ZyWALL 5 User’s Guide
648
Appendix Q Log Descriptions
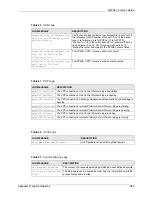
Recv <packet>
IKE uses ISAKMP to transmit data. Each ISAKMP packet
contains many different types of payloads. All of them show in
the LOG. Refer to RFC2408 – ISAKMP for a list of all ISAKMP
payload types.
Recv <Main or Aggressive>
Mode request from <IP>
The router received an IKE negotiation request from the peer
address specified.
Send <Main or Aggressive>
Mode request to <IP>
The router started negotiation with the peer.
Invalid IP <Peer local> /
<Peer local>
The peer’s “Local IP Address” is invalid.
Remote IP <Remote IP> /
<Remote IP> conflicts
The security gateway is set to “0.0.0.0” and the router used
the peer’s “Local Address” as the router’s “Remote Address”.
This information conflicted with static rule #d; thus the
connection is not allowed.
Phase 1 ID type mismatch
This router’s "Peer ID Type" is different from the peer IPSec
router's "Local ID Type".
Phase 1 ID content mismatch
This router’s "Peer ID Content" is different from the peer
IPSec router's "Local ID Content".
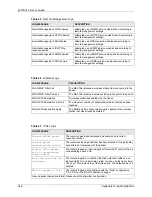
No known phase 1 ID type
found
The router could not find a known phase 1 ID in the
connection attempt.
ID type mismatch. Local /
Peer: <Local ID type/Peer ID
type>
The phase 1 ID types do not match.
ID content mismatch
The phase 1 ID contents do not match.
Configured Peer ID Content:
<Configured Peer ID Content>
The phase 1 ID contents do not match and the configured
"Peer ID Content" is displayed.
Incoming ID Content:
<Incoming Peer ID Content>
The phase 1 ID contents do not match and the incoming
packet's ID content is displayed.
Unsupported local ID Type:
<%d>
The phase 1 ID type is not supported by the router.
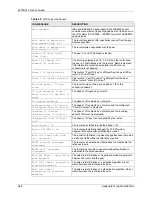
Build Phase 1 ID
The router has started to build the phase 1 ID.
Adjust TCP MSS to %d
The router automatically changed the TCP Maximum
Segment Size value after establishing a tunnel.
Rule <%d> input idle time
out, disconnect
The tunnel for the listed rule was dropped because there was
no inbound traffic within the idle timeout period.
XAUTH succeed! Username:
<Username>
The router used extended authentication to authenticate the
listed username.
XAUTH fail! Username:
<Username>
The router was not able to use extended authentication to
authenticate the listed username.
Rule[%d] Phase 1 negotiation
mode mismatch
The listed rule’s IKE phase 1 negotiation mode did not match
between the router and the peer.
Rule [%d] Phase 1 encryption
algorithm mismatch
The listed rule’s IKE phase 1 encryption algorithm did not
match between the router and the peer.
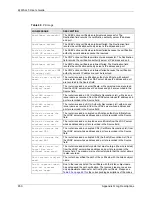
Rule [%d] Phase 1
authentication algorithm
mismatch
The listed rule’s IKE phase 1 authentication algorithm did not
match between the router and the peer.
Table 48
IKE Logs (continued)
LOG MESSAGE
DESCRIPTION
Summary of Contents for ZyXEL ZyWALL 5
Page 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Page 2: ......
Page 26: ...ZyWALL 5 User s Guide 24 ...
Page 44: ...ZyWALL 5 User s Guide 42 ...
Page 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Page 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Page 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
Page 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Page 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Page 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Page 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Page 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Page 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Page 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Page 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Page 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Page 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Page 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Page 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Page 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Page 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Page 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Page 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Page 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Page 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Page 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Page 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Page 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Page 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Page 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Page 571: ...ZyWALL 5 User s Guide 569 ...
Page 572: ...ZyWALL 5 User s Guide 570 ...
Page 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
Page 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Page 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Page 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Page 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Page 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Page 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...