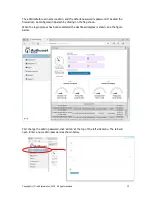
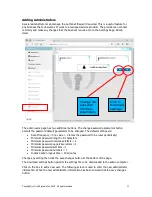
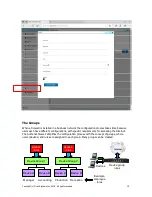
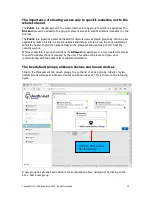
Reviews:
No comments
Related manuals for Firewall F-10

XTM 33
Brand: Watchguard Pages: 24

Firebox SOHO 6 Wireless
Brand: Watchguard Pages: 208

NetDefend DFL-800
Brand: D-Link Pages: 2

XCS 280
Brand: Watchguard Pages: 20

UTM25 - ProSecure Unified Threat Management Appliance
Brand: NETGEAR Pages: 2

UTM5 - ProSecure Unified Threat Management Appliance
Brand: NETGEAR Pages: 2

ProSecure UTM150
Brand: NETGEAR Pages: 2

ProSecure UTM25S
Brand: NETGEAR Pages: 2

ProSAFE FVS336G v3
Brand: NETGEAR Pages: 2

SRXN3205 - ProSafe Wireless-N VPN Firewall Wireless Router
Brand: NETGEAR Pages: 150

UTM10 - ProSecure Unified Threat Management Appliance
Brand: NETGEAR Pages: 480

freeGuard 100
Brand: Freedom9 Pages: 310