWALL 5
Page 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Page 2: ......
Page 26: ...ZyWALL 5 User s Guide 24 ...
Page 44: ...ZyWALL 5 User s Guide 42 ...
Page 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Page 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Page 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
Page 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Page 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Page 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Page 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Page 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Page 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Page 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Page 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Page 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Page 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Page 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Page 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Page 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Page 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Page 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Page 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Page 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Page 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Page 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Page 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Page 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Page 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Page 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Page 571: ...ZyWALL 5 User s Guide 569 ...
Page 572: ...ZyWALL 5 User s Guide 570 ...
Page 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
Page 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Page 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Page 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Page 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Page 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Page 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...